Security researchers have disclosed technical details for a Visual Studio Code remote code execution vulnerability (CVE-2023-36742, CVSS score of 7.8) and a public proof-of-concept (PoC) exploit.

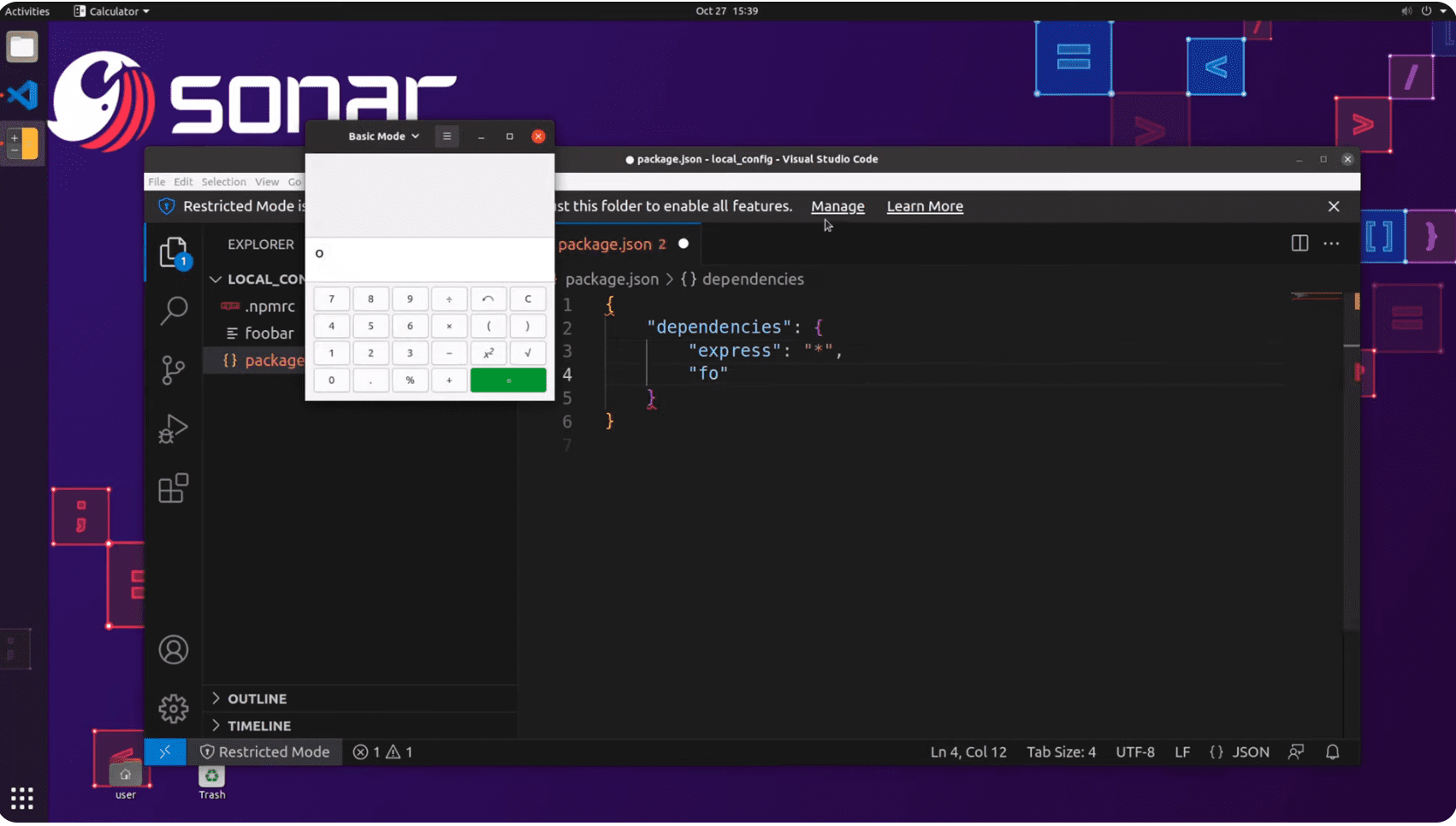
The flaw resides in VS Code versions 1.82.0 and earlier. The vulnerability manifests when working in a maliciously crafted package.json file, resulting in the execution of commands locally. The exploitation scenario unfolds as an attacker entices a VS Code user to open a malicious project and interact with malformed entries in the dependencies sections of the package.json file.
VS Code utilizes the locally installed npm command to fetch information about package dependencies. In this vulnerability, a package dependency can be manipulated such that the npm tool inadvertently runs a script.
In response to this alarming issue, a remedy is available starting with VS Code 1.82.1. The fix (identified as e7b3397) counters this attack by disabling the use of npm in untrusted workspaces and implementing additional input validation when executing the npm command. The fix also advises against working with the dependencies sections in the package.json file from untrusted sources.
Two security researchers, Thomas Chauchefoin and Paul Gerste from SonarSource have disclosed technical details for CVE-2023-36742 and a public proof-of-concept (PoC) exploit. This PoC demonstrates how an attacker can exploit the vulnerability to execute arbitrary code on a vulnerable system.
“The most fascinating aspect was exploiting NPM’s option to alter its global configuration, –globalconfig,” the researchers elucidate in their technical write-up. They describe a scenario where an arbitrary configuration from a local file named description , part of the malicious project, is loaded: npm view –json –globalconfig description dist-tags.latest homepage version time. This method, though not reflecting the constraints of more recent NPM versions or other platforms, demonstrates the potential for leveraging such vulnerabilities to execute arbitrary commands in untrusted workspaces.
To underscore the severity and practicality of this vulnerability, the researchers shared a video demonstrating how this flaw in Visual Studio Code can be exploited. This visual representation not only illustrates the vulnerability but also serves as a stark warning to the development community.
While the researchers acknowledge that the exploit may not be applicable in more recent versions of NPM and other platforms, it underscores the potential for remote code execution attacks in untrusted workspaces. Users are strongly advised to update to the latest version of VS Code (1.82.1 or later) and exercise caution when opening projects from untrusted sources.