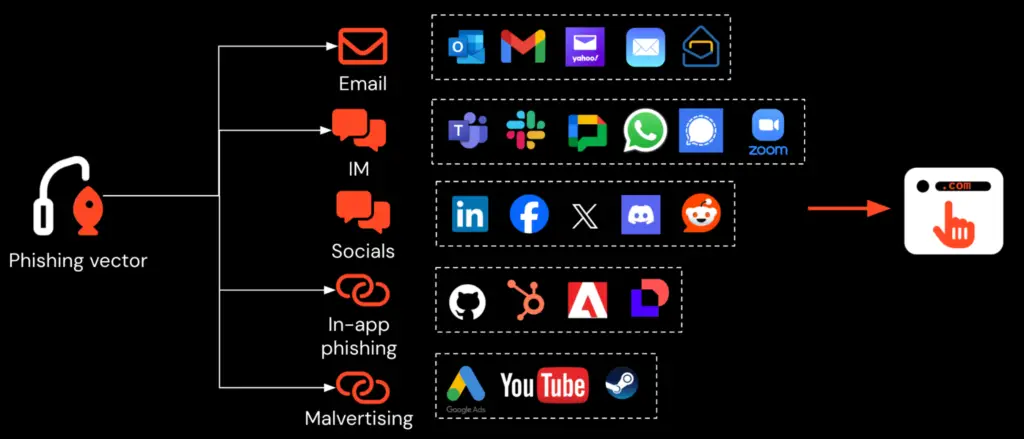
A new phishing campaign has emerged that hijacks trust not through inboxes, but through Google ads. Security researchers at Push have uncovered a malvertising campaign targeting users of Onfido, a digital identity verification platform widely used in fintech, HR, and regulated industries.
The attackers used a deceptive Google search ad to lure victims into clicking a spoofed Onfido login page hosted on a domain that looks legitimate: dashboard[.]onfido[.]us[.]com.
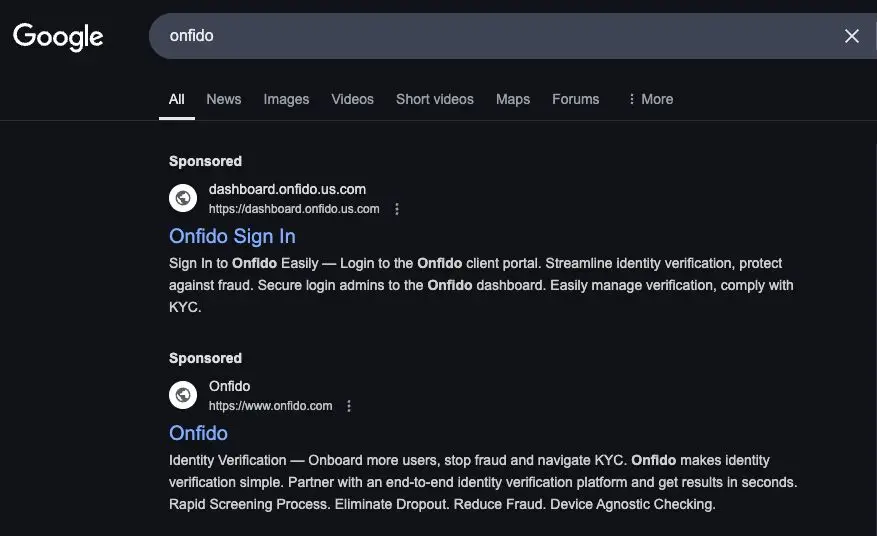
Once clicked, the malicious link led to a cloned Onfido page that appeared credible enough to fool the victim. However, Push’s browser-based detection system flagged the URL immediately. The fake login page was being served through Evilginx, a man-in-the-middle phishing framework that proxies legitimate pages to steal session tokens and credentials.
“Although the page was not the official login page for Onfido, it appeared legitimate enough at first glance to trick the user.”
Interestingly, the phishing page was configured to only display properly when accessed through a Google ad referral. Visiting the same domain directly would redirect users to a 404 page on the legitimate Onfido domain—an evasive tactic to avoid detection by security crawlers.
Onfido isn’t a typical phishing target like Microsoft or Google. But that’s exactly the point.
“Attackers are diversifying their phishing targets… Onfido contains valuable data that attackers can take advantage of… plenty of PII that can be leveraged to extort a victim.”
With phishing defenses hardening around major platforms, attackers are shifting focus to lesser-monitored SaaS tools—often lacking features like passkey support or strong identity policies.
This attack is a textbook case of malvertising—using paid search results to deliver malicious links. Google ads don’t rely on the same reputation and domain history checks as email gateways, giving attackers a fresh channel to launch phishing attempts.
“Malvertising doesn’t require much effort… you put the link up and wait for the clicks to roll in.“
The spoofed domain used us[.]com—not a legitimate U.S. government top-level domain but a domain resale service that allows subdomains to impersonate trusted brands. It’s cheap, easy to register, and difficult for the average user to distinguish from a genuine .us site.
Though originally created as a red-team tool, Evilginx is increasingly used in the wild for phishing campaigns. Its strength lies in its flexibility—it can proxy almost any login page without needing extensive custom JavaScript, reducing its detectability by security tools.
Even if your emails are clean, your search bar might be the weakest link. As Push puts it, “phishing attacks that bypass email like malvertising are so appealing” because they sidestep defenses entirely.
Related Posts:
- Vulnerable Clicks: PikaBot Hijacks Businesses with Malvertising
- Beware of Fake AI Photo Editors on Social Media: Malvertising Campaign Targets Credentials
- Google Ads Abused in Graphic Design Malvertising Attack
- Microsoft Uncovers Massive Malvertising Campaign Distributing Info Stealers via GitHub
- Google Products Exploited in Sophisticated Malvertising Scheme
