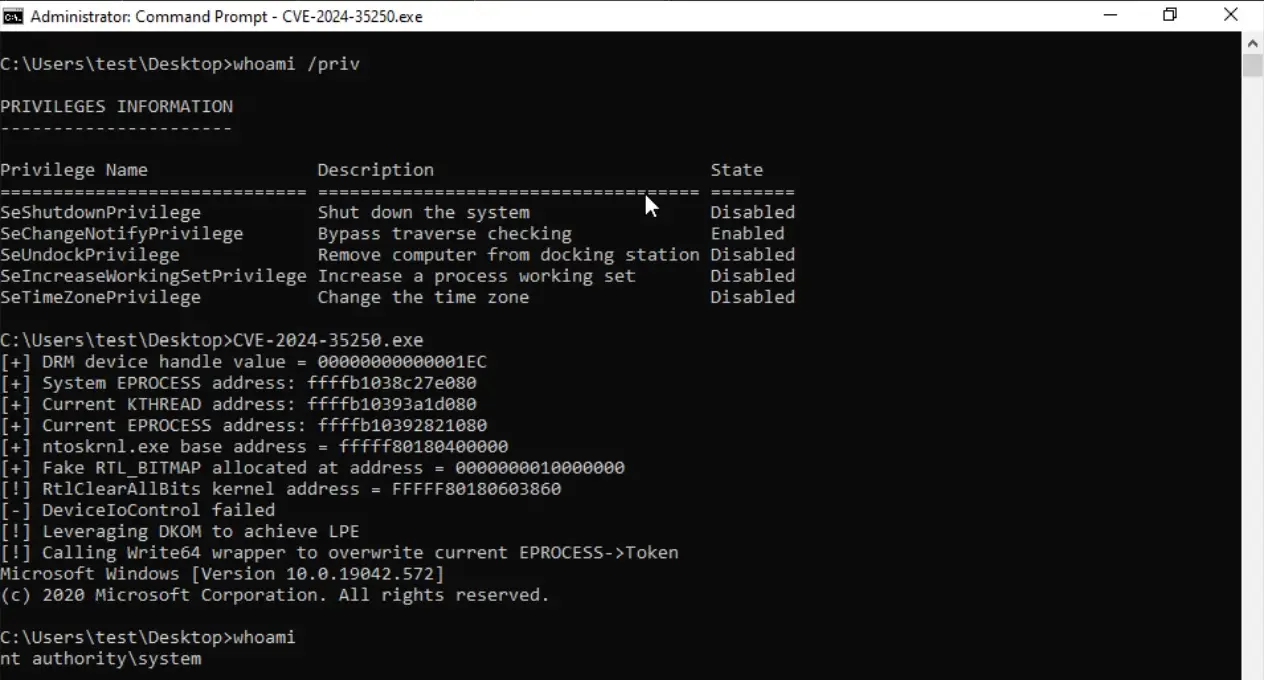
In a detailed analysis by security researcher Angelboy (@scwuaptx) from the DEVCORE Research Team, the critical vulnerability CVE-2024-35250 has been exposed as a significant threat, enabling attackers to gain SYSTEM privileges in Windows. The vulnerability, which affects Windows Kernel-Mode Drivers, was notably used during the Pwn2Own Vancouver 2024 competition, drawing widespread attention due to its severity.
Confirmed! The DEVCORE Team used a couple of bugs, including a somewhat risky TOCTAU race condition, to get their LPE on #Windows 11. They earn $30,000 and 3 Master of Pwn points. #Pwn2Own pic.twitter.com/pP9adGmRs0
— Zero Day Initiative (@thezdi) March 20, 2024
Identified with a CVSS score of 7.8, CVE-2024-35250 allows for an elevation of privilege through the manipulation of the IOCTL_KS_PROPERTY request in Kernel Streaming (ks.sys). As Microsoft explains, “An attacker who successfully exploited this vulnerability could gain SYSTEM privileges,” effectively allowing them to take full control of the affected system.
The vulnerability lies within the handling of property requests in the ks.sys driver. Specifically, when the KSPROPERTY_TYPE_UNSERIALIZESET flag is provided, a series of operations can be initiated that ultimately lead to arbitrary IOCTL calls. During this process, the user-supplied buffer is copied into a newly allocated space and executed without proper validation. Angelboy notes, “We now have a primitive that allows us to perform arbitrary IOCTL_KS_PROPERTY operations,” making this flaw a prime target for privilege escalation attacks.
