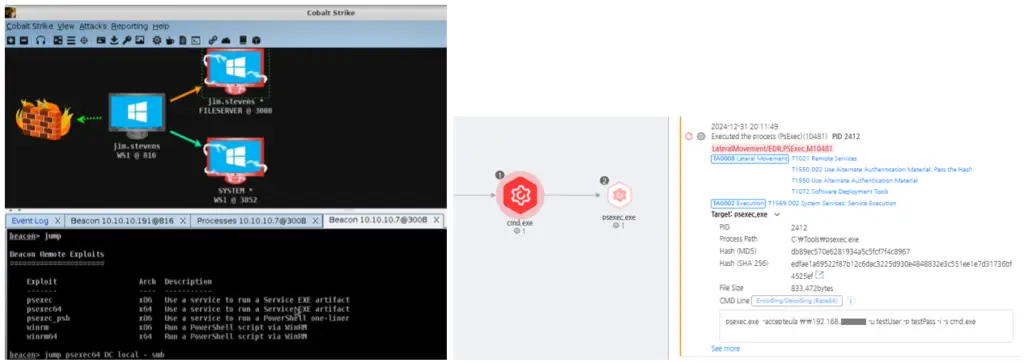
EDR detection of threat actor attack actions used in the Lateral Movement phase | Source: AhnLab
Play ransomware, also known as Balloonfly or PlayCrypt, has emerged as a significant cyber threat since its discovery in June 2022. Responsible for over 300 global attacks, this ransomware encrypts files and appends them with the “.PLAY” extension. It follows the double extortion model, stealing sensitive data before encrypting systems to pressure victims into paying ransom.
A notable revelation about Play ransomware is its collaboration with the Andariel group, a North Korean threat actor. According to AhnLab’s analysis, “The Andariel group utilized malware known as Sliver and DTrack to steal information, and then a Play ransomware attack was carried out using the same attack infrastructure.” The Andariel group’s history of leveraging ransomware like SHATTEREDGLASS and Maui underscores the evolving sophistication of Play ransomware operations.
Play ransomware actors exploit vulnerabilities in widely used systems and misuse legitimate accounts to gain initial access. Vulnerabilities like ProxyNotShell (CVE-2022-41040, CVE-2022-41082) in MS Exchange Server and flaws in FortiOS (CVE-2020-12812, CVE-2018-13379) are frequently targeted. AhnLab highlights, “Threat actors gain initial access to organizations by exploiting vulnerabilities or abusing compromised accounts.”
Attack Phases and Techniques
- Discovery: The attackers conduct network reconnaissance using tools like NetScan, Nltest, and AdFind to map the environment. AhnLab notes, “BloodHound is a tool that collects Active Directory domain-related information and helps identify attack paths for privilege escalation.”
- Privilege Escalation: Tools such as WinPEAS, an open-source script, are employed to identify and exploit vulnerabilities for administrative privileges.
- Credential Access: Threat actors use Mimikatz and even abuse legitimate processes like Task Manager to extract credentials from memory. “Suspicious tools like Mimikatz are key detection targets for security products,” the report emphasizes.
- Command and Control: Remote management tools like AnyDesk and proxy tools such as Plink are leveraged to maintain control over infected systems. Even legitimate tools are exploited, complicating detection.
- Lateral Movement: Using stolen credentials, attackers spread through the network using tools like Cobalt Strike and PsExec, executing malicious payloads on remote systems.
- Defense Evasion: Legitimate tools such as Process Hacker and GMER are exploited to disable security defenses. AhnLab reports, “These tools are frequently used for legitimate purposes, it can be challenging for anti-malware solutions to detect and block them.”
- Data Exfiltration and Encryption: Before encryption, sensitive information is compressed using WinRAR and exfiltrated via tools like WinSCP. A ransom note, “ReadMe.txt,” provides contact details and a Tor link for negotiations.
Organizations must prioritize patching known vulnerabilities, implementing robust security tools, and fostering awareness to mitigate risks effectively.
Related Posts:
- Hackers Exploit Google Ads to Spread Malware Disguised as Popular Software
- LockBit Ransomware: The Hidden Threat in Resume Word Files
- Hackers Weaponize Popular Software Framework for Stealthy Data Theft
- North Korean Hackers Exploit VPN Vulnerabilities to Breach Networks