VLANPWN
VLAN attacks toolkit
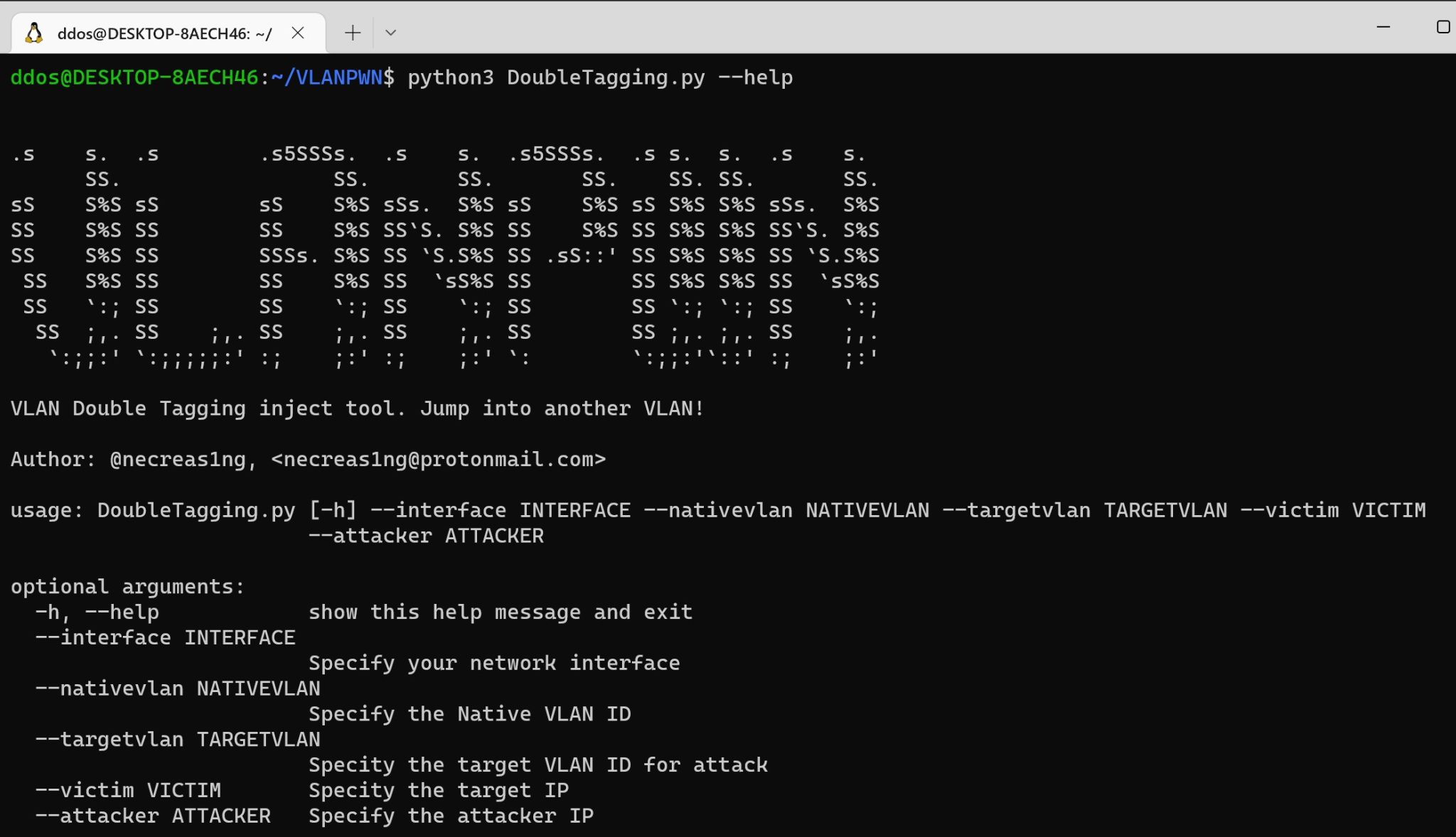
DoubleTagging.py – This tool is designed to carry out a VLAN Hopping attack. VLAN hopping is a computer security exploit, a method of attacking networked resources on a virtual LAN (VLAN). The basic concept behind all VLAN hopping attacks is for an attacking host on a VLAN to gain access to traffic on other VLANs that would normally not be accessible. There are two primary methods of VLAN hopping: switch spoofing and double tagging. Both attack vectors can be mitigated with proper switch port configuration. As a result of the injection of a frame with two 802.1Q tags, a test ICMP request will also be sent.
