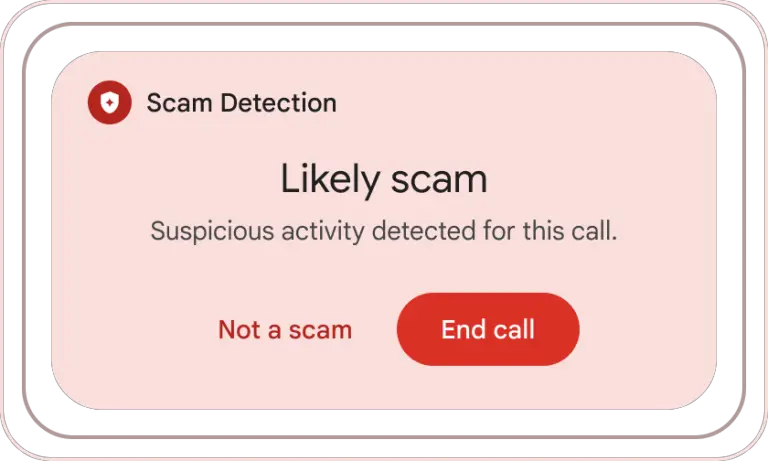
Pixel users are the first to benefit from new AI-powered security features in Phone by Google and...
Threats are evolving fast, with attackers constantly refining their techniques to slip past defenses. One of these...
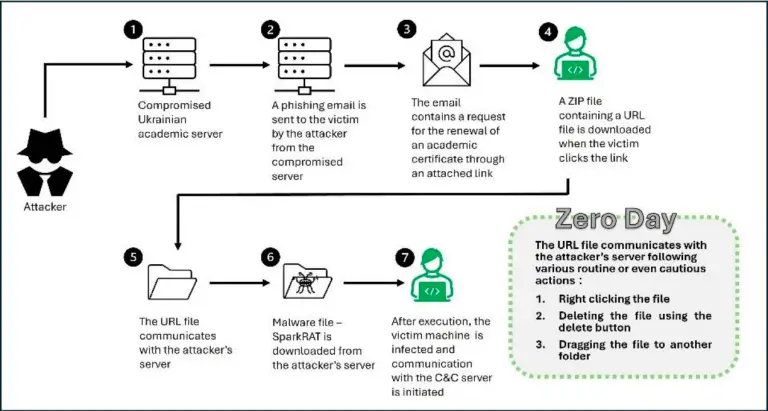
ClearSky Cyber Security has uncovered a new zero-day vulnerability, CVE-2024-43451, actively exploited in the wild, targeting Windows...
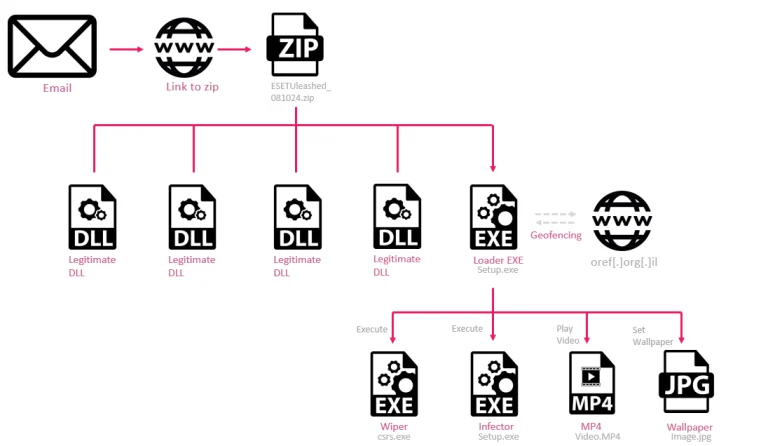
Researchers at Group-IB have discovered a new stealth technique employed by the North Korean APT group Lazarus,...
