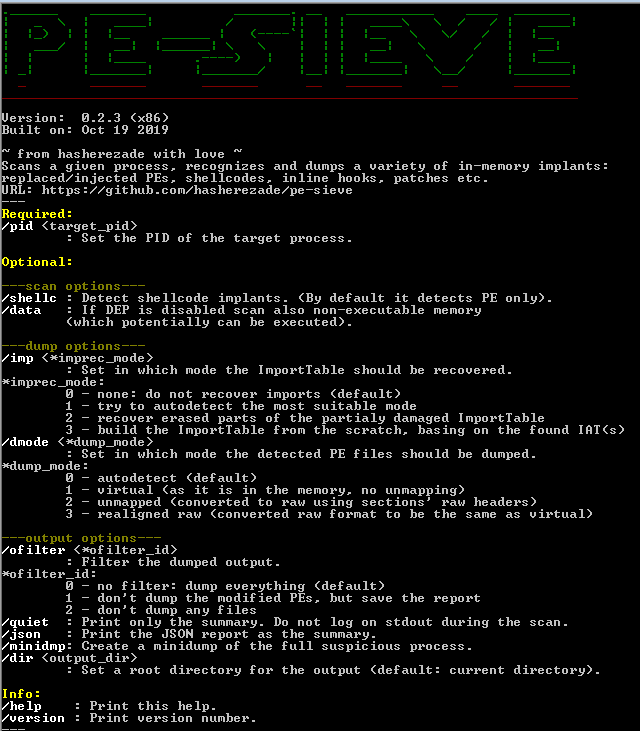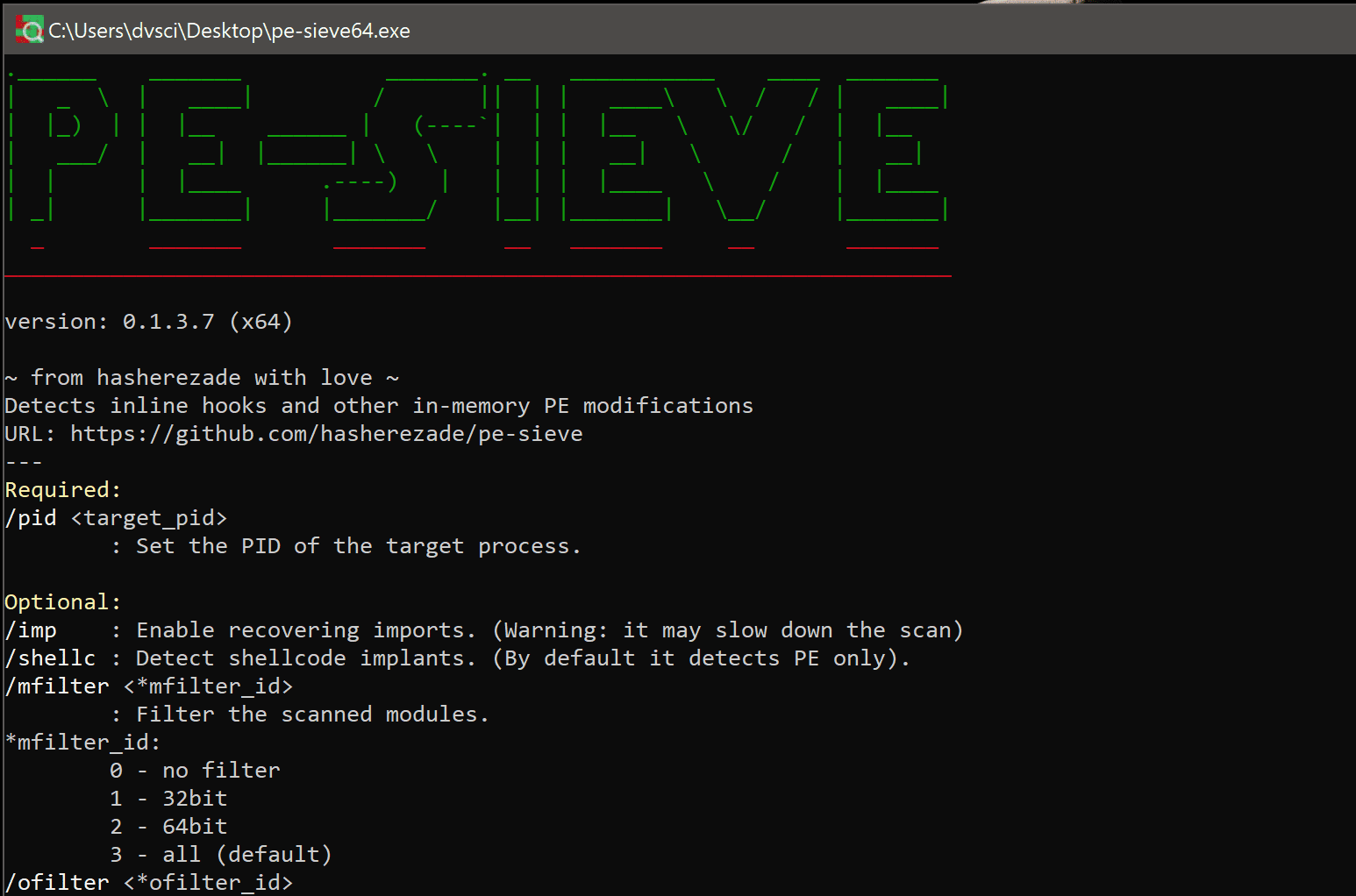
PE-sieve is a light-weight tool that helps to detect malware running on the system, as well as to collect the potentially malicious material for further analysis.
Recognizes and dumps a variety of implants within the scanned process, such as:
- replaced/injected PEs
- shellcodes
- hooks, and other in-memory patches.
Detects inline hooks, Process Hollowing, Process Doppelgänging, Reflective DLL Injection, etc.
It can be used for dynamic malware unpacking (see examples here).
PE-sieve works on Windows, the lowest supported version is XP.
PE-sieve scans a given process, searching for the modules containing in-memory code modifications. When found, it dumps the modified PE. When found, it dumps the modified PE. Currently, it detects inline hooks, hollowed processes, Process Doppelgänging etc. The tool is under rapid development, so expect frequent updates.
Detects inline hooks, hollowed processes etc.
This tool is intended to help malware analysts, malware hunters, and incident responders in their daily work.
Having a new sample to be analyzed, we can unpack it with PE-sieve very fast, extracting the payload that can be then easily identified and used for further analysis.
When we want to collect material from an infected system of a client, HollowsHunter (an extended PE-sieve based scanner) can scan the full system, dumping the injected code from each and every accessible process.
It can also help in cases when the infected client doesn’t know what is the sample that started the infection. PE-sieve/HollowsHunter will search for injected material in running processes and then dump the malicious PE.
Features
- Detecting inline hooks and patches
- Detecting hollowed processes
- Detecting Process Doppelgänging
FEATURE
- New options for shellcode detection (
/shellc):- detect by patterns (previous mode): available with
/shellc P - detect by stats (new mode): available with
/shellc S - possibility to mix both modes: options
/shellc B(both) or/shellc A(any)
- detect by patterns (previous mode): available with
- Detection of obfuscated memory regions (
/obfusc) - Caching of detected shellcodes (guarantee that the dumped shellcode is the same as detected shellcode – no second read)
Demo
Copyright (c) 2017-2018, @hasherezade
All rights reserved.
Source: https://github.com/hasherezade/