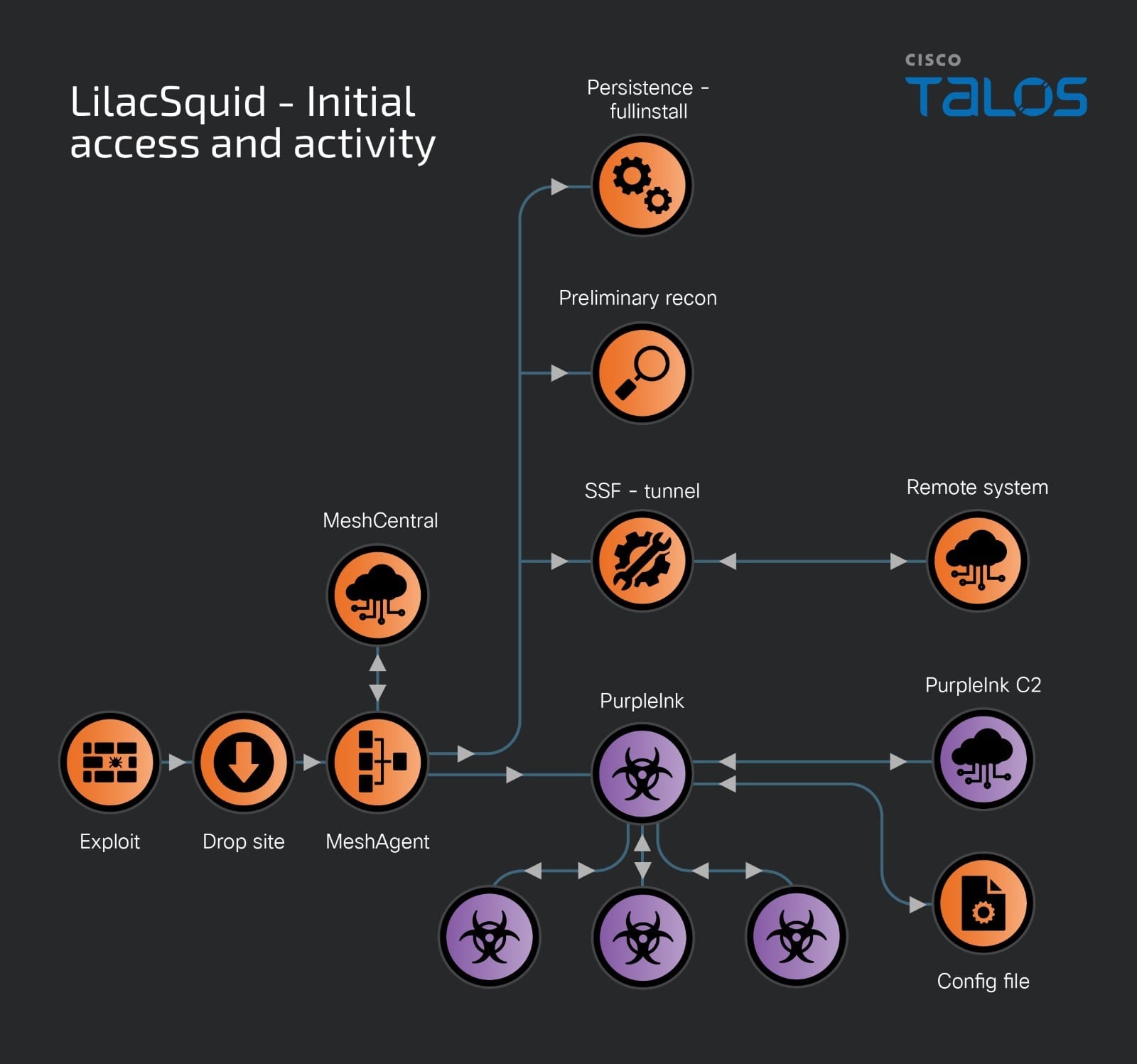
LilacSquid’s infection chains
Cisco Talos, the threat intelligence and research arm of Cisco, has exposed a sophisticated espionage-focused threat actor known as LilacSquid (UAT-4820). This advanced persistent threat (APT) group has been operating under the radar since at least 2021, successfully compromising organizations in Asia, Europe, and the United States across various sectors, including pharmaceuticals, oil and gas, and technology.
LilacSquid’s Modus Operandi:

The APT group employs a dual-pronged approach for initial access, either exploiting vulnerabilities in web applications or leveraging compromised remote desktop protocol (RDP) credentials. Once inside a network, LilacSquid deploys a series of malicious tools, including MeshAgent (an open-source remote management tool), a customized version of QuasarRAT dubbed “PurpleInk,” and Secure Socket Funneling (SSF) for covert communication and data exfiltration.