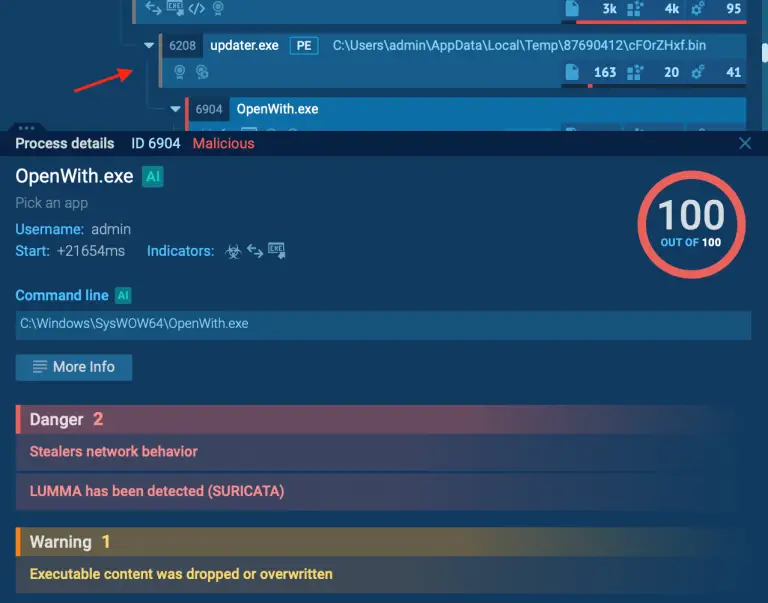
IBM’s X-Force team has identified a major surge in the distribution of Strela Stealer, a credential-stealing malware...
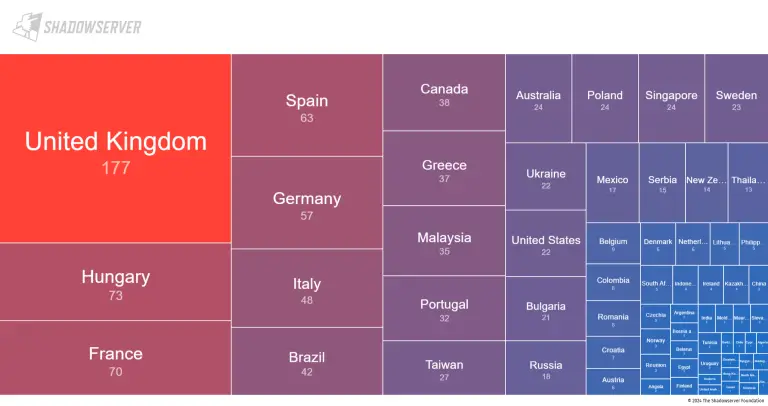
In a joint cybersecurity advisory, the top cybersecurity agencies from the United States, Australia, Canada, New Zealand,...
Check Point Research recently exposed ongoing activity from WIRTE, a Hamas-affiliated cyber-espionage group, that continues despite the...
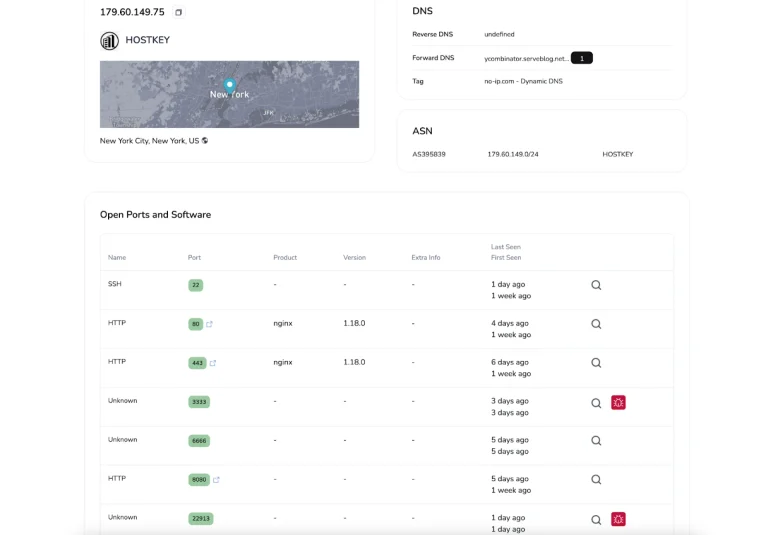
Security researchers from Threat Hunting Platform Hunt.io have uncovered a recent operation leveraging the Sliver command-and-control (C2)...
GitLab has released a critical security update addressing a high-severity vulnerability that could grant unauthorized access to...