Once arbitrary calls are achieved, exploiting the flaw becomes a straightforward task. The attacker can utilize a legitimate function to perform an arbitrary write, which can then be leveraged to replace process tokens, thereby granting SYSTEM-level privileges. As Angelboy points out, “Our goal here is straightforward: to create an arbitrary write primitive from a legitimate function, which can then be used to achieve EoP through typical methods like replacing the current process token with system token or abusing the token privilege.”
However, exploitation is not without its challenges. Several security measures, such as Kernel Control Flow Guard (kCFG), Address Space Layout Randomization (ASLR), and Supervisor Mode Execution Prevention (SMEP), need to be bypassed for the attack to succeed. Angelboy explains, “Although protections such as kCFG, kASLR, and SMEP will be encountered, the only protection that needs to be dealt with under Medium IL is kCFG.”
Through extensive research, the DEVCORE team identified the function RtlSetAllBits as a viable option to bypass these protections. This function, part of the legitimate Windows kernel, allows the attacker to manipulate a bitmap structure, thereby creating a write primitive that leads to privilege escalation.
During testing, the exploit was successfully executed in a controlled environment. However, the researchers encountered difficulties when attempting to run the exploit on a Windows 11 23H2 virtual machine (VM) on Hyper-V. As Angelboy recounts, “The result was a failure. It failed at the open device stage.” The issue stemmed from the fact that Hyper-V does not include an audio device by default, which is required to trigger the vulnerability via the KSPROPSETID_DrmAudioStream property.
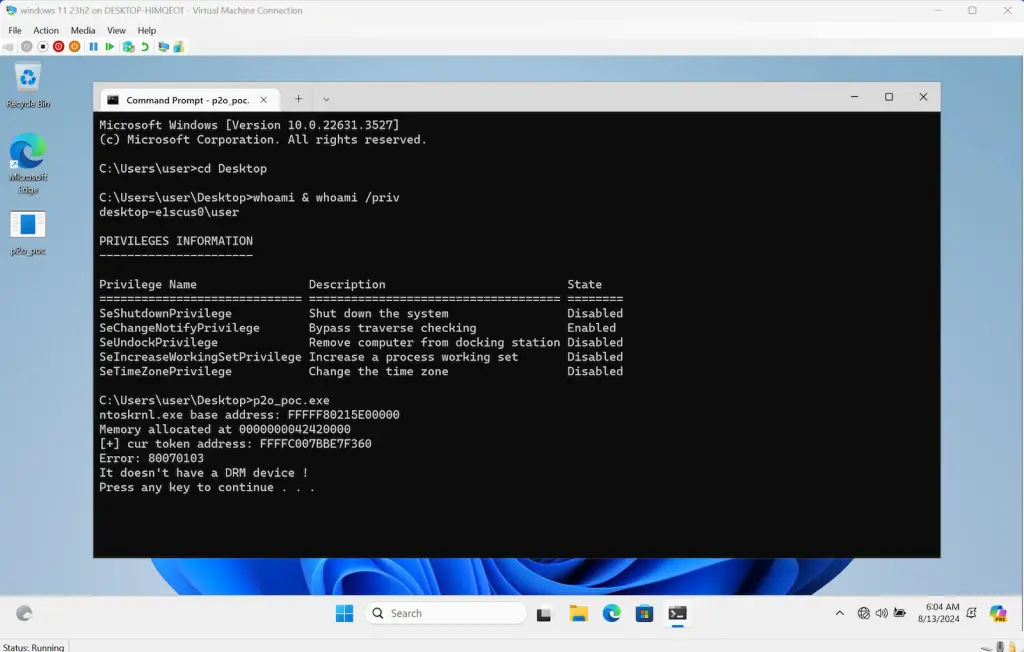
Based on Angelboy’s analysis, security researcher Varwara has released a Proof of Concept (PoC) exploit code to demonstrate the CVE-2024-35250’s impact.
Microsoft addressed this critical flaw in its June 2024 Patch Tuesday update, providing a patch that prevents exploitation of the vulnerability.
Organizations and users are strongly advised to update their systems to mitigate the risks associated with CVE-2024-35250. Additionally, implementing best practices such as enforcing the principle of least privilege, keeping software up to date, and monitoring systems for abnormal behavior can provide further protection against such vulnerabilities.
Related Posts:
- Microsoft December Patch Tuesday: fix 6 zero-day security vulnerabilities
- Microsoft releases January Patch Tuesday to fix 56 security issues
- Microsoft released April Patch Tuesday to fix 67 security issues
