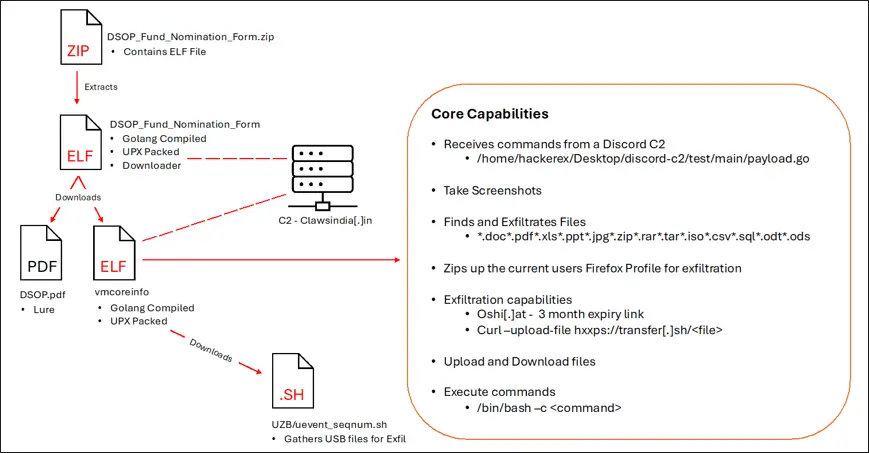
DSOP_Fund_Nomination_Form attack chain and core capabilities
The BlackBerry Threat Research and Intelligence Team has revealed a sustained campaign by Pakistani-based cyber espionage group Transparent Tribe (APT36) targeting critical Indian government, defense, and aerospace sectors. The attacks, which span from late 2023 to April 2024, demonstrate a notable evolution in the group’s tactics, techniques, and procedures (TTPs).

Evolving Toolkit and Techniques
Transparent Tribe, also known as ProjectM, Mythic Leopard, and Earth Karkaddan, has a notorious history of cyber espionage against India. In their recent campaigns, the group has shown significant adaptation and evolution in their attack vectors and tools. They have increasingly relied on cross-platform programming languages such as Python, Golang, and Rust, and have exploited popular web services like Telegram, Discord, Slack, and Google Drive to evade detection and enhance their operational capabilities.
Recent Discoveries
BlackBerry’s investigation revealed multiple artifacts that substantiate the attribution to Transparent Tribe. Key evidence includes a file served from the group’s infrastructure that sets the time zone variable to “Asia/Karachi,” and a remote IP address linked to a Pakistani-based mobile data network operator embedded within spear-phishing emails.
New Attack Vectors
In October 2023, Transparent Tribe began using ISO images as a new attack vector. They have also developed a new Golang compiled “all-in-one” espionage tool capable of exfiltrating files with popular extensions, taking screenshots, and executing commands. This tool exemplifies their strategic shift towards more versatile and robust cyber-espionage capabilities.
Technical Analysis
The group’s recent campaign involved sophisticated tactics and new iterations of their tools. For instance, the Poseidon payload, a Golang agent, is designed for use with open-source cross-platform red teaming frameworks. They also deployed Python downloader scripts compiled into ELF binaries, with minimal detection rates due to their lightweight nature.
Furthermore, Transparent Tribe has utilized a Python-based Windows downloader, equivalent to their Linux counterparts, demonstrating their cross-platform proficiency. This downloader sets up executables to run at startup, maintaining persistence on the compromised systems.
Strategic Targeting
The primary focus of Transparent Tribe’s recent campaign has been on India’s defense forces and state-run defense contractors. Their spear-phishing campaigns have targeted key stakeholders and clients of the Department of Defense Production (DDP), aiming to infiltrate and gather intelligence on India’s defense capabilities.
Geopolitical Context
The ongoing conflict and heightened tensions between India and Pakistan provide a backdrop for these cyber espionage activities. Transparent Tribe’s strategic targeting of critical sectors aligns with the interests of Pakistan, suggesting a state-aligned motive behind their operations.
Impact and Concerns
The campaign highlights the evolving sophistication and adaptability of Transparent Tribe, posing a significant threat to Indian national security. The group’s focus on defense and aerospace sectors could jeopardize sensitive information and critical infrastructure.