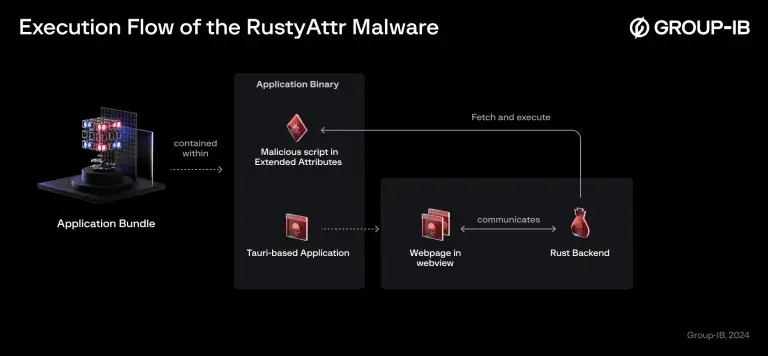
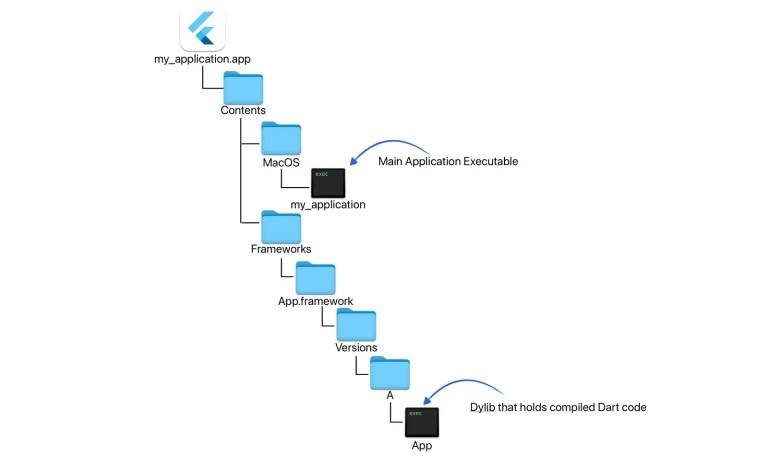
Researchers from Jamf Threat Labs have discovered multi macOS malware samples embedded within applications developed using the...
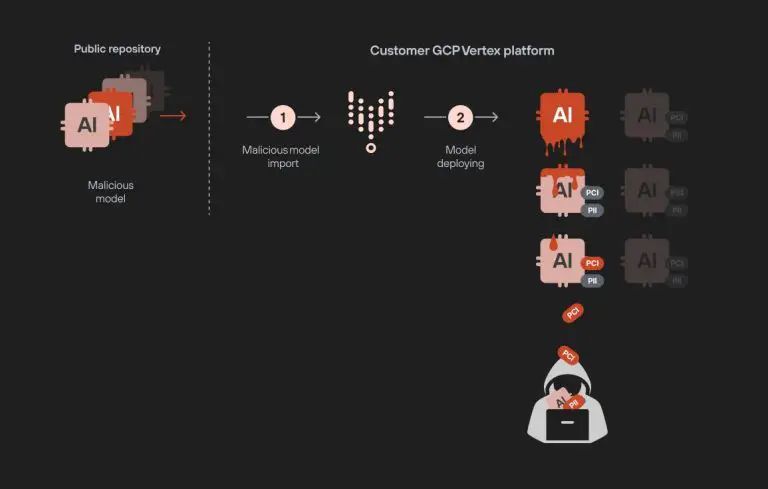
In a recent report, Palo Alto Networks researchers disclosed two critical vulnerabilities within Google’s Vertex AI platform...
A critical command injection vulnerability (CVE-2024-10914) impacting numerous end-of-life D-Link network-attached storage (NAS) devices is currently under...
Google Cloud today announced a significant step towards increased transparency in vulnerability disclosure. Effective immediately, the company...
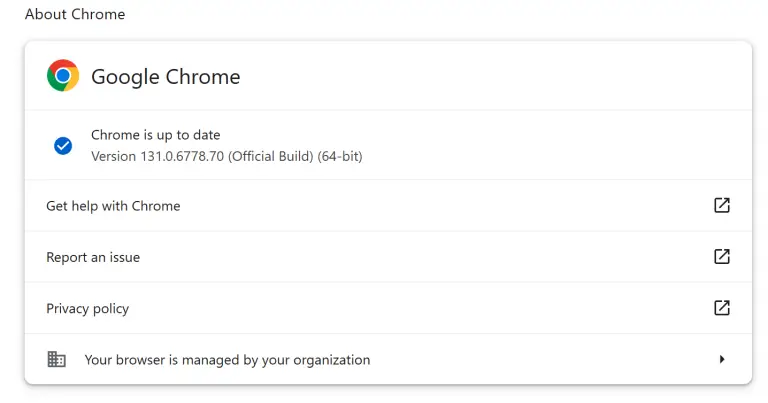
Google has released Chrome version 131, addressing a range of security vulnerabilities, including one classified as “high...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has expanded its Known Exploited Vulnerabilities (KEV) catalog, highlighting...