
Zscaler ThreatLabz has identified a new malware family, RiseLoader, which specializes in downloading and executing second-stage payloads. Sharing similarities with RisePro, this loader appears to be the work of the same threat actor group responsible for RisePro and PrivateLoader.
First observed in October 2024, RiseLoader marks an evolution in malware loaders with its focus on streamlined delivery and execution of payloads. Notably, it emerged shortly after RisePro’s development was discontinued, as the threat actor behind it announced on Telegram in June 2024. Zscaler ThreatLabz states: “Due its distinctive focus and similarities with RisePro’s communication protocol, we named this new malware family RiseLoader.”
The security community believes that RiseLoader fills the void left by RisePro, targeting similar victims and delivering payloads like Vidar, Lumma Stealer, XMRig, and Socks5Systemz.
RiseLoader adopts advanced anti-analysis measures to complicate detection:
- VMProtect Packing: Most samples are protected with VMProtect, making reverse-engineering challenging.
- String Obfuscation: Strings related to debugging tools (e.g., processhacker.exe, ollydbg.exe, ida.exe) are embedded globally but unused in execution, hinting at future enhancements.
- Mutex-Based Execution Control: RiseLoader creates a unique mutex like
winrar8PROMEMEKGAmaV3_2_8to ensure single execution per infected host.
Zscaler explains: “The mutex name will be a combination of three strings… If the mutex exists, RiseLoader will terminate.”
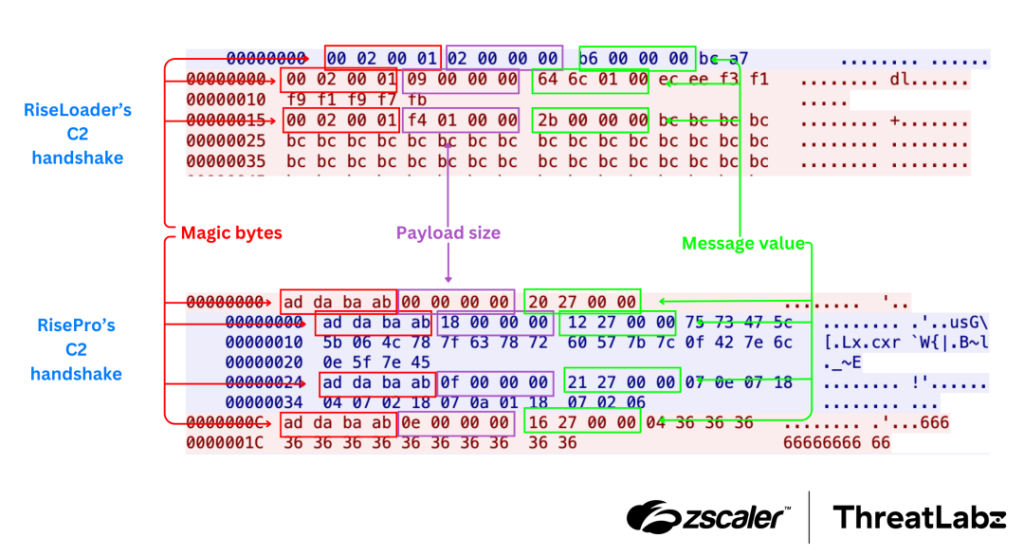
Once executed, RiseLoader establishes communication with a command-and-control (C2) server using a custom TCP-based binary protocol, reminiscent of RisePro. It follows this process:
- C2 Communication Initialization: RiseLoader connects to one of several hardcoded C2 servers. After a successful handshake, the server sends XOR keys for message encryption.
- Payload Processing: RiseLoader retrieves a list of payload URLs in JSON format, downloads the files, and executes them. DLL payloads are launched via rundll32, while executables are started as new processes.
- Registry-Based Infection Marker: A registry key (
HKEY_CURRENT_USER\SOFTWARE\dmdsaodgmarksmdkgsa) acts as an infection marker to avoid redundant executions.
The downloaded payloads often include well-known malware families such as Vidar and Lumma Stealer, continuing the behavior observed in PrivateLoader.
RiseLoader’s C2 protocol is strikingly similar to RisePro. Both rely on XOR-encrypted JSON messages and a consistent binary structure. Zscaler highlights the shared components: “The message structure is very similar: magic bytes, followed by a 4-byte payload size, and a 4-byte command type.”
Key message types exchanged include:
- SEND_VICTIM_INFO (0x2B): Sends information about cryptocurrency wallets, browser extensions, and system details.
- SYS_INFO (0x2F): Sends system metadata, including Windows version and architecture.
- PAYLOADS (0x4DCF): Contains URLs and parameters for payload downloads.
- KEEPALIVE (0x6B5): Ensures the connection remains active.
- SEND_SHUTDOWN (0x1CCD): Instructs RiseLoader to terminate execution.
In addition to its payload delivery role, RiseLoader scans infected systems for information related to cryptocurrency wallets and financial tools. Targeted artifacts include browser extensions, wallet directories, and system data, which are transmitted to the C2 server for further exploitation.
Zscaler notes: “RiseLoader collects information about installed applications and browser extensions related to cryptocurrency.”
While RiseLoader shares payload targets with PrivateLoader, its network protocol and behavior are far more aligned with RisePro. Both loaders exhibit similar initialization processes, message structures, and communication protocols, leading Zscaler to conclude: “These overlaps may indicate that the same threat actor is behind both malware families.”
Related Posts:
- Zscaler found 150 Android apps infected with Windows malware
- Zscaler Report: 300% increase in phishing attacks delivered over SSL
- AI Powers a Phishing Frenzy – Zscaler Report Warns of Unprecedented Threat Wave
- Researchers release the technical analysis & PoC for Windows 0-Day CVE-2022-37969 Flaw
- Dark Angels Ransomware Gang Reaps Record $75 Million Payout
