Krane
Krane is a simple Kubernetes RBAC static analysis tool. It identifies potential security risks in K8s RBAC design and makes suggestions on how to mitigate them. Krane dashboard presents the current RBAC security posture and lets you navigate through its definition.
Features
- RBAC Risk rules – Krane evaluates a set of built-in RBAC risk rules. These can be modified or extended with a set of custom rules.
- Portability – Krane can run in one of the following modes:
- Locally as a CLI or docker container.
- In CI/CD pipelines as a step action detecting potential RBAC flaws before it gets applied to the cluster.
- As a standalone service continuously analysing the state of RBAC within a Kubernetes cluster.
- Reporting – Krane produces an easy-to-understand RBAC risk report in a machine-readable format.
- Dashboard – Krane comes with a simple Dashboard UI helping you understand in-cluster RBAC design. A dashboard presents a high-level overview of RBAC security posture and highlights detected risks. It also allows for further RBAC controls inspection via faceted tree and graph network views.
- Alerting – It will alert on detected medium and high severity risks via its Slack integration.
- RBAC in the Graph – Krane indexes the entirety of Kubernetes RBAC in a local Graph database which makes any further ad-hoc interrogating of RBAC data easy, with arbitrary CypherQL queries.
Architecture
RBAC Data indexed in a local Graph database
Krane indexes RBAC entities in RedisGraph. This allows us to query a network of dependencies efficiently and simply using a subset of CypherQL supported by RedisGraph.
Schema
Nodes
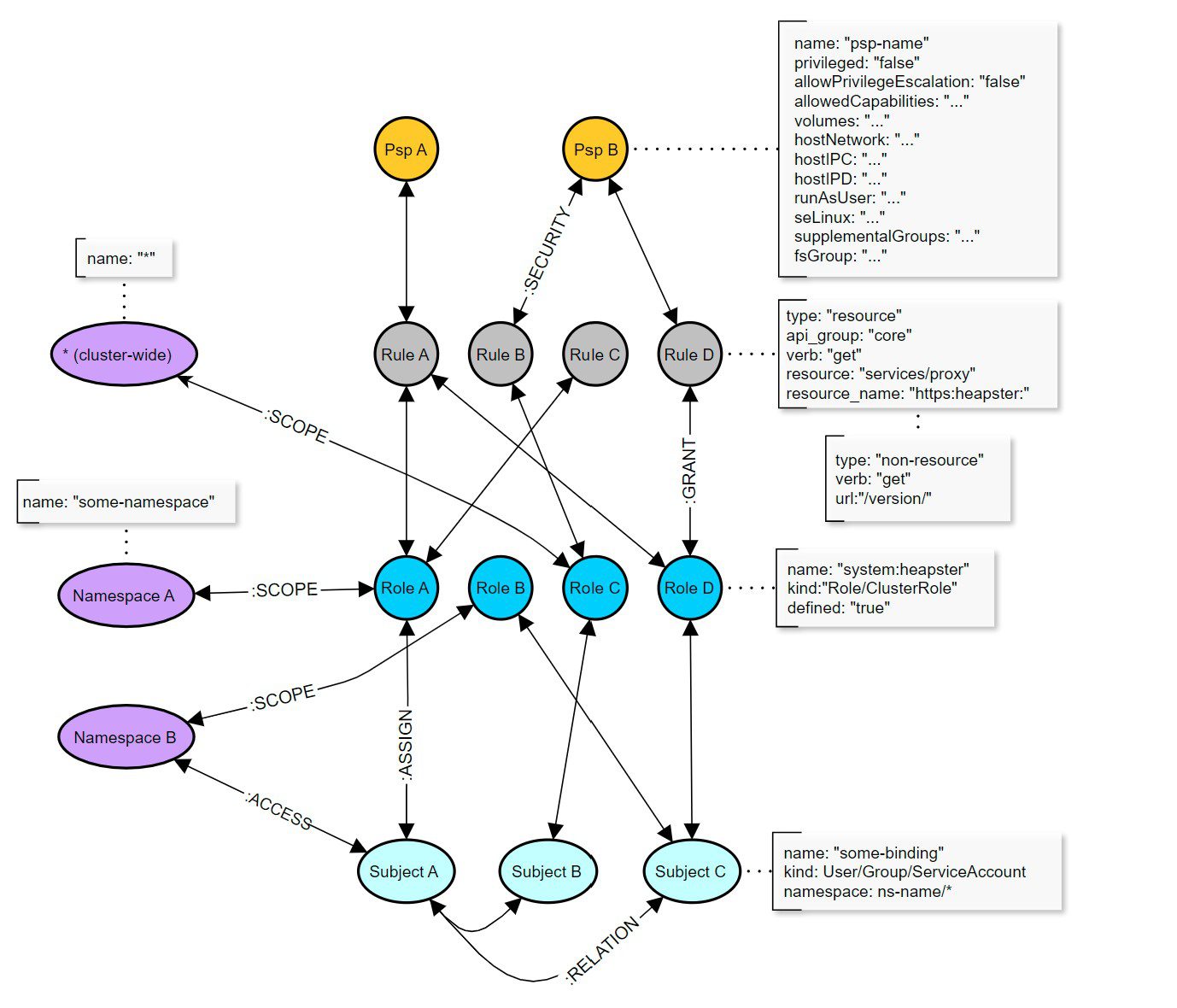
The following nodes are created in the Graph for the relevant RBAC objects:
Psp– A PSP node containing attributes around the pod security policy.Rule– Rule node represents access control rule around Kubernetes resources.Role– Role node represents a given Role or ClusterRole.kindattribute defines type of role.Subject– Subject represents all possible actors in the cluster (kind: User, Group and ServiceAccount)Namespace– Kubernetes Namespace node.
Edges
:SECURITY– Defines a link between Rule and Psp nodes.:GRANT– Defines a link between Role and Rule associated with that role.:ASSIGN– Defines a link between an Actor (Subject) and given Role/ClusterRole (Role node).:RELATION– Defines a link between two different Actor (Subject) nodes.:SCOPE– Defines a link between Role and Namespace nodes.:ACCESS– Defines a link between Subject and Namespace nodes.:AGGREGATE– Defines a link between ClusterRoles (one ClusterRole aggregates another)A-(aggregates)->B:COMPOSITE– Defines a link between ClusterRoles (one ClusterRole can be aggregated in another)A<-(is a composite of)-B
All edges are bidirectional, which means graph can be queried in either direction. Only exceptions are :AGGREGATE and :COMPOSITE relations which are uni-directional, though concerned with the same edge nodes.
Querying the Graph
In order to query the graph directly you can exec into a running redisgraph container, start redis-cli and run your arbitrary queries. Follow official instructions for examples of commands.
You can also query the Graph from Krane console. First exec into running Krane container, then
Note: The example query above will select all Subjects with assigned Roles/ClusterRoles granting access to update configmaps.
Changelog v0.1.1
This release includes a number of patches and dependency updates.
- FIX: in-cluster run – dashboard will wait for the first report to be generated before starting. #241
- FIX: Updates example default network policy #240
- Various dependencies version updates and security patches