mssqlproxy
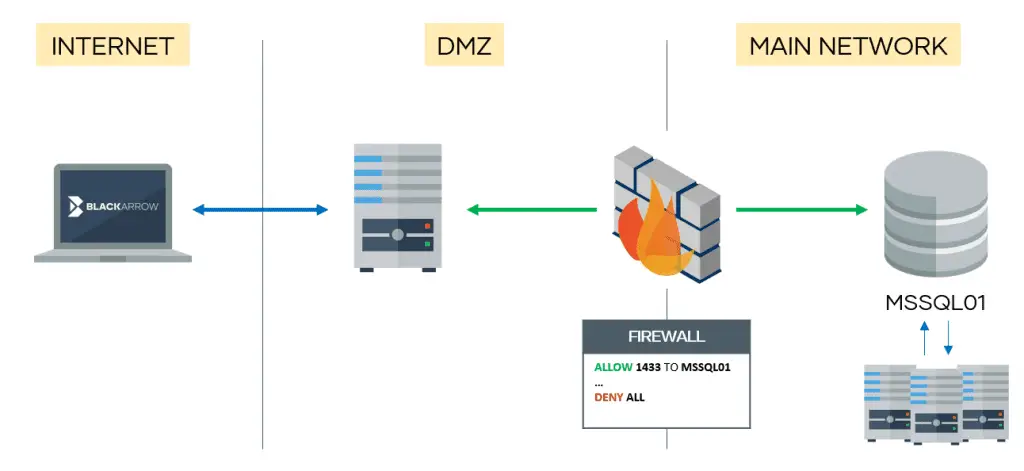
mssqlproxy is a toolkit aimed to perform a lateral movement in restricted environments through a compromised Microsoft SQL Server via socket reuse. The client requires impacket and sysadmin privileges on the SQL server.
Please read this article carefully before continuing.
It consists of three parts:
- CLR assembly: Compile assembly.cs
- Core DLL: Compile reciclador.sln
- Client: mssqlclient.py (based on Impacket’s example)
Use
Once the two libraries are compiled, upload the core DLL (reciclador) to the target server.
Authentication options are the same as the ones in the original mssqlclient. mssqlproxy options:
We have also implemented two commands (within the SQL shell) for downloading and uploading files. Relating to the proxy stuff, we have four commands:
- install: Creates the CLR assembly and links it to a stored procedure. You need to provide the -clr param to read the generated CLR from a local DLL file.
- uninstall: Removes what install created.
- check: Checks if everything is ready to start the proxy. Requires to provide the server DLL location (-reciclador), which can be uploaded using the upload command.
- start: Starts the proxy. If -local-port is not specified, it will listen on port 1337/tcp.
Once the proxy is started, you can plug in your proxychains 😉
Note #1: if using a non-direct connection (e.g. proxies in between), the -no-check-src-port flag is needed, so the server only checks the source address.
Note #2: at the moment, only IPv4 targets are supported (nor DNS neither IPv6 addresses).
Note #3: use carefully! by now the MSSQL service will crash if you try to establish multiple concurrent connections
Important: It’s important to stop the mssqlproxy by pressing Ctrl+C on the client. If not, the server may crash and you will have to restart the MSSQL service manually.
Download
Copyright (c) 2020 BlackArrow