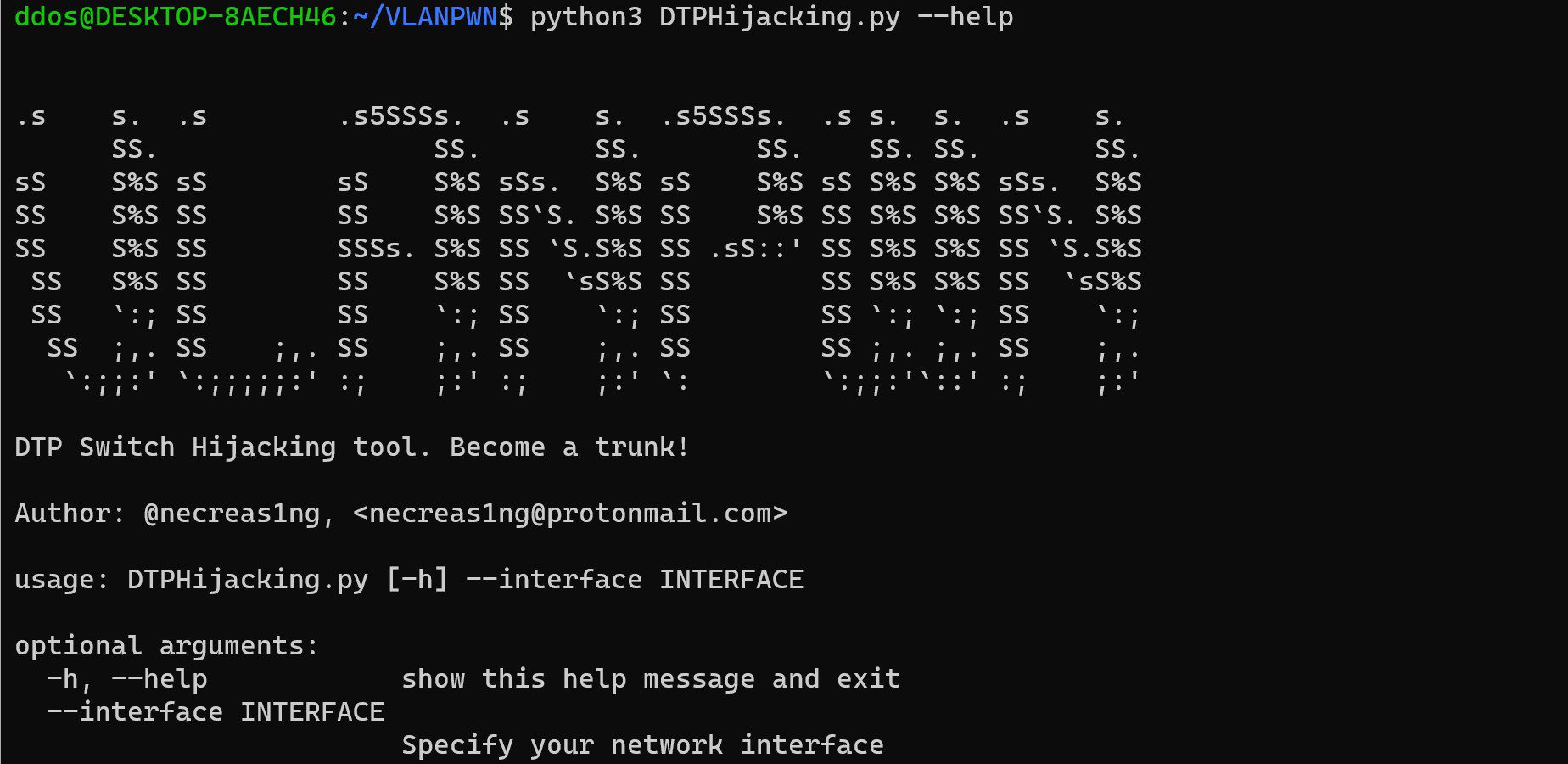
DTPHijacking.py – A script for conducting a DTP Switch Spoofing/Hijacking attack. Sends a malicious DTP-Desirable frame, as a result of which the attacker’s machine becomes a trunk channel. The impact of this attack is that you can bypass the segmentation of VLAN networks and see all the traffic of VLAN networks.
Download
git clone https://github.com/necreas1ng/VLANPWN.git
Use

Example
python3 DTPHijacking.py –interface eth0
Example
python3 DoubleTagging.py –interface eth0 –nativevlan 1 –targetvlan 20 –victim 10.10.20.24 –attacker 10.10.10.54
Source: https://github.com/necreas1ng/