Leprechaun
The purpose of this tool is to help penetration testers identify potentially valuable targets on the internal network environment. By aggregating netstat routes from multiple hosts, you can easily figure out what’s going on within.
How it Works
Using a tool such as Josh Stone’s routehunter, or any other process/tool that can recursively run netstat on multiple hosts, you can provide Leprechaun this output and get a visual representation of the data flow (or network connections) within the environment.
Install
gem install ‘securerandom’
gem install ‘terminal-table’
gem install ‘getopt’
git clone https://github.com/vonahi-security/leprechaun.git
Use
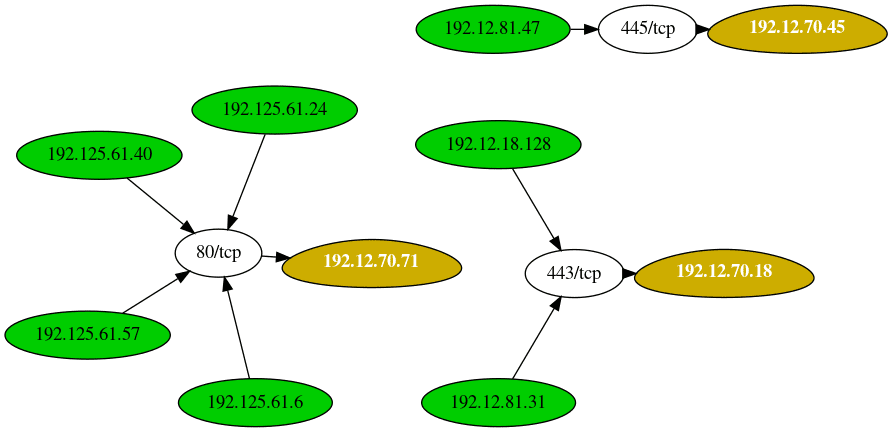
Example outputs
+--------------+-----------------------------+----------------------------------+
| Server | Number of connected clients | Highest traffic destination port |
+--------------+-----------------------------+----------------------------------+
| 192.12.70.71 | 4 | 80/tcp (4 clients) |
| 192.12.70.18 | 2 | 443/tcp (2 clients) |
| 192.12.70.45 | 1 | 445/tcp (1 clients) |
+--------------+-----------------------------+----------------------------------+Copyright (c) 2019 Vonahi Security
Source: https://github.com/vonahi-security/