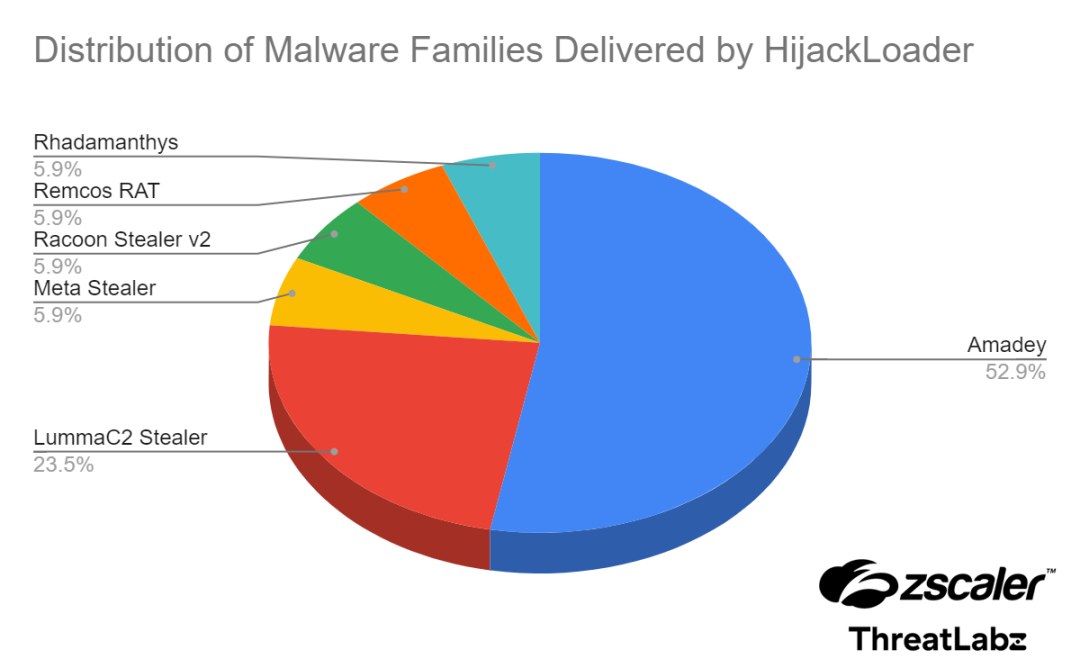
A pie chart showing the different malware families distributed by HijackLoader
Security researchers at Zscaler’s ThreatLabz have uncovered significant updates to the HijackLoader malware, making it far more stealthy and dangerous. These new capabilities are designed to evade detection by antivirus and security software, allowing it to operate undetected on infected systems for longer periods.
Key Developments in HijackLoader:
- Modular Architecture: Unlike traditional malware loaders, HijackLoader operates on a modular system, allowing for dynamic adaptation and customization based on the attack environment.
- Enhanced Evasion Techniques: The latest updates include modules that specifically bypass common security measures like Windows Defender Antivirus, User Account Control (UAC), and API hooking—techniques frequently used by cybersecurity software to detect threats.
- Process Hollowing: This technique involves the exploitation of legitimate processes to execute malicious activities discreetly, further camouflaging HijackLoader’s presence within the system.
Innovative Malware Delivery:

- Image-based Malware Distribution: HijackLoader now uses a PNG image as a trojan horse to decrypt and parse payloads. This method is particularly stealthy as it blends in with regular web traffic, reducing the chances of detection.
- Diverse Malware Family Deployment: From March to April 2024, ThreatLabz identified multiple instances where HijackLoader was used to deploy various malware families, including Amadey, Lumma Stealer, Racoon Stealer v2, and Remcos RAT.
Prevalence of Distributed Malware:

- Amadey: Most frequently delivered malware, accounting for 52.9% of HijackLoader activities. This Trojan collects system information and can download additional malware.
- Lumma Stealer and Racoon Stealer v2: These stealers target sensitive information like passwords, cookies, and cryptocurrency wallet data.
- Remcos RAT: Provides attackers with remote access capabilities, turning infected systems into potential launch pads for further attacks.
Python Script for Malware Analysis
To aid the cybersecurity research community, ThreatLabz has developed a Python script that decrypts and decompresses the second stage of the HijackLoader, allowing for deeper analysis of its components and behaviors. This script is available on their GitHub repository.
Conclusion
HijackLoader’s evolution represents a significant shift in the landscape of cyber threats, with its ability to stay undetected for prolonged periods posing a formidable challenge to existing security frameworks. Its use of a PNG image to obscure its payload delivery is a testament to the innovative tactics employed by cybercriminals to bypass traditional defenses.