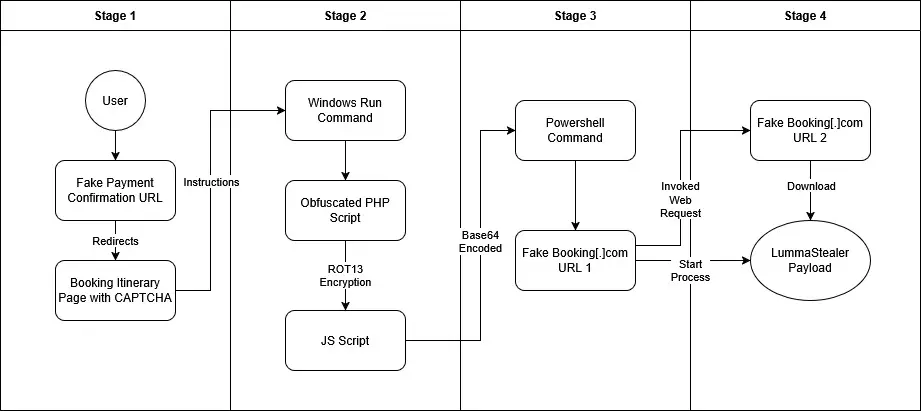
Infection Chain | Image: G DATA
In a concerning evolution of malvertising tactics, threat actors have begun using fake booking websites to distribute LummaStealer, an info-stealer malware offered under the Malware-as-a-Service (MaaS) model. According to G DATA analysts, the latest LummaStealer campaign targets victims worldwide by leveraging fraudulent booking itinerary pages and deceptive CAPTCHA verifications to execute malicious payloads.
Originally observed in 2022, LummaStealer has traditionally spread through platforms like GitHub and Telegram. However, G DATA’s latest findings indicate that attackers are now exploiting online booking platforms to infect unsuspecting travelers.
“Using things such as booking websites is a new approach for LummaStealer. Previously, this malware was primarily being spread through channels like GitHub or Telegram,” G DATA analysts explain.
The campaign’s infection chain was first detected in early 2025, targeting users booking trips to Palawan, Philippines. Within a week, the attack vector shifted to a hotel in Munich, Germany, indicating a broader global focus on travel-related platforms.
Victims are lured into the attack through fraudulent booking confirmation pages hosted on malicious domains. These fake booking pages feature a CAPTCHA prompt, but unlike a standard verification step, this one tricks users into executing a hidden malware payload. This social engineering tactic, known as ClickFix, convinces users to manually execute a PowerShell command that downloads and launches LummaStealer on their system.
Once deployed, LummaStealer exhibits a 350% increase in file size (from 2MB to 9MB) compared to earlier versions. Researchers believe this suggests the incorporation of new evasion mechanisms, such as:
- Binary Padding – Adding junk data to bypass antivirus file size restrictions
- Indirect Control Flow Obfuscation – Using Dispatcher Blocks to dynamically calculate execution paths, making malware analysis more difficult
Larger files result in longer response times for signature-based antivirus detections. The way it does this is by using Dispatcher Blocks, which control execution dynamically.
G DATA researchers warn that LummaStealer is rapidly evolving and may soon resemble notorious malware families like Emotet, which utilized multiple attack vectors and extensive obfuscation. With its increased payload complexity and new delivery mechanisms, LummaStealer is expected to remain a persistent cybersecurity threat in the coming months.
Related Posts:
- Fake CAPTCHA Phishing Campaign Impacts Over 1,150 Organizations
- Cybercriminals Exploit CAPTCHA to Deliver Malware: Experts Issue Warning