
A recent report by Cyble Research and Intelligence Labs (CRIL) unveils a troubling trend: threat actors are increasingly leveraging LNK files and SSH commands as stealthy tools to orchestrate advanced cyberattacks. These techniques enable attackers to bypass traditional security measures, maintain persistence, and execute multi-stage attack chains that compromise systems worldwide.
LNK files, commonly known as Windows shortcut files, have become a preferred initial infection vector for threat actors. “These malicious shortcut files, often disguised as legitimate documents, have become a preferred entry point for attackers seeking to compromise systems,” CRIL notes in the report. By embedding commands that exploit Living-off-the-Land Binaries (LOLBins), such as PowerShell and rundll32, attackers can execute additional payloads while evading detection.
Adding a layer of sophistication, recent campaigns have embedded SSH commands within malicious LNK files. These commands facilitate various malicious activities, including data exfiltration, remote payload execution, and persistence. CRIL observed attackers using the Secure Copy Protocol (SCP) to download and execute malicious files. One such campaign employed an SSH command configured as follows:
This command downloaded a malicious executable disguised as a legitimate application to advance the attack.
The report highlights multiple ways SSH commands are abused:
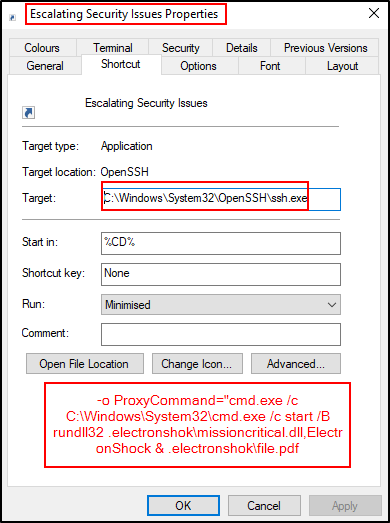
- SCP for File Downloads: Attackers use SCP to retrieve and execute malicious files from remote servers.
- PowerShell Execution via ProxyCommand: SSH commands invoke PowerShell to execute malicious scripts, such as accessing remote URLs through mshta.exe to download harmful payloads.
- Rundll32 and CMD Exploitation: SSH commands trigger rundll32 to load malicious DLLs, accompanied by decoy documents to distract the victim.
Advanced Persistent Threat (APT) groups have adopted these techniques, integrating them into their playbooks to target high-value sectors. CRIL identified similarities between recent campaigns and prior attacks attributed to the APT group Transparent Tribe, known for targeting defense and aerospace sectors.
The use of LNK files and SSH commands represents a paradigm shift in cyberattack methodologies. “These techniques are continuously evolving, with threat actors refining their methods to evade detection by exploiting trusted system utilities,” CRIL emphasizes.
Related Posts:
- Turla APT Suspected in “Tiny BackDoor” Campaign Leveraging MSBuild to Evade Detection
- Turla APT Group Unleashes Sophisticated Fileless Backdoor via Compromised Site
- New Phishing Scam Targets Android Users in India, Researchers Warn