
Cybersecurity researchers at Trend Micro Managed XDR have uncovered a sophisticated malware campaign that leverages GitHub’s release infrastructure to distribute the Lumma Stealer malware, a dangerous information-stealing Trojan. The campaign, which exhibits tactics consistent with the Stargazer Goblin threat group, also deploys additional malware, including SectopRAT, Vidar, and a secondary Lumma Stealer variant.
“Malicious actors exploited GitHub as a trusted platform to deliver the stealer, which subsequently initiated additional malicious activities,” researcher wrote.
The attackers used compromised websites and GitHub repositories to distribute pre-signed URLs for malware payloads, further demonstrating their adaptability and evolving infection techniques.
Trend Micro’s investigation traced the initial access of the Lumma Stealer infections to files downloaded from GitHub’s release mechanism.
🔹 Malicious Executables Identified:
- Pictore.exe
- App_aeIGCY3g.exe
These files were hosted on GitHub’s release infrastructure and downloaded by victims via links embedded in compromised websites and phishing campaigns.
“In one instance, a user downloaded a file named Pictore.exe via the Google Chrome browser, with the URL pointing to a GitHub-hosted release asset stored on a cloud service provider.”
Both files were initially digitally signed by ConsolHQ LTD and Verandah Green Limited, but the certificates were later revoked after Trend Micro flagged the binaries as malicious.
Once executed, Lumma Stealer quickly drops and extracts multiple files from an embedded 7-Zip archive, including:
- nsis7z.dll (used to extract more files)
- System.dll (likely used for persistence)
- Temporary executables for lateral execution
“The dropped file C:\Users<username>\AppData\Local\Temp\1\nse2869.tmp\nsis7z.dll is a 7zip archiving tool used to extract files from the malware’s embedded archive.”
Lumma Stealer is designed to steal sensitive data, including:
✅ Stored browser credentials (Chrome, Edge, Firefox, and Brave)
✅ Cryptocurrency wallets (MetaMask, Phantom, Trust Wallet, Binance Wallet)
✅ System information (hostname, IP address, OS version, running processes)
✅ Session cookies and saved autofill data
The malware establishes contact with two command-and-control (C2) servers:
- 192[.]142[.]10[.]246:80
- 192[.]178[.]54[.]36:443
These servers receive stolen data and issue additional payloads for execution.
“The malware collected system information, including RAM size, display adapter, OS version, hostname, uptime, user directory paths, and temporary directory content.”
Beyond Lumma Stealer, Trend Micro researchers found that the initial malware downloads additional payloads, including:
🔹 SectopRAT – A remote access Trojan (RAT) that allows attackers to control infected systems and deploy further payloads.
🔹 Vidar – A well-known infostealer that targets browser data, cryptocurrency wallets, and cloud storage accounts.
🔹 Cobeacon – A lesser-known malware variant likely used for post-exploitation operations.
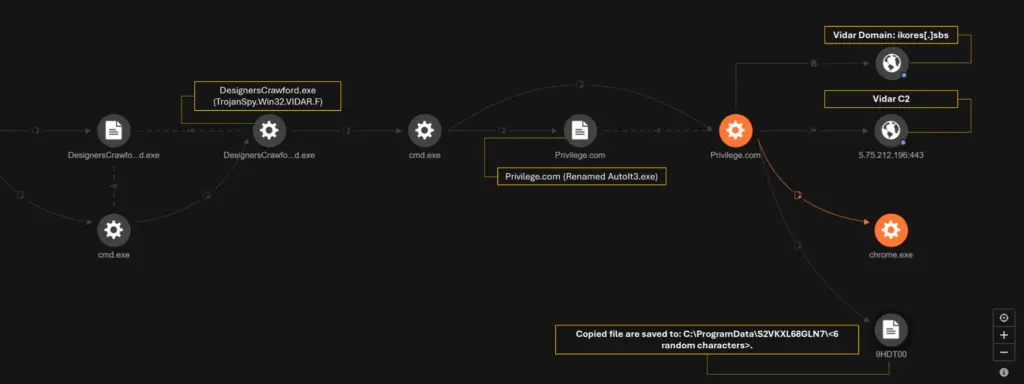
“The infected machines received additional threats, including SectopRAT, Vidar, Cobeacon, and another Lumma Stealer variant.”
Each of these payloads is designed to maximize data theft and persistence, making removal significantly harder for victims.
Trend Micro’s analysis suggests that the malware is either built using Electron (a framework based on Chromium) or masquerades as a Chromium-based application to bypass security software.
“Electron apps, by default, bundle Chromium with the app to render the graphical user interface.”
In addition, Lumma Stealer executes various PowerShell and CMD commands to:
🛑 Disable GPU sandboxing to evade security monitoring.
🔍 Gather hardware and system information to detect if the malware is running inside a virtualized environment.
📤 Exfiltrate data to attacker-controlled C2 servers.
The use of GitHub for malware distribution is not new, but this campaign highlights how cybercriminals are abusing GitHub’s trust to host malicious payloads.
“The GitHub accounts used in the campaign demonstrate minimal activity and were primarily focused on creating repositories and hosting malicious releases,” Trend Micro warned.
Despite takedown efforts, new accounts are quickly created to replace banned repositories, showing how cybercriminals are weaponizing GitHub’s infrastructure for malware delivery.
Related Posts:
- CVE-2024-55417: One-Click RCE Vulnerability in Voyager Admin Panel, No Patch
- Cyber Espionage and Influence: Unmasking APT28’s Tactics Sources and related content