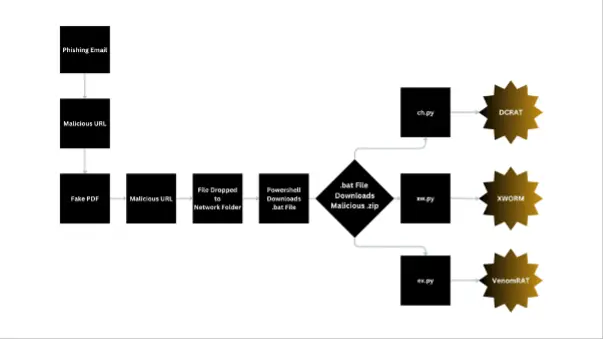
Attack Flow | Image: Cofense
A recent report by Adam Martin and Kian Buckley Maher from the Cofense Phishing Defense Center (PDC) has revealed a sophisticated malware loader, PythonRatLoader, that is being used to distribute various types of remote access trojans (RATs), including XWorm, VenomRAT, AsyncRAT, and DCRat. This loader employs multi-layered obfuscation and evasion techniques to execute complex, damaging attacks on corporate environments, posing a serious risk to any organization targeted by this campaign.
The attack begins with a seemingly legitimate phishing email, posing as a customer service request. The email includes an urgent call to action, pushing the recipient to open a malicious attachment—a “PDF” file that is actually a link to a malicious WebDAV server. According to Cofense, “The email uses urgent language to deceive a victim into clicking a malicious attachment, initiating a series of harmful activities.” Once clicked, the link downloads a file that directs the victim to a remote server, setting off a chain reaction that downloads additional malware components.

The threat actors behind PythonRatLoader have gone to great lengths to evade detection. Upon accessing the WebDAV-hosted “PDF,” a PowerShell script is activated, using stealthy commands to download a batch script (obfuscated with BatchShield) that installs multiple malware payloads. This strategy of layered obfuscation, “gives PythonRatLoader the ability to enter victim systems and cause a serious level of damage,” according to the report. The PowerShell script further downloads a ZIP file, which unpacks several Python scripts into the user’s AppData directory, each prepped to initiate a different RAT payload.
PythonRatLoader’s payloads are highly destructive, leveraging RATs to perform surveillance, data theft, and system exploitation:
- XWorm: The xw.py script spawns a Notepad.exe process and injects it with XWorm’s shellcode. This malware allows attackers to gain full remote control, often connecting back to a command-and-control server undetected.
- VenomRAT: Executed by ex.py, VenomRAT operates similarly, injecting malicious shellcode into a separate Notepad process, creating a backdoor on the victim’s system.
- DCRat: The ch.py script loads DCRat, providing extensive remote capabilities, from keylogging to file exfiltration, while maintaining persistence.
Each RAT operates independently, abusing “a process injection method known as Early Bird APC injection,” which is a stealthy technique for embedding malicious code into system processes. The report explains, “In essence, the script creates a new process (Notepad.exe in this case) and injects the malicious code into it before the thread execution begins.” This tactic ensures that the RATs can operate without detection from standard antivirus software, making them even more challenging to eliminate.
The Cofense PDC urges organizations to bolster email security and increase phishing awareness among employees. Key red flags include unexpected attachments, strange URLs, urgent or emotionally charged language, and unusual email addresses. Additionally, employees should be trained to identify suspicious emails, as “the initial infection vector continues to be very well-crafted phishing emails that, through their perceived innocuous nature, lull users into a false sense of security.”
Related Posts:
- Windows Sandbox Gets Supercharged: Clipboard and File Sharing Arrive
- CVE-2024-4947: New Chrome 0-Day Vulnerability Under Active Exploitation
- Stealthy New Android Trojan Disguised as Popular Apps Steals Your Data
- Apache Answer Flaws: XSS, DoS Attacks Possible – Update Urgently