Red Team Arsenal v1.0: web/network security scanner
Red Team Arsenal is a web/network security scanner which has the capability to scan all company’s online facing assets and provide a holistic security view of any security anomalies. It’s a closely linked collection of security engines to conduct/simulate attacks and monitor public-facing assets for anomalies and leaks.

It’s an intelligent scanner detecting security anomalies in all layer 7 assets and gives a detailed report with integration support with Nessus. As companies continue to expand their footprint on the INTERNET via various acquisitions and geographical expansions, human-driven security engineering is not scalable, hence, companies need feedback driven automated systems to stay put.
Installation
Prerequisites:
There are a few packages which are necessary before proceeding with the installation:
- Git client: sudo apt-get install git
- Python 2.7, which is installed by default in most systems
- Python pip: sudo apt-get install python-pip
- MongoDB: Read the official installation guide to install it on your machine.
git clone https://github.com/flipkart-incubator/RTA.git
cd RTA
python install/install.py
Integrating Nessus:
Integrating Nessus into Red Team Arsenal can be done is simple 3 steps:
- Download and install Nessus community edition (if you don’t have a paid edition). If you already have an installation (it can be remote installation as well), then go to step (2).
- Update the config file (present in the root directory of RTA) with Nessus URL, username and password.
- Create a Nessus policy where you can configure the type of scans and plugins to run and name it RTA (Case sensitive – use full uppercase).
- Once the config file has the correct Nessus information (url, username, password), use the flag –nessus while running RTA to launch Nessus scan over the entire subdomains gathered by RTA (one single scan initiated with all the subdomains gathered).
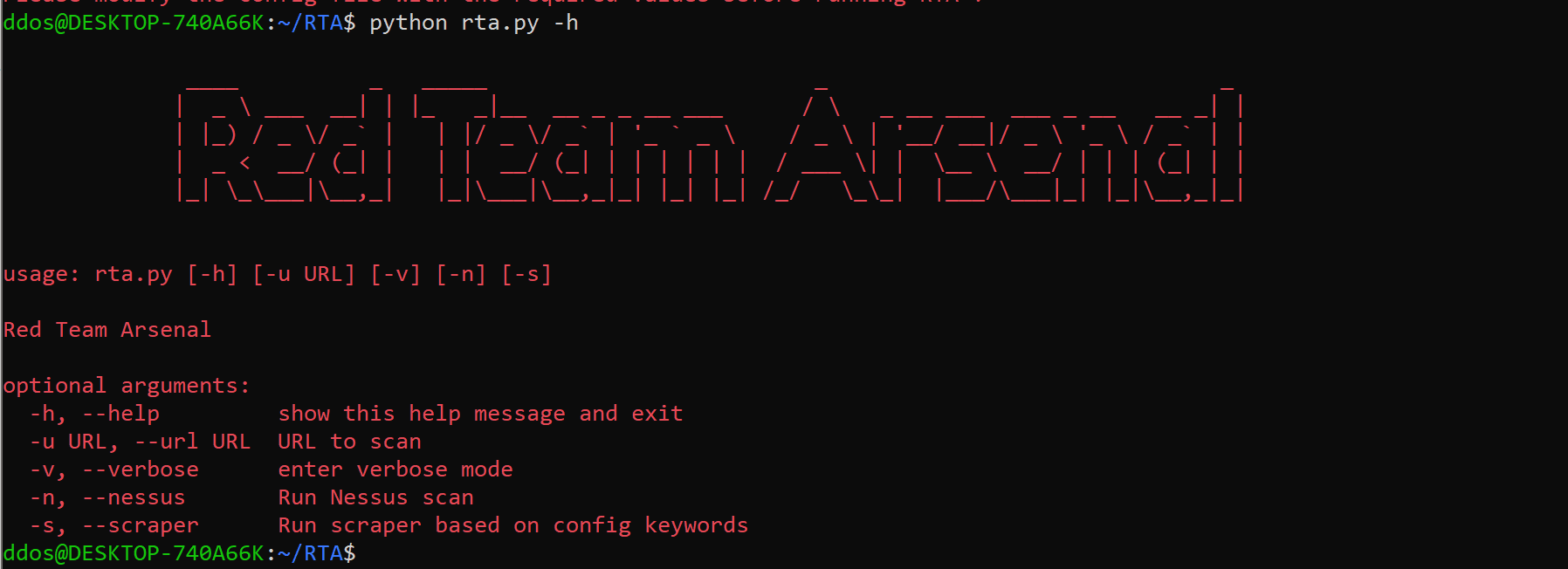
Usage
Copyright (2018) a0xnirudh





