Visual Basic GUI: A Tool to Inject Keystrokes on a SSH Client via an X11 Forwarded Session
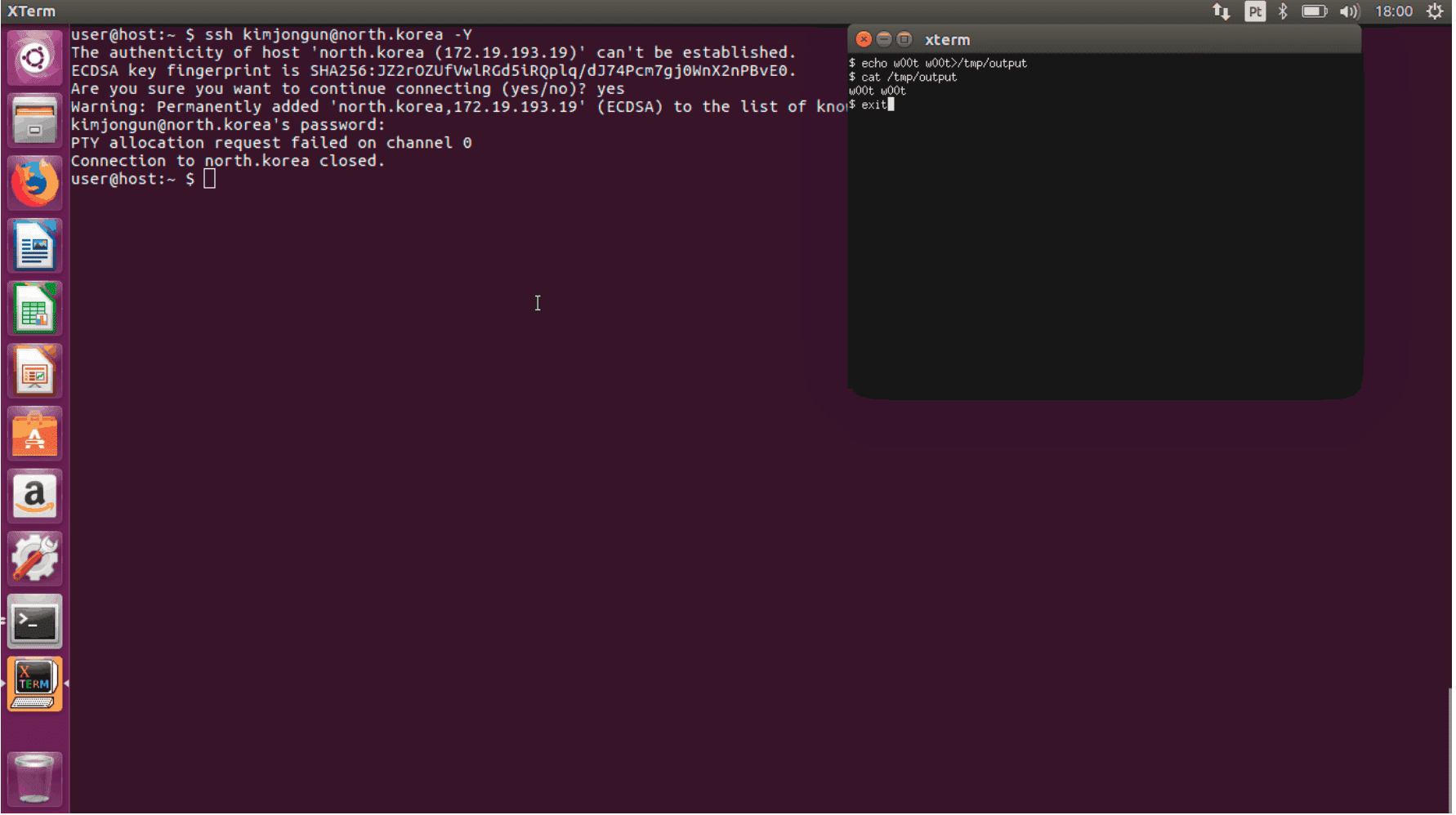
Visual Basic GUI (VBG for short) uses an X11 forwarded SSH session to remotely execute commands on the client.
Motivation
On its usual mode of operation SSH requires the client to be trusted by the server, however, with X11 it’s also necessary that the client trust the server, given that X exposes a lot of features that allow the remote server to open windows, intercept keystrokes, etc. Despite being well known to be dangerous, most people don’t expect to have their machines compromised with an SSH connection.
How?
Trusted X11 forwarding (the -Y option) exposes a lot of X11 extensions to the server and it’s possible to do all sorts of nasty things, like enumerating open windows, recording/injecting keyboard and mouse events, etc. The tool uses wmctrl to detect the client’s windows manager and uses the XTEST extension to inject keystrokes and deliver a payload specific to their environment. It works exactly like it would if running locally, I’ve only added a ForceCommand option inside sshd_config to run the script and exit. It can also read and execute payloads similar to the ones used by Rubber Ducky.
Installation
The setup script will download dependencies, create a new user and configure the SSH daemon to simulate the keystrokes automatically.
Usage
Client
Simply specify -Y when connecting and login like usual: ssh -Y $username@$server_ip
Server
It’s also possible to manually run the script after logging in:
With automatic WM detection and payload selection:
cd /opt/vbg && ./vbg.py -m cmd
With manual payload selection:
cd /opt/vbg && ./vbg.py -m cmd -p payloads/i3_payload
Demo

Source: https://github.com/xfee/





