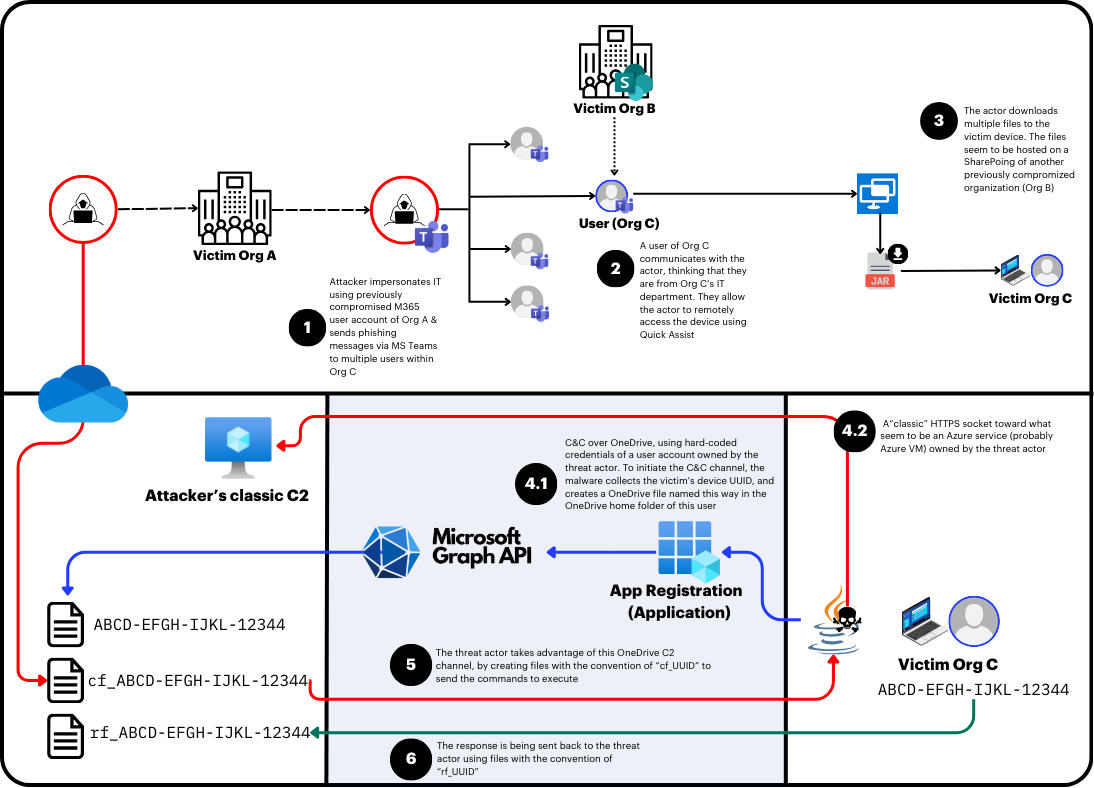
Attack Diagram | Image: Hunters
The cybersecurity team at Hunters, AXON, recently uncovered an ongoing threat campaign called VEILDrive that leverages Microsoft services for command and control (C2). Utilizing Microsoft’s SaaS suite—including Teams, OneDrive, SharePoint, and Quick Assist—the attackers embedded C2 functionality within custom malware, allowing them to discreetly control infected systems within compromised environments. Team AXON’s report indicates a likely Russian origin for the campaign and reveals how the attackers cleverly exploited Microsoft’s trusted infrastructure to bypass detection.
The report notes that the attackers’ reliance on Microsoft’s SaaS products complicates detection efforts. “This SaaS-dependent strategy complicates real-time detection and bypasses conventional defenses,” Team AXON explained, emphasizing how leveraging a trusted platform like OneDrive for C2 makes the attack challenging to detect and prevent.
The attackers initiated their attacks by impersonating IT personnel and sending spear-phishing messages via Microsoft Teams. According to the report, “the attacker impersonated an IT team member and requested access to each employee’s device via the Quick Assist remote utility tool,” targeting non-technical employees for easier exploitation. Once granted access through Quick Assist, the attacker guided the victim to download a malicious file hosted on a separate organization’s SharePoint. This clever multi-layered approach enabled the attacker to move laterally within the target environment while evading conventional monitoring systems.
VEILDrive’s malware, a Java-based .jar file named Cliento.jar, contained two main C2 mechanisms. The first was a traditional HTTPS socket, while the second utilized OneDrive as a C2 platform in a more complex setup:
- OneDrive C2 Functionality: The OneDrive-based C2 system uses three file types—
UUID,cf_UUID, andrf_UUID—to manage communications with the infected device. The malware creates unique files in the victim’s OneDrive account, using them to execute commands, retrieve files, and signal the completion of tasks. As AXON described, “The ‘odRun’ function…includes the creation of a OneDrive connection using the ‘Odconnect’ function as a first step.” - Dynamic Command Execution via Microsoft Graph API: The malware leverages the Microsoft Graph API to facilitate the exchange of commands and results between the attacker and the infected device. This integration with a legitimate API allowed the malware to operate inconspicuously, blending into normal cloud-based activity.
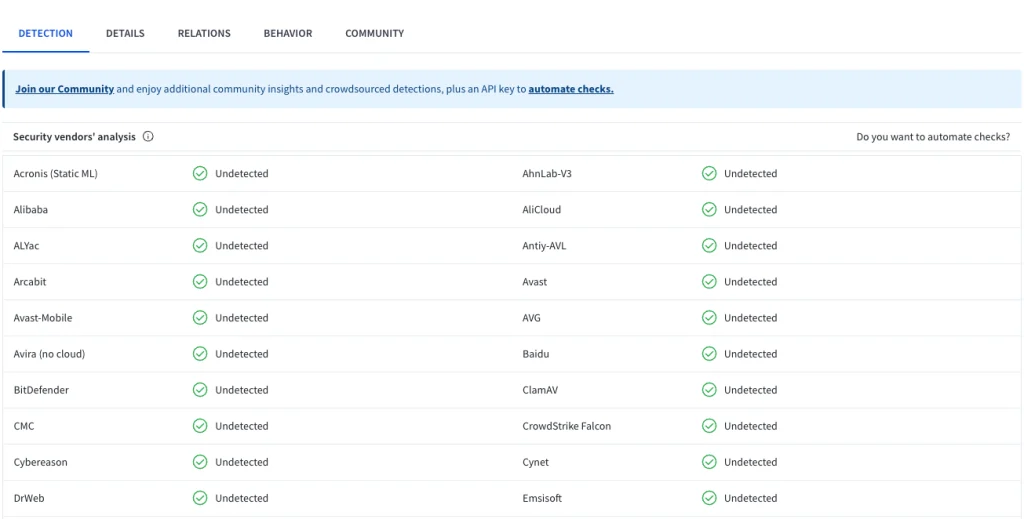
Despite its lack of obfuscation and straightforward code structure, the malware proved remarkably evasive. “The malware evaded detection by a top-tier Endpoint Detection and Response (EDR) tool and all security engines in VirusTotal,” as reported by AXON. This simplicity allowed the malware to fly under the radar, demonstrating that even non-complex code can evade sophisticated defenses if placed within trusted infrastructures like Microsoft’s services.
The team at AXON has since notified Microsoft and affected organizations, sharing actionable intelligence to prevent further exploitation.
Related Posts:
- OneDrive Users Targeted in Sophisticated Phishing and Downloader Campaign
- Double Trouble: DDoS and Internal Errors Cause Major Microsoft Azure Outage
- Microsoft adds ransomware protection and file recovery features to OneDrive