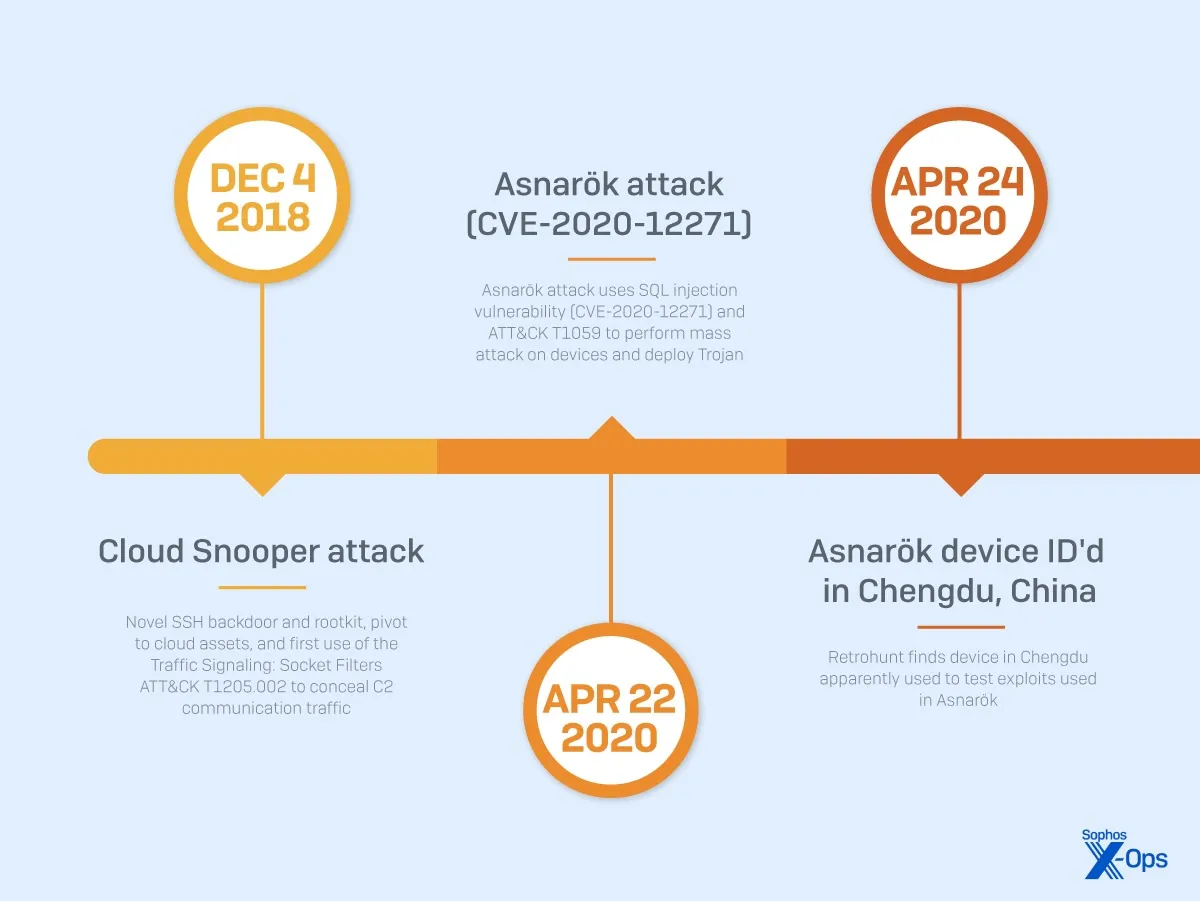
An abridged timeline of Pacific Rim activity, December 2018 to April 2020 | Image: Sophos X-Ops
In a newly released report titled “Pacific Rim,” Sophos X-Ops uncovers a five-year campaign by China-based threat groups targeting high-value infrastructure and government organizations across the Indo-Pacific. These operations involve advanced tactics, including bespoke malware, stealthy persistence mechanisms, and sophisticated operational security. Working alongside other cybersecurity firms, law enforcement, and government agencies, Sophos has linked these attacks to notorious state-sponsored groups, such as Volt Typhoon, APT31, and APT41/Winnti.
According to Sophos X-Ops, the initial years of this campaign were marked by large-scale, “noisy” attacks. However, as the attackers honed their strategies, their focus shifted toward stealthier, high-value targets. “Sophos has identified three key evolving attacker behaviors,” the report states, “a shift from indiscriminate attacks to stealthier operations against high-value and critical infrastructure targets primarily located in the Indo-Pacific region”. These targets include nuclear energy suppliers, government agencies, and telecom providers, where prolonged access could provide significant intelligence and strategic advantages.
The report highlights the threat actors’ remarkable technical sophistication, citing a range of persistence techniques to maintain access on compromised devices. Sophos X-Ops notes the use of “memory-only Trojans, backdoored Java classes, and an experimental UEFI bootkit,” which they believe marks the “first observed instance of bootkit use specifically on a firewall”. Such methods underscore the attackers’ intent to avoid detection by operating directly in device memory and firmware.
In addition to these stealthy malware deployments, the attackers disrupted device telemetry to evade detection. “As early as April 2020, the attackers sabotaged the hotfix mechanism of devices they compromised,” Sophos reveals. Later, they targeted telemetry systems, “preventing Sophos from getting early warning of their activity.”
The report underscores the importance of edge devices as critical entry points, often exploited to establish operational relay boxes (ORBs) for onward attacks. Sophos highlights that attackers use zero-day and known vulnerabilities in these devices, creating extensive opportunities for infiltration. They stress that “edge network devices are high-value targets that well-resourced adversaries use for both initial access and persistence”. The message for defenders is clear: securing edge devices is crucial for protecting against targeted attacks and disruptions to essential services.
Sophos X-Ops calls for transparent communication between security vendors and encourages organizations to adopt robust detection and response strategies to counter these advanced threats. They have provided defenders with a set of Tactics, Techniques, and Procedures (TTPs) and Indicators of Compromise (IOCs) to aid in identifying malicious activity.
Related Posts:
- Cyberattack on Pacific Islands Forum: Chinese Hackers Suspected
- Sophos X-Ops Alerts: ‘Inhospitality’ Malspam Targets Hotels with Deceptive Tactics
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities
- Teal Kurma’s Evolving Cyber Activities: A Resurgent Threat to Europe and the Middle East