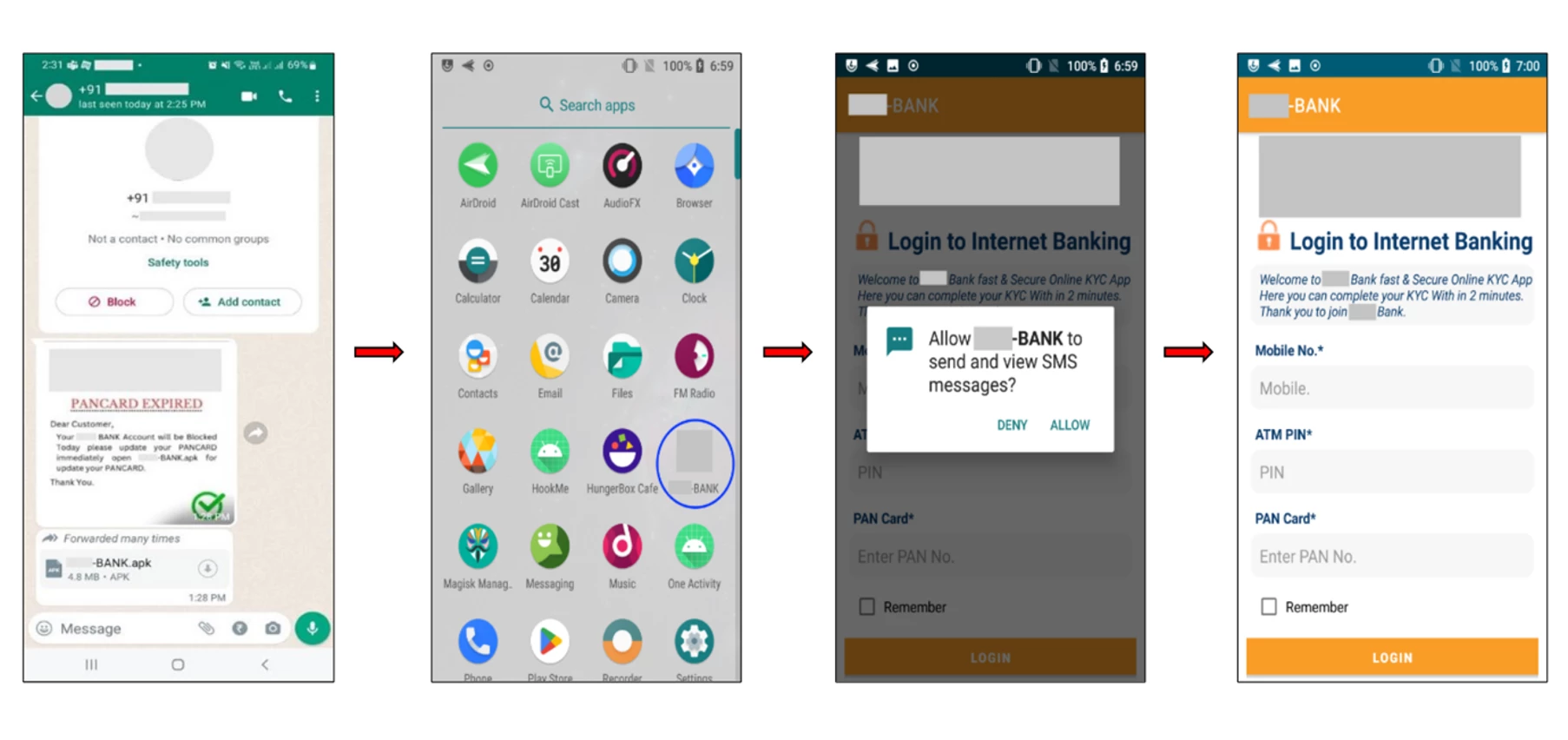
Once installed on a device, the fake app asks users to allow SMS permissions and to sign-in to internet banking and submit their mobile number, ATM pin, and PAN card to update KYC.
Microsoft’s recent observations highlight an ongoing surge in mobile banking trojan campaigns in India. Cybercriminals are exploiting social media platforms like WhatsApp and Telegram, sending crafty messages that entice users to install malicious applications. These applications, masquerading as legitimate services from banks, government entities, and utility companies, aim to filch a wide array of sensitive user information, including personal details, banking credentials, and payment card data.
Mobile malware infections, though not a novel threat, continue to pose significant risks. Users face unauthorized access to personal data, financial losses from fraudulent transactions, privacy breaches, reduced device performance, and potential data theft or corruption. Similar campaigns in the past have employed malicious links to trick users into downloading these dangerous apps, as detailed in the blog “Rewards plus: Fake mobile banking rewards apps lure users to install info-stealing RAT on Android devices.”
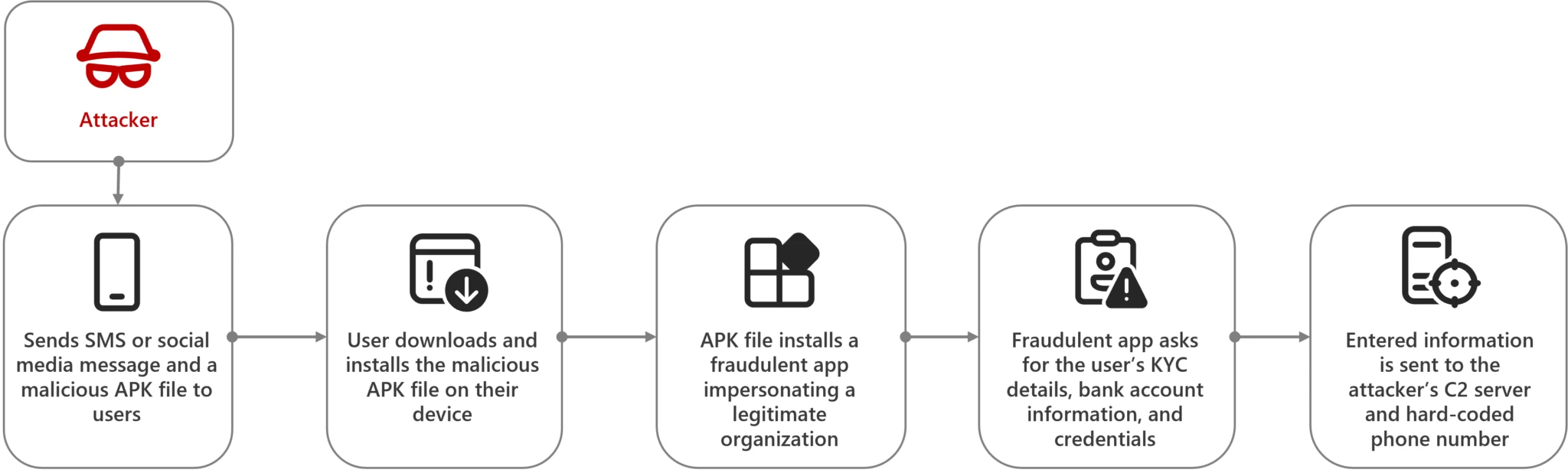
The latest active campaigns have shifted tactics, directly sharing malicious APK files with users in India. Microsoft Threat Intelligence team uncovered two such applications, falsely claiming to be official banking apps. These fraudulent apps exploit social engineering tactics by imitating legitimate financial institutions, though these banks themselves are not directly affected by these attacks.
One particular case involved a WhatsApp phishing campaign distributing a banking trojan. A message prompted users to update their PAN card details through a provided APK file, which, upon installation, impersonated an official bank KYC application. The app sought sensitive user information, transmitting it to a command and control server and an attacker’s phone number.
The fake app’s interface mimicked a legitimate bank application, initially requesting SMS permissions and then banking details under the guise of an online KYC process. The app even simulated a multifactor authentication process, further deceiving users into believing in its legitimacy.

Similar campaigns have used the names of known institutions as app file names to target mobile users in India. These campaigns leverage social media to spread their fraudulent apps, choosing well-known institutions to create a false sense of security among users.
Mobile banking trojan infections can significantly endanger users’ personal and financial security. Awareness of the risks and common tactics used by these trojans is crucial in identifying and mitigating their impact.
Signs of a potential infection include unfamiliar apps, increased data usage, unauthorized transactions, device crashes, and unusual app behavior. To guard against these threats, we recommend:
- Installing apps only from trusted sources like the Google Play Store or Apple App Store.
- Avoiding unknown links from ads, SMS, emails, or untrusted sources.
- Utilizing mobile security solutions like Microsoft Defender for Endpoint on Android.
- Keeping the “Install unknown apps” setting disabled on Android devices.