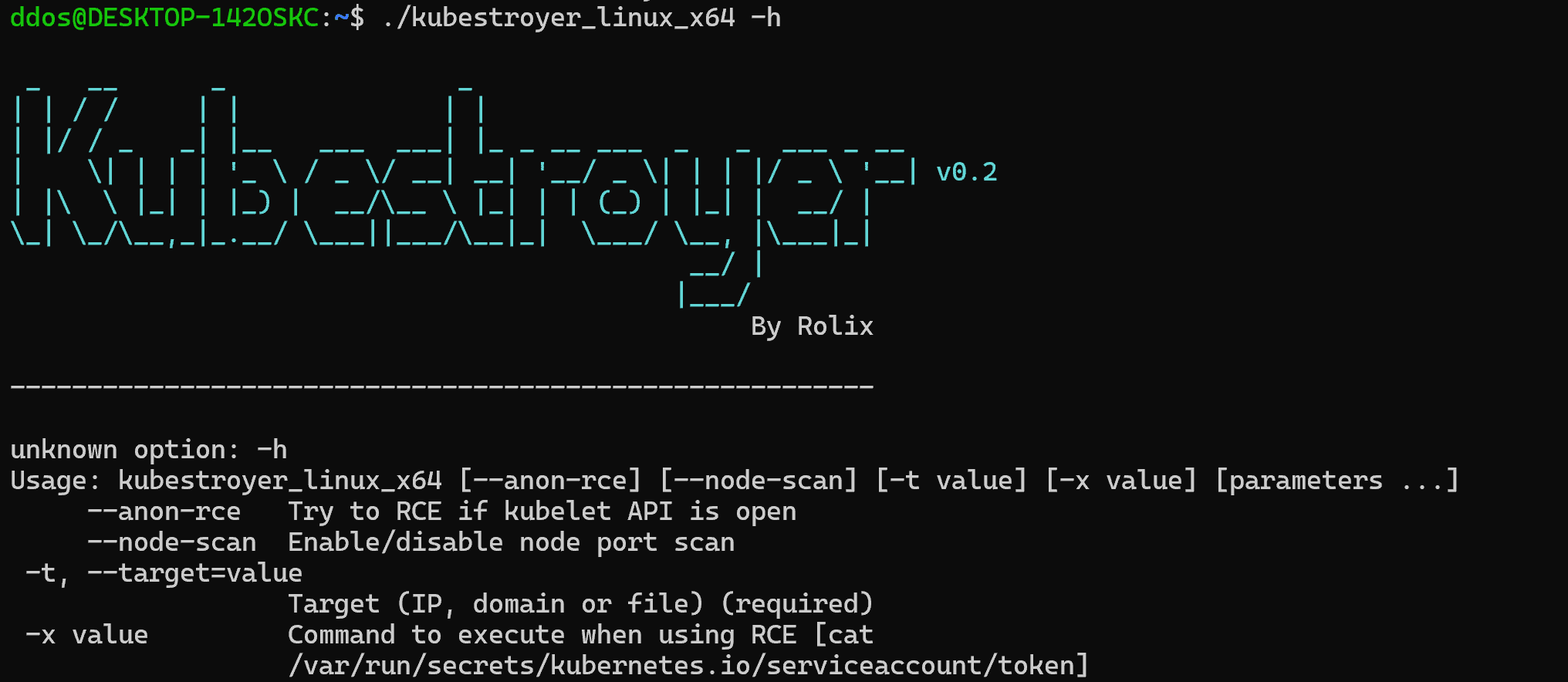
Kubestroyer
Kubestroyer aims to exploit Kubernetes clusters misconfigurations and be the swiss army knife of your Kubernetes pentests.
Kubestroyer is a Golang exploitation tool that aims to take advantage of Kubernetes clusters misconfigurations.
The tool is scanning known Kubernetes ports that can be exposed as well as exploiting them.

Roadmap
- Split main into different packages
- Target selection
- List of multiple targets
- input file as target parameter
- Description for each detected open port
- Choose the pod for anon RCE
Use
| Parameter | Description | Mand/opt | Example |
|---|---|---|---|
| -t / –target | Target (IP, domain or file) | Mandatory | -t localhost,127.0.0.1 / -t ./domain.txt |
| –node-scan | Enable node port scanning (port 30000 to 32767) | Optionnal | -t localhost –node-scan |
| –anon-rce | RCE using Kubelet API anonymous auth | Optionnal | -t localhost –anon-rce |
| -x | Command to execute when using RCE (display service account token by default) | Optionnal | -t localhost –anon-rce -x “ls -al” |
Download
Copyright (c) 2023 Rolix