A concerning variant of the Mirai botnet, IZ1H9, is infiltrating Linux servers and network devices with new vigor, as per a recent analysis by Unit 42 researchers. Utilizing several vulnerabilities, IZ1H9 poses a serious threat, taking full control of compromised devices to form part of its botnet. These devices are then utilized to orchestrate further attacks, notably distributed denial-of-service (DDoS) campaigns.
Observed in action since November 2021, the Mirai IZ1H9 variant has been linked to multiple campaigns. Key indicators such as identical malware shell script downloaders, shared XOR decryption keys, and identical function usage suggest that these operations are likely the handiwork of a single threat actor.

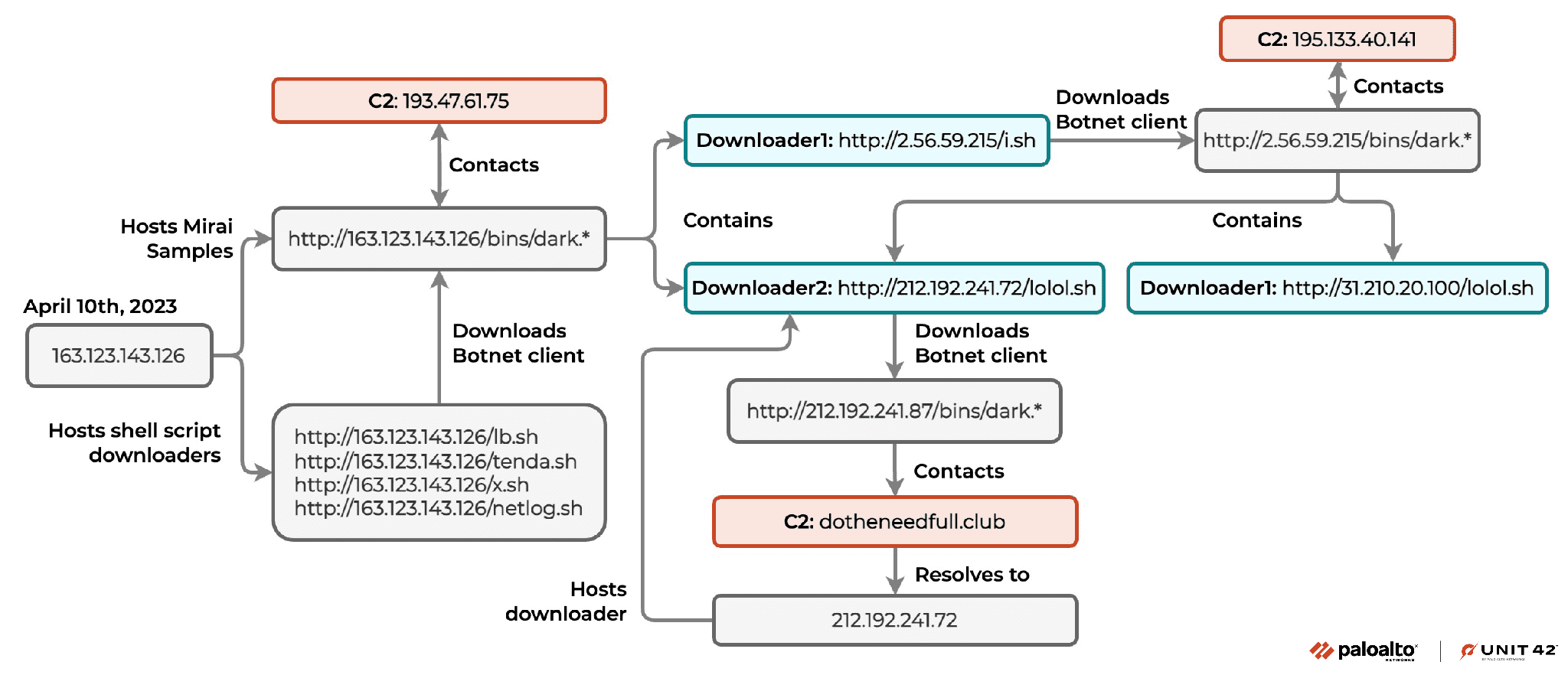
Researchers detected unusual traffic on April 10, 2023, pointing towards a shell script downloader labeled ‘lb.sh’ originating from a specific IP. If successfully executed, the downloader would proceed to eliminate logs, thereby obscuring its activities, and subsequently download bot clients adapted to various Linux architectures. In the final phase, it modifies the device’s iptable rules, disrupting network connections from several ports. This maneuver makes remote device recovery difficult for victims.
Further investigation led to the discovery of two additional URLs hosting shell script downloaders. These downloaders carried botnet clients contacting a command and control (C2) server and more URLs hosting shell scripts. The shell script downloaders were discovered downloading botnet clients from specified locations and contacting distinct C2 domains.
Upon analyzing the downloaded samples, researchers deduced that they represented a variant of the Mirai botnet, IZ1H9. Notorious since its discovery in August 2018, IZ1H9 remains one of the most active Mirai variants. Sharing many of the original Mirai’s characteristics, IZ1H9 avoids execution for a range of IP blocks, terminates other botnet processes, and attempts connection to a hardcoded C2 address.
Key to IZ1H9’s modus operandi is its use of encrypted configuration strings. To decrypt these strings, it uses an initialized encrypted string table and performs XOR decryption with the key 0xBAADF00D. Subsequently, it retrieves the encrypted strings using an index.
IZ1H9 propels its malware through HTTP, SSH, and Telnet protocols, using embedded default login credentials for scanner and brute-force attacks. The botnet also capitalizes on several remote code execution vulnerabilities to access susceptible devices and execute shellcode script downloaders. The botnet clients then establish connections with the C2 server to initialize all DDoS attack functions.
IZ1H9’s consistent activity and adaptability highlight the persistent and evolving nature of cyber threats. As such, device users and administrators should strengthen their defenses, regularly update systems, and remain vigilant for anomalies that may hint at a cyber intrusion.