
A new report from Trend Micro has revealed that ShadowPad, a modular malware with deep ties to Chinese threat actors, has evolved into a more dangerous cyber threat, now facilitating ransomware attacks. The report highlights two recent incident response cases in Europe where ShadowPad was used to infiltrate organizations, followed by the deployment of a previously unreported ransomware family—an unusual tactic for attackers leveraging this malware.
Initially discovered in a 2017 supply chain attack, ShadowPad has been linked to several Chinese state-sponsored actors, including APT41, Earth Baku, Earth Longzhi, and Earth Freybug. Traditionally used for cyber espionage, this malware has now been spotted aiding in ransomware deployment, raising concerns about its evolving capabilities.
According to Trend Micro, 21 companies across 15 countries in Europe, Asia, the Middle East, and South America have been targeted in the last seven months, with the manufacturing industry being the hardest hit. More than half of the victims belong to this sector.
“We don’t know the ultimate goal of the threat actor. However, it is possible that some of this targeting is related to intellectual property theft,” Trend Micro stated.
The infection chain in the investigated incidents involved remote network attacks where adversaries gained access through:
- Weak Administrative VPN Passwords: Threat actors logged into VPN accounts with weak or compromised credentials.
- Bypassing Multi-Factor Authentication (MFA): In one case, attackers bypassed certificate-based MFA, possibly by obtaining a valid certificate before the attack.
- Brute-Force Attacks: In another case, traces of brute-force attacks were found, though it remains unclear if they were responsible for the initial compromise.
Once inside the victim’s network, attackers deployed ShadowPad, often on the domain controller, ensuring they had extensive control over the infrastructure. From there, the malware facilitated data theft, credential harvesting, and lateral movement before deploying ransomware on select victims
The latest ShadowPad variant exhibits advanced anti-analysis techniques and improvements designed to evade security tools. Key upgrades include:
- Enhanced Anti-Debugging Measures: The malware now terminates itself if debugging is detected using techniques such as checking the Process Environment Block (PEB), CPU cycle comparisons, and GetThreadContext Windows API checks.
- Registry-Based Encryption: The ShadowPad payload is now encrypted using the volume serial number to ensure it remains unique to each infected machine.
- DNS over HTTPS (DoH) Support: This feature hides C2 communications, making it harder for security teams to monitor network activity
“While these features are not major enhancements of the malware itself, they show that the malware is in active development and that its developers are willing to make their malware nalysis harder,” Trend Micro warned.
The new ransomware family, linked to ShadowPad, employs a three-stage loading mechanism:
- Legitimate Signed Executable (e.g., usysdiag.exe signed by Beijing Huorong Network Technology Co., Ltd.).
- Malicious Side-Loaded DLL (sensapi.dll).
- Encoded Ransomware Payload (usysdiag.dat).
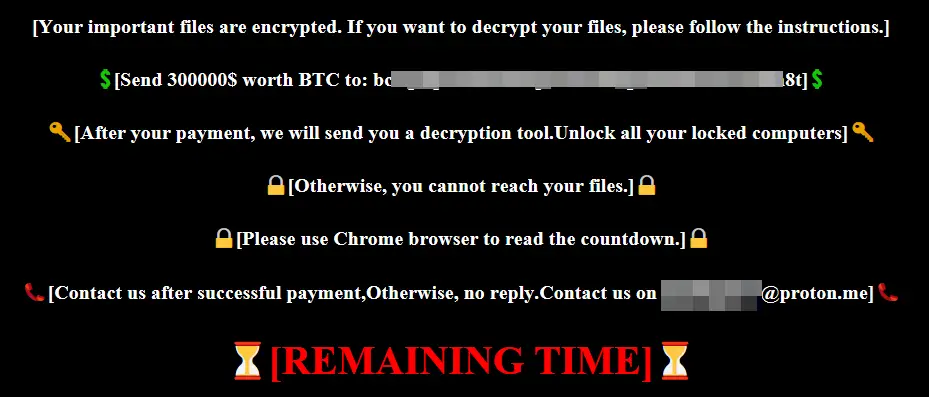
Once executed, the ransomware encrypts all files, except for system-critical extensions (.EXE, .DLL, .SYS) and directories (Windows, Program Files, AppData). The ransomware renames encrypted files with the .locked extension and drops a ransom note directing victims to a fake Kodex Evil Extractor tool ransom page.
Interestingly, Trend Micro found no cryptocurrency transactions linked to these attacks, suggesting that no victims paid the ransom.
Attackers also deployed CQHashDumpv2 and Impacket’s WmiExec to collect credentials and move laterally within the networks. Additionally, they dumped Active Directory databases to retrieve credentials for future exploitation.
Infrastructure analysis uncovered a single Command-and-Control (C2) domain—updata.dsqurey[.]com—which has been associated with multiple ShadowPad loaders in recent campaigns.
“Knowledge of the updating approaches and the targeting of actors of this caliber are critical for companies that may consider themselves of interest to such adversaries,” Trend Micro emphasized.
Related Posts:
- Persistent Espionage Attacks on National Infrastructure Raising Alarm
- Cybercriminals have been earned over $16 million by distributing ransomware for 2 years
- Trend Micro Linux-based Email Encryption Gateway exist multiple security vulnerabilities
- LockBit Imposter: New Ransomware Leverages AWS for Attacks