LHF – Leaked Handles Finder
Leaked Windows processes handles identification tool. Useful for identifying new LPE vulnerabilities during a pentest or simply as a new research process. Currently supports exploiting (autopwn) processes leaked handles spawning a new arbitrary process (cmd.exe default).
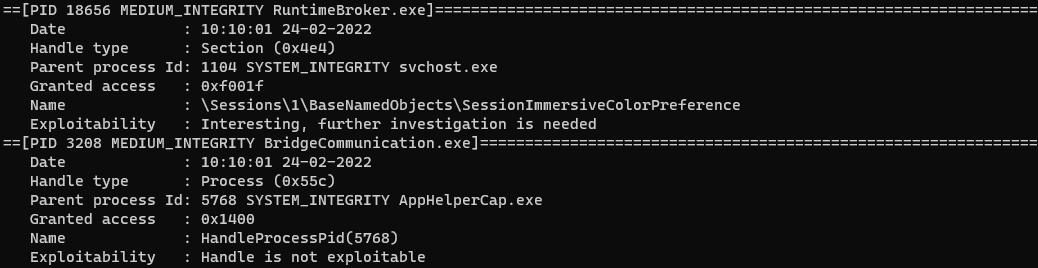
LHF identifies in real-time inherited handles and gives the researcher exploitability tips.

Use
.\LeakedHandlesFinder_x64.exe -h
__ __ __ _______
| | | | | | | ____|
| | | |__| | | |__
| | | __ | | __|
| `—-.| | | | | |
|_______||__| |__| |__|
==[Leaked Handles Finder v1.0 by @ramado78 from lab52.io]==================================
Usage : C:\Users\dvsci\Desktop\LeakedHandlesFinder_x64.exe [options]
==[Options]================================================================================
-o<file> : Write log to file
-s<type> : Suspend process when a handle type (Process, File…) is found
-a : AutoPwn, try to exploit the handle
-r : Research mode. Keep looking for leaked handles continuously
-l : Print to stdout using single line
-h : Show help
-u : Hide unnamed handles
-c<Exploit command> : Command to execute (Case process parent pid explotation)
==[Examples]===============================================================================
Loop execution research : LeakedHandlesFinder.exe -u -r -oLogFile.txt
One execution autopwn : LeakedHandlesFinder.exe -u -a