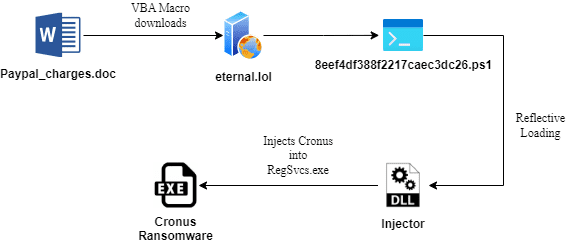
In a recent report, the Seqrite Labs APT-Team has exposed a series of malicious campaigns employing fake...
In a recent advisory published on August 8th, Microsoft disclosed a high-severity zero-day vulnerability affecting multiple versions...
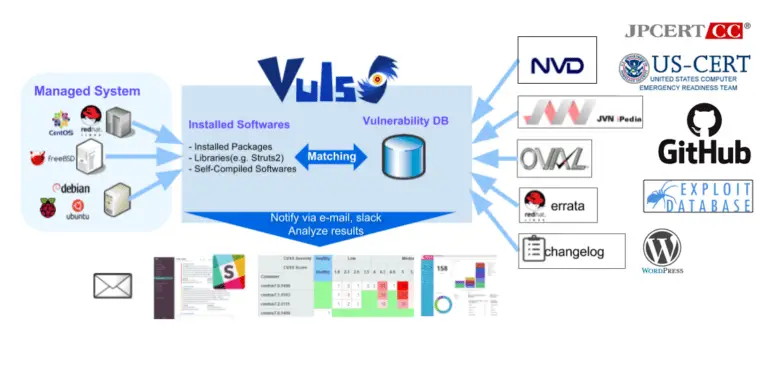
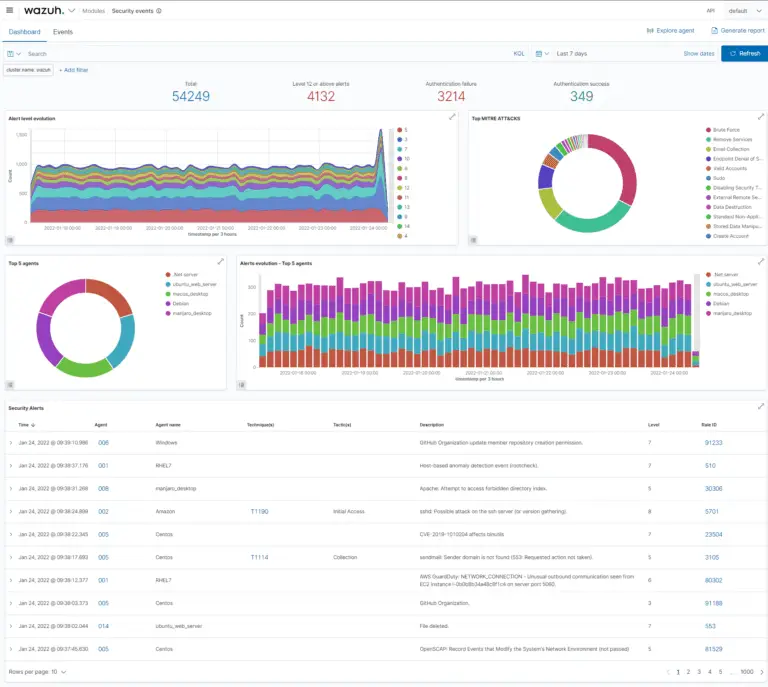
The ever-growing complexity of modern IT infrastructure, coupled with the relentless proliferation of cyber threats, places a...
GL-iNet has recently issued a security advisory addressing multiple critical vulnerabilities in several of their router models....
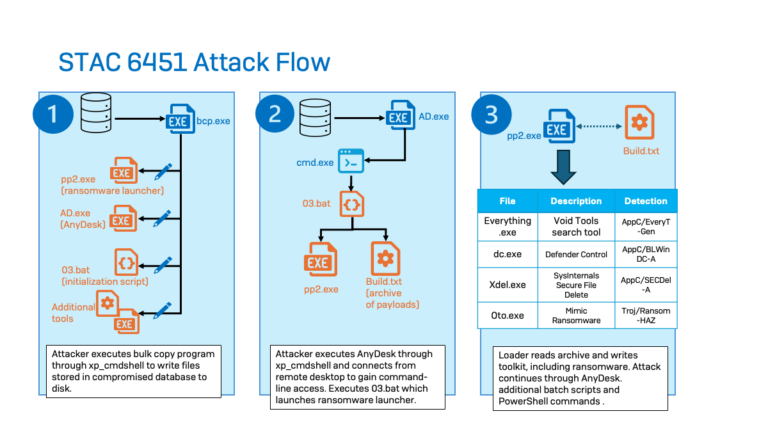
Sophos MDR threat hunters and intelligence analysts have recently unveiled a new threat activity cluster, dubbed STAC6451,...
