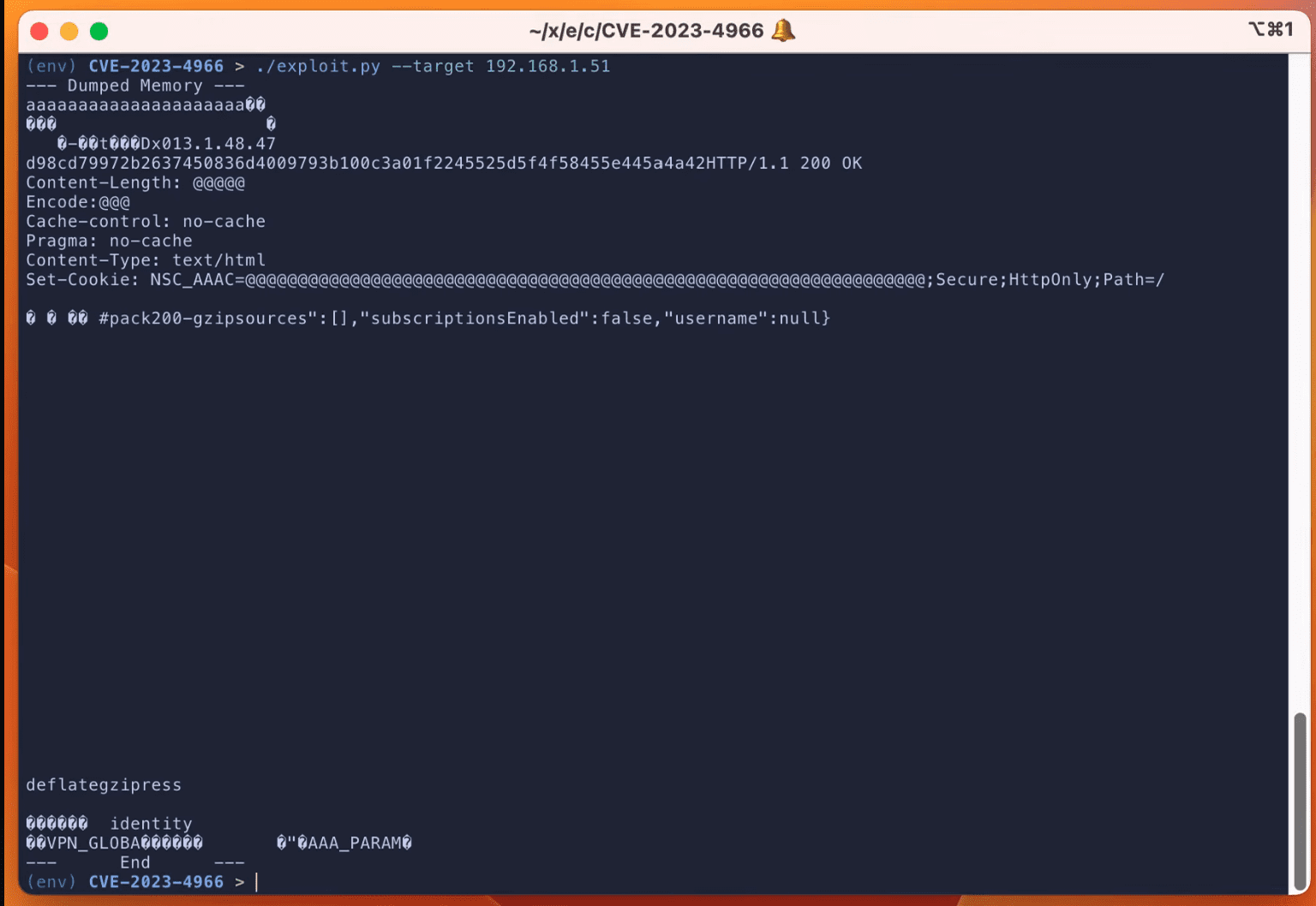
Proof-of-concept (PoC) exploit code is now available for a sensitive information disclosure flaw (CVE-2023-4966) in Citrix NetScaler ADC and NetScaler Gateway. This flaw has been grabbing headlines due to its high CVSS rating of 9.4. What’s even more concerning is its potential to be remotely exploited without necessitating high privileges, intricate user interaction, or high complexity.
For the vulnerability to be exploited, the Citrix appliance has to be set as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or an AAA virtual server. “Exploits of CVE-2023-4966 on unmitigated appliances have been observed. Cloud Software Group strongly urges customers of NetScaler ADC and NetScaler Gateway to install the relevant updated versions of NetScaler ADC and NetScaler Gateway as soon as possible,” reads Citrix’s security bulletin.
Assetnote, in its recent technical root cause analysis, shed light on how CVE-2023-4966 can be weaponized to extract sensitive data from unpatched Citrix appliances. The vulnerability pivots around two functions – `ns_aaa_oauth_send_openid_config` and `ns_aaa_oauthrp_send_openid_config`. Both functions serve the purpose of the OpenID Connect Discovery endpoint and, alarmingly, are accessible unauthenticated.

It’s a seemingly simple flaw in the code’s function. In essence, the function crafts a JSON payload, integrating the device’s hostname. In the unpatched version, the device would promptly dispatch this response. However, in the corrected version, the response is dispatched only if a particular condition is met. The underlying vulnerability stems from how the system gauges the number of bytes sent to the client.
But what makes this flaw so exploitable? Simply put, if a hacker discerns how to get the response to transcend the buffer size of 0x20000 bytes, the application would then furnish the completely filled buffer and the succeeding memory.
“The vulnerability occurs because the return value of snprintf is used to determine how many bytes are sent to the client by ns_vpn_send_response. This is a problem because snprintf does not return how many bytes it did write to the buffer, snprintf returns how many bytes it would have written to the buffer if the buffer was big enough,” the Assetnote said.
As with most zero-days, the real fear isn’t just in the flaw itself but in its exploitation. Mandiant, a reputed cybersecurity firm, divulged that bad actors had been harnessing CVE-2023-4966 since late August 2023 to purloin authentication sessions and commandeer accounts. Such actions could facilitate bypassing multifactor authentication or other stringent auth requisites.
Citrix’s recent warning underscored the gravity of the situation. They reported incidents hinting at session hijacking and authenticated targeted attacks exploiting this vulnerability.
Citrix’s emphasis on the critical nature of this flaw cannot be overstated. They’ve urgently appealed to customers using the vulnerable builds and configurations to swiftly adopt the recommended builds to shield against this potential threat.
Citrix’s acknowledgment that they cannot offer forensic analysis to identify possible system compromises only heightens the urgency. It underscores the unpredictability and potential ramifications of this zero-day.
With a PoC exploit for CVE-2023-4966 now available on Github and this vulnerability being actively exploited, the cybersecurity community and end-users must be ever-vigilant and take swift, informed action to mitigate potential risks.