Modularized Infection Chain:
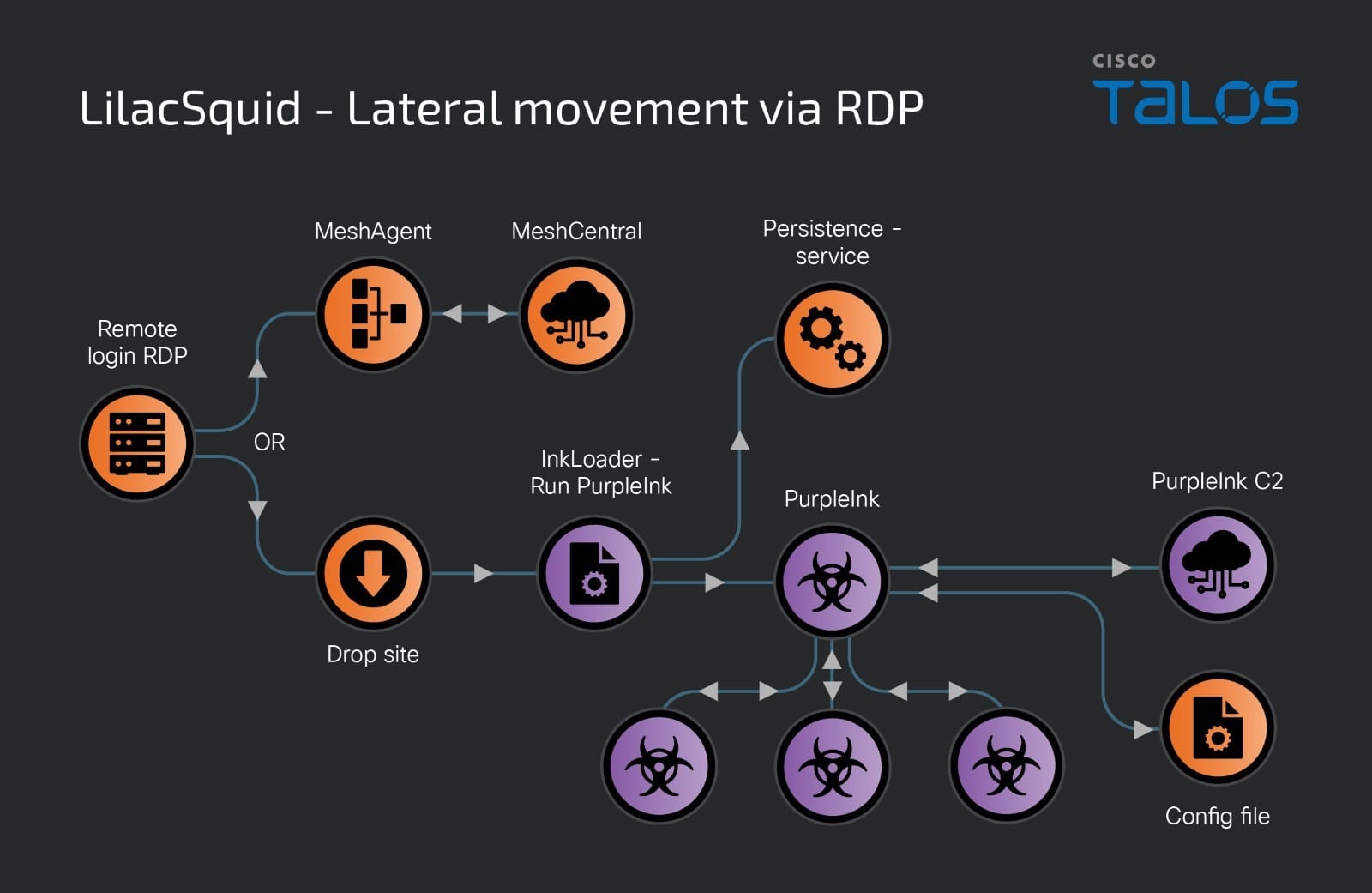
Talos researchers have observed LilacSquid evolving its tactics over time, including the introduction of a modular malware loader called InkLoader in newer attacks. This allows the group to deploy PurpleInk as a separate process, increasing stealth and making detection more difficult.
Links to North Korean APT Groups:
Interestingly, LilacSquid’s tactics, techniques, and procedures (TTPs) bear similarities to those employed by North Korean APT groups like Andariel and Lazarus. This includes the use of MeshAgent for post-compromise access and the deployment of custom malware and tunneling tools for lateral movement and data exfiltration.
Global Impact and Concerns:
LilacSquid’s extensive targeting of diverse industries and regions raises concerns about the potential for widespread economic and intellectual property theft. The group’s focus on software manufacturers also raises the specter of supply chain attacks, where malicious code could be injected into widely used software products, further amplifying the impact of their activities.
For more detailed information on the LilacSquid campaign and to stay updated on cybersecurity threats, visit the official Cisco Talos website.