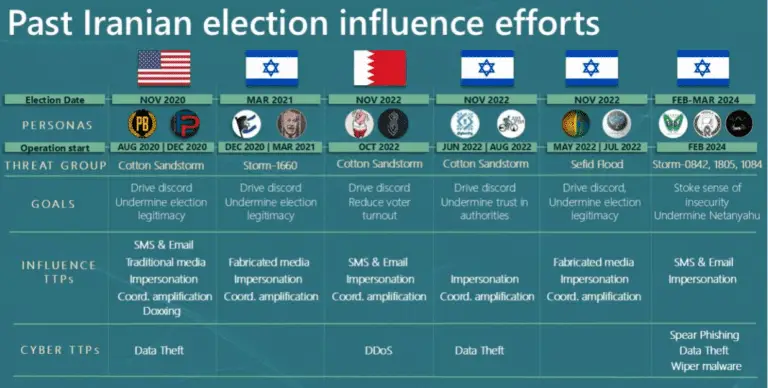
As the 2024 US presidential election approaches, the Microsoft Threat Analysis Center (MTAC) has reported a significant...
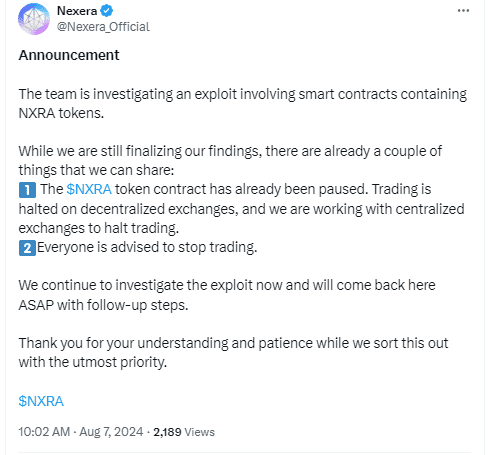
The blockchain infrastructure protocol Nexera, renowned for its tokenization solutions, fell victim to an attack in which...
In today’s complex and ever-evolving threat landscape, safeguarding diverse IT infrastructures demands a robust, adaptable security solution....
The Django team has issued security updates for Django 5.0.8 and 4.2.15 to address multiple vulnerabilities, including...
In a concerning development, cybersecurity researchers from Symantec’s Threat Hunter Team have uncovered a new Go-based backdoor...
Recently, the cybersecurity research team known as Team82 has published an in-depth investigation into a series of...
Cybersecurity specialists have discovered significant flaws in the protective mechanisms of Microsoft Windows—Smart App Control (SAC) and...
Department of Justice Disrupts North Korean IT Worker Fraud Scheme with Arrest of Nashville Resident


Department of Justice Disrupts North Korean IT Worker Fraud Scheme with Arrest of Nashville Resident
The U.S. Department of Justice announced on Thursday charges against Matthew Isaac Knoot, a 38-year-old Nashville resident,...
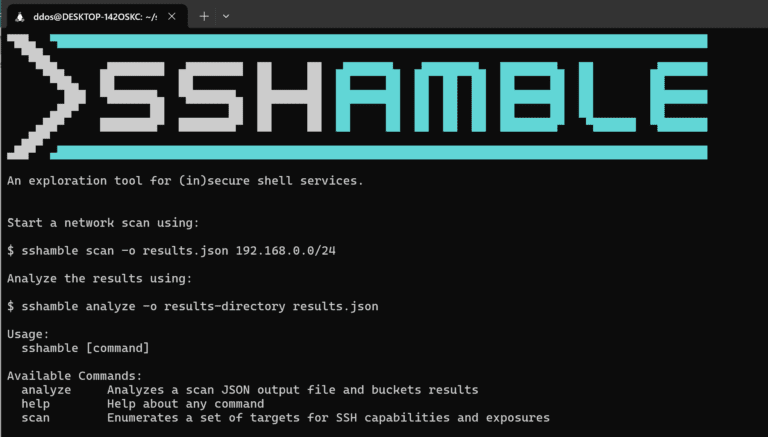
Experts at runZero have uncovered numerous vulnerabilities related to poorly secured or improperly implemented SSH services, an...
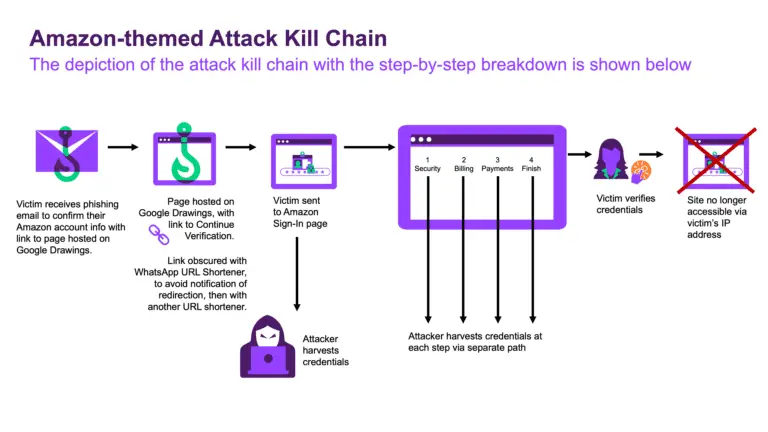
Menlo Security has uncovered a new phishing campaign that exploits Google Drawings to bypass security systems and...