Powermad: PowerShell MachineAccountQuota and DNS exploit tools
Powermad – PowerShell MachineAccountQuota and DNS exploit tools
Functions
- MachineAccountQuota Functions
The default Active Directory ms-DS-MachineAccountQuota attribute setting allows all domain users to add up to 10 machine accounts to a domain. Powermad includes a set of functions for exploiting ms-DS-MachineAccountQuota without attaching an actual system to AD.- Get-MachineAccountAttribute
This function can return values populated in a machine account attribute.
- Get-MachineAccountCreator
This function leverages the ms-DS-CreatorSID property on machine accounts to return a list of usernames or SIDs and the associated machine account. The ms-DS-CreatorSID property is only populated when a machine account is created by an unprivileged user.
- Disable-MachineAccount
This function can disable a machine account that was added through New-MachineAccount. This function should be used with the same user that created the machine account.
- Enable-MachineAccount
This function can enable a machine account that was disabled through Disable-MachineAccount. This function should be used with the same user that created the machine account.
This function can add a new machine account directly through an LDAP add request to a domain controller and not by impacting the host system’s attachment status to Active Directory.
- Remove-MachineAccount
This function removes a machine account with a privileged account.
- Set-MachineAccountAttribute
This function can populate some attributes for an account that was added through New-MachineAccount if a user has to write access. This function should be used with the same user that created the machine account.
- Get-MachineAccountAttribute
- DNS Functions
By default, authenticated users have the ‘Create all child objects’ permission on the Active Directory-Integrated DNS (ADIDNS) zone. Most records that do not currently exist in an AD zone can be added/deleted. - Dynamic Updates Functions
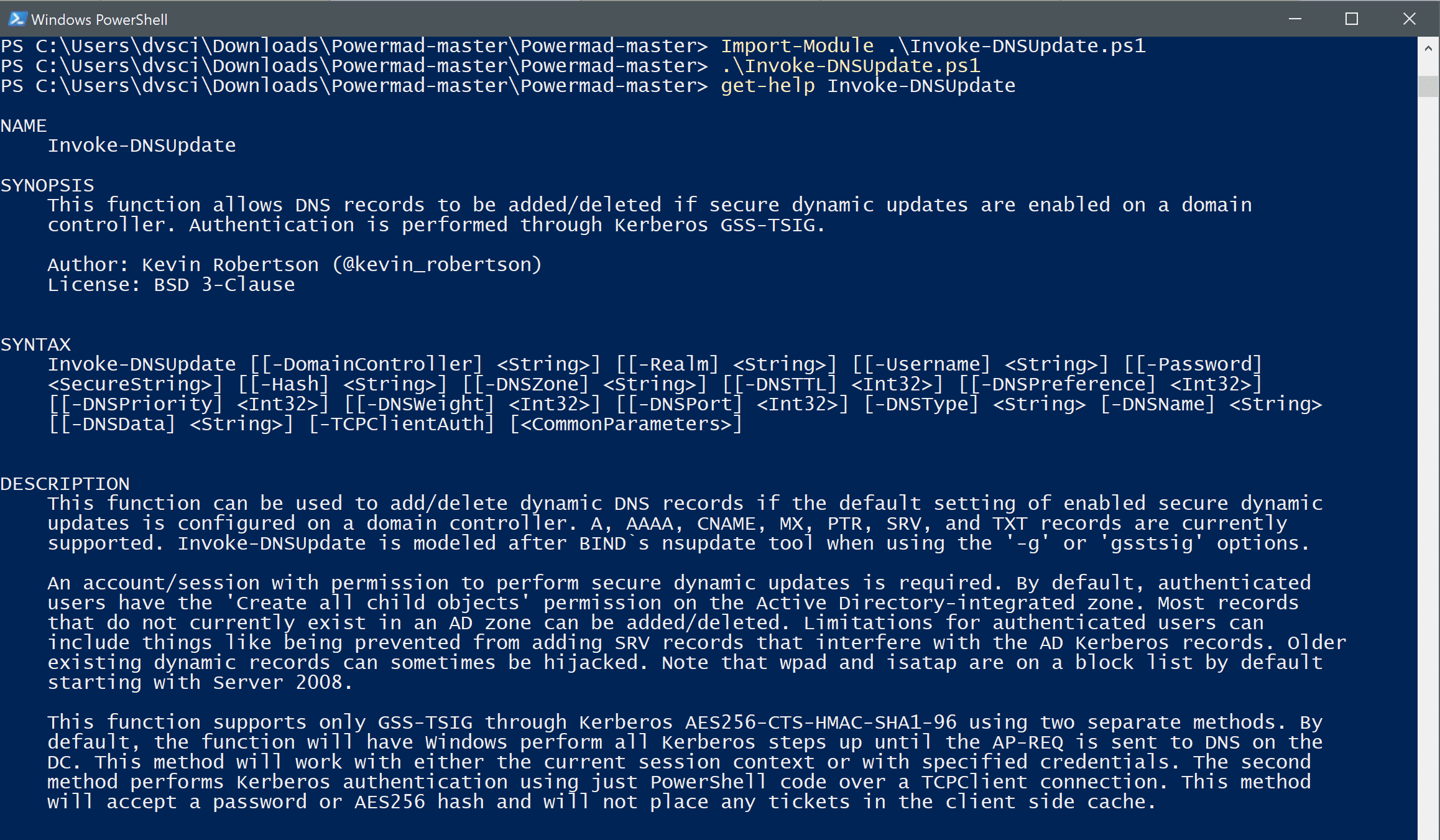
- Invoke-DNSUpdate
This function can be used to add/delete dynamic DNS records if the default setting of enabled secure dynamic updates is configured on a domain controller. A, AAAA, CNAME, MX, PTR, SRV, and TXT records are currently supported. Invoke-DNSUpdate is modeled after BIND`s nsupdate tool when using the ‘-g’ or ‘gsstsig’ options.
- Invoke-DNSUpdate
- ADIDNS Functions
- Disable-ADIDNSNode
This function can tombstone an ADIDNS node.
- Enable-ADIDNSNode
This function can turn a tombstoned node back into a valid record.
- Get-ADIDNSNodeAttribute
This function can return values populated in an DNS node attribute.
- Get-ADIDNSNodeOwner
This function can return the owner of an ADIDNS Node.
- Get-ADIDNSPermission
This function gets a DACL of an ADIDNS node or zone.
- Get-ADIDNSZone
This function can return ADIDNS zones.
- Grant-ADIDNSPermission
This function adds an ACE to an DNS node or zone DACL.
- New-ADIDNSNode
This function adds an DNS node to an Active Directory-Integrated DNS (ADIDNS) Zone through an encrypted LDAP add request.
- New-DNSRecordArray
This function creates a valid byte array for the dnsRecord attribute.
- New-SOASerialNumberArray
This function gets the current SOA serial number for a DNS zone and increments it by the set amount.
- Rename-ADIDNSNode
This function can rename an DNS node.
- Remove-ADIDNSNode
This function can remove an DNS node.
- Revoke-ADIDNSPermission
This function removes an ACE to an DNS node or zone DACL.
- Set-ADIDNSNodeAttribute
This function can append, populate, or overwite values in an DNS node attribute.
- Set-ADIDNSNodeOwner
This function can sets the owner of an DNS Node. Note that a token with SeRestorePrivilege is required.
- Disable-ADIDNSNode
- Miscellaneous Functions
- Get-KerberosAESKey
This function can generate Kerberos AES 256 and 128 keys from a known username and password. This can be used to test pass the hash in invoke-DNSUpdate.
- Get-KerberosAESKey
Download
git clone https://github.com/Kevin-Robertson/Powermad.git
Copyright (c) 2017, Kevin Robertson
All rights reserved.