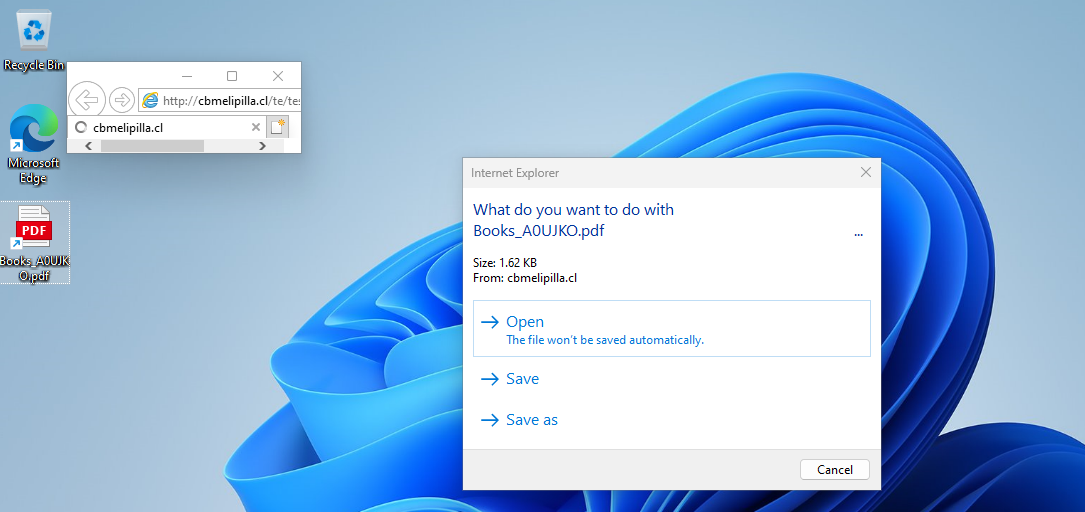
IE and a promote window dialog appear when the victim double-clicks on the .url file | Image: Check Point
In an unexpected turn of events, Microsoft has revised its September 2024 Patch Tuesday security advisory, revealing a fifth zero-day vulnerability actively exploited in the wild. The disclosure comes just days after the company’s initial announcement of security updates addressing 79 flaws, including four zero-days.
The newly identified vulnerability, tracked as CVE-2024-43461, impacts the Windows MSHTML Platform and facilitates spoofing attacks. With a CVSS severity score of 8.8, this vulnerability poses a significant risk of exploitation.
The CVE-2024-43461 flaw is a spoofing vulnerability in the Windows MSHTML platform, a key component used by the Internet Explorer rendering engine. This bug allows threat actors to manipulate MSHTML’s parsing behavior, tricking users into believing they are interacting with a legitimate source when, in fact, they are not. The ZDI Threat Hunting team was the first to identify and report this vulnerability to Microsoft back in June 2024.
However, this flaw appears to be related to a previous exploit chain involving CVE-2024-38112, which was patched in Microsoft’s July 2024 security updates. At the time, the patch for CVE-2024-38112 was thought to mitigate the attack chain, but it appears that threat actors have found a way to bypass the earlier fix, leaving users vulnerable to this new variant of the exploit.
On September 10th, when Microsoft released Patch Tuesday, the Zero Day Initiative (ZDI) expressed concern that this vulnerability is not officially listed as “under active attack,” despite evidence that it has been used in the wild. According to ZDI, the bug was being actively exploited when reported, and its exploitation is similar to a vulnerability the team identified earlier this year.
“CVE-2024-43461 was exploited as a part of an attack chain relating to CVE-2024-38112,” Microsoft noted in its advisory. “We released a fix for CVE-2024-38112 in our July 2024 security updates which broke this attack chain. Customers should both the July 2024 and September 2024 security update to fully protect themselves.” Microsoft has urged users to install both the July 2024 and September 2024 security updates to ensure complete protection.
The inclusion of CVE-2024-43461 brings the total number of zero-day vulnerabilities patched by Microsoft in September to five. The original four zero-day vulnerabilities patched earlier this week are:
- CVE-2024-38014 – Windows Installer Elevation of Privilege Vulnerability
- CVE-2024-38217 – Windows Mark of the Web Security Feature Bypass Vulnerability
- CVE-2024-38226 – Microsoft Publisher Security Feature Bypass Vulnerability
- CVE-2024-43491 – Microsoft Windows Update Remote Code Execution Vulnerability
These flaws span multiple attack vectors, from privilege escalation and code execution to bypassing key security features.
Related Posts:
- Microsoft’s September Patch Tuesday: A Patchwork of Urgency with 4 Zero-Days Under Attack
- Check Point Research Details 0-Day Flaw (CVE-2024-38112), Threatens Windows Users
- Microsoft Patches Actively Exploited 0-Day Flaws (CVE-2024-30040 & CVE-2024-30051)
- Android’s July 2024 Security Patches Fix Critical Vulnerability