TrustJack
bypassing UAC with DLL Hijacking technique
DLL Hijacking is a popular technique for executing malicious payloads. Attackers have been seen to use DLL hijacking in different ways and for different reasons. Motives include execution (executing malicious code through a trusted executable may be less likely to set off alarm bells, and in some cases even bypasses application whitelist features such as AppLocker [1]), obtaining persistence (if the target application is pre-installed and runs regularly, so will the malicious code) and privilege escalation (if the target application runs under elevated permissions, so will the malicious code).
Use
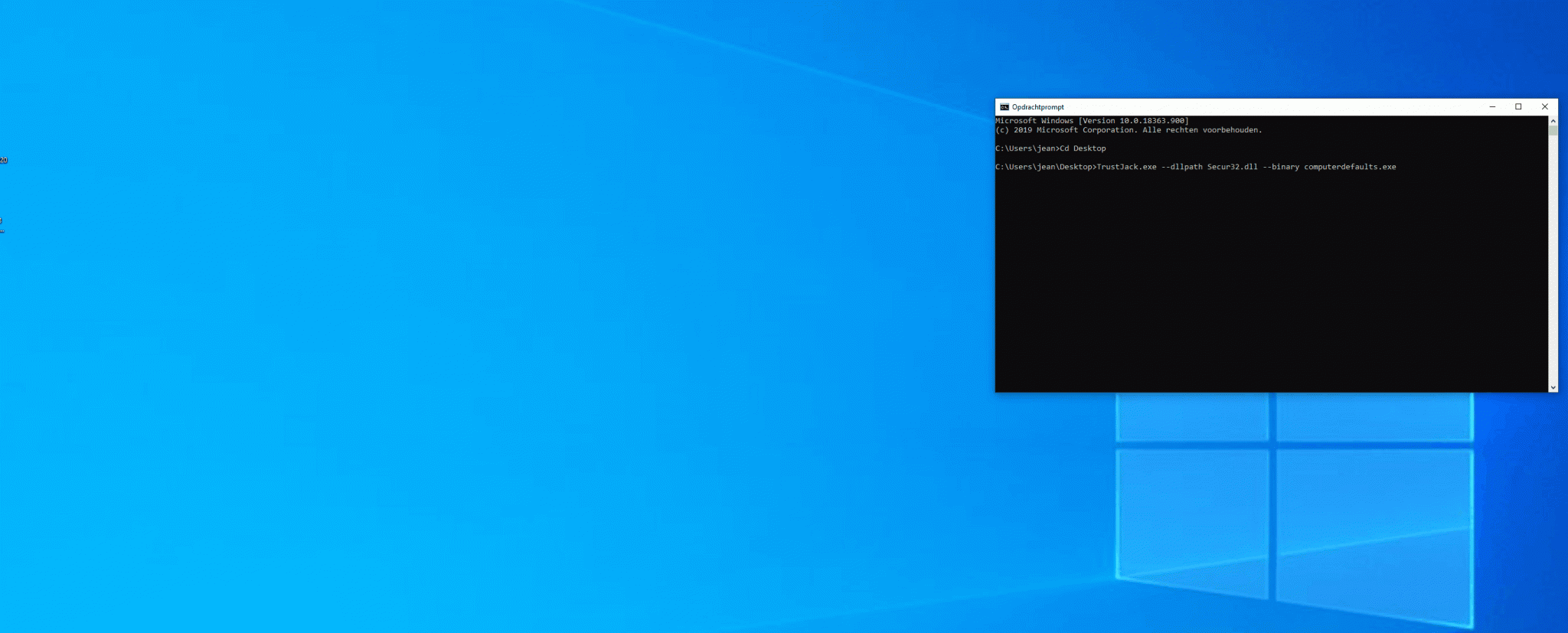
To be used with a cmd that does whatever the F you want, for a dll that pops cmd, hang tight. gonna upload my cmd dll soon. check the list in wietze’s site to check how you should call your dll.
will automatically create c:\Windows \System32 and drop your dll and chosen binary in there, followed by execution. Clean up after yourself by running trustjack again with the -c flag.
You might be missing fody 2.0, run NuGet package restore to fix (right-click Solution ‘TrustJacker’ and select ‘restore NuGet packages’)
Download
Copyright (C) 2020 jfmaes