watchdog: A Comprehensive Security Scanning and a Vulnerability Management Tool
Watchog is an integration of open source security tools aimed to provide a holistic security view for a given domain/IP. The way Watchdog is built it can be used by product security teams, red teams and also by bug bounty hunters to get a 360-degree view of an Internet property it scans. Given a list of domains/IP, it has the capability to perform a network scan, feeds the output to open source web app scanners like Google’s skip-fish and wapiti, perform tech stack analysis and determine if the stack has any known CVE’s.

