Metasploitable3: Exploiting Axis2 vulerability
Introduction
Apache Axis2™ is a Web Services / SOAP / WSDL engine, the successor to the widely used Apache Axis SOAP stack. There are two implementations of the Apache Axis2 Web services engine – Apache Axis2/Java and Apache Axis2/C.
Metasploitable3 is a VM that is built from the ground up with a large number of security vulnerabilities. It is intended to be used as a target for testing exploits with Metasploit.
Penetration Testing
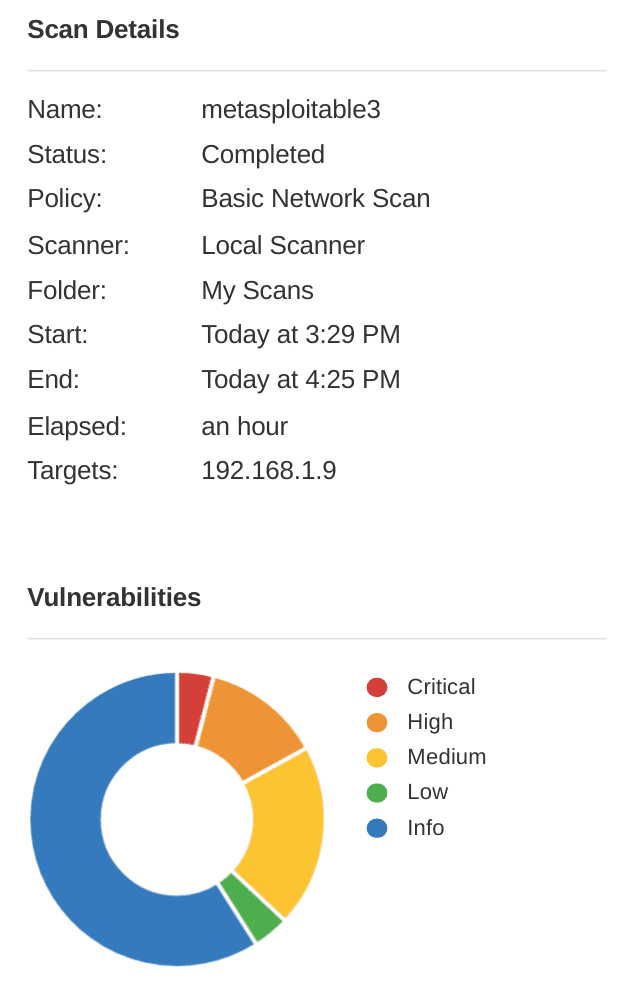
- Installing Nessus, please visit here. Scanning vulnerability using Nessus.
- Using exploit/multi/http/axis2_deployer module on Metasploit
This module logs in to an Axis2 Web Admin Module instance using a specific user/pass and uploads and executes commands via deploying a malicious web service by using SOAP. - Enjoy!





