Image: Phylum
Recently, the Phylum team’s automated risk detection platform uncovered a suspicious publication on npm, a popular package manager for JavaScript. This discovery shed light on a complex attack orchestrated through the seemingly innocuous “oscompatible” package. The package raised red flags due to its unusual contents, which included binaries, JavaScript files, and encrypted data. The subsequent investigation unveiled a sophisticated Remote Access Trojan (RAT) deployment masquerading as a standard Microsoft update process.
Unlike typical malware found on npm, this malicious package does not execute upon installation. Instead, it exports a function called “compat” in its index.js file. To activate the execution chain, a script must explicitly call “compat()” without requiring administrative privileges. This raises questions about the attacker’s intended deployment method, as the package lacks a README but claims to make projects compatible with ChromeOS in its package.json description. Is the attacker attempting to deceive casual users or providing specific instructions for package use? This malware doesn’t follow the infect-on-install model, making it a unique threat.

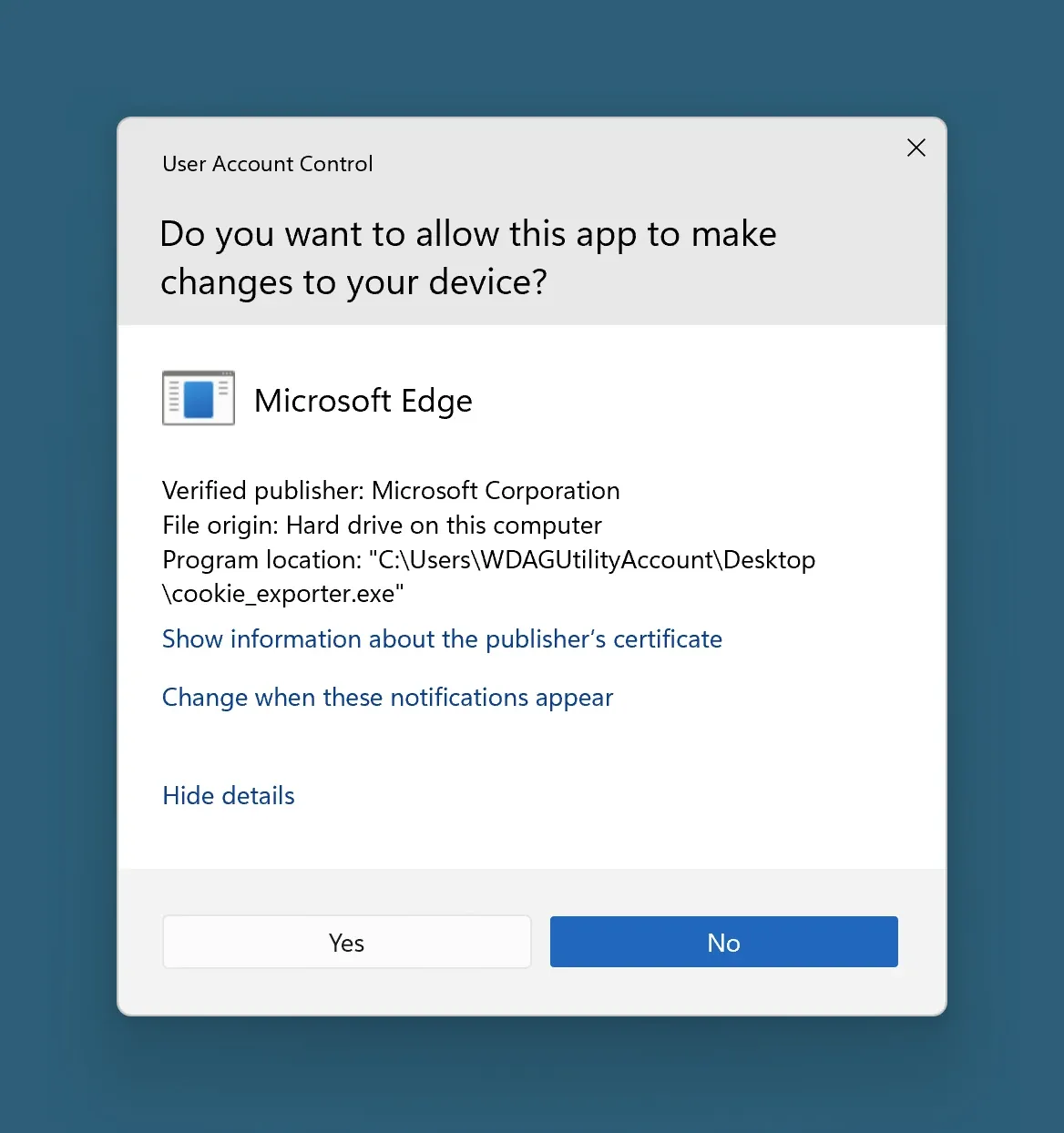
Let’s dissect the attack chain starting with the index.js file, the package’s sole JavaScript component. This file checks the platform, and if it’s Windows, it runs an autorun.bat file. If not, it requests execution on a “Windows Server OS.” The autorun.bat script first checks for administrator privileges. If absent, it runs “cookie_exporter.exe” with privilege escalation. However, if the script already has admin privileges, it proceeds without requesting further access.
The pivotal component, “cookie_exporter.exe,” is a legitimate Microsoft Edge component exploited due to its valid Authenticode signature. When run with admin privileges, it attempts “DLL search order hijacking” by loading a rogue “msedge.dll” from the same directory, signed using a revoked certificate. This dll is not the authentic Microsoft Edge dll, and it executes a function named “ExportSpartanCookies.” Instead of exporting Edge cookies, it decrypts an attacker-supplied “msedge.dat” file with a 352-byte XOR key, producing another DLL named “msedgedat.dll,” which it runs directly from memory.
“msedgedat.dll” communicates with “kdark1[.]com,” downloading a zip file dated 2024 JAN 13. The zip file contains malicious payloads, including screen-takeover software, AnyDesk, and DLLs injected into system processes. The decrypted “verify.dll” is a RAT, capable of registering as a scheduled task, receiving commands from a remote server, installing Chrome extensions, configuring AnyDesk, and collecting sensitive user data.
At the time of this publication, “oscompatible” appears to be the sole package associated with this campaign on npm. The attack’s complexity, from decrypting data to using revoked certificates for signing and sourcing files remotely, indicates a higher level of sophistication compared to typical open-source ecosystem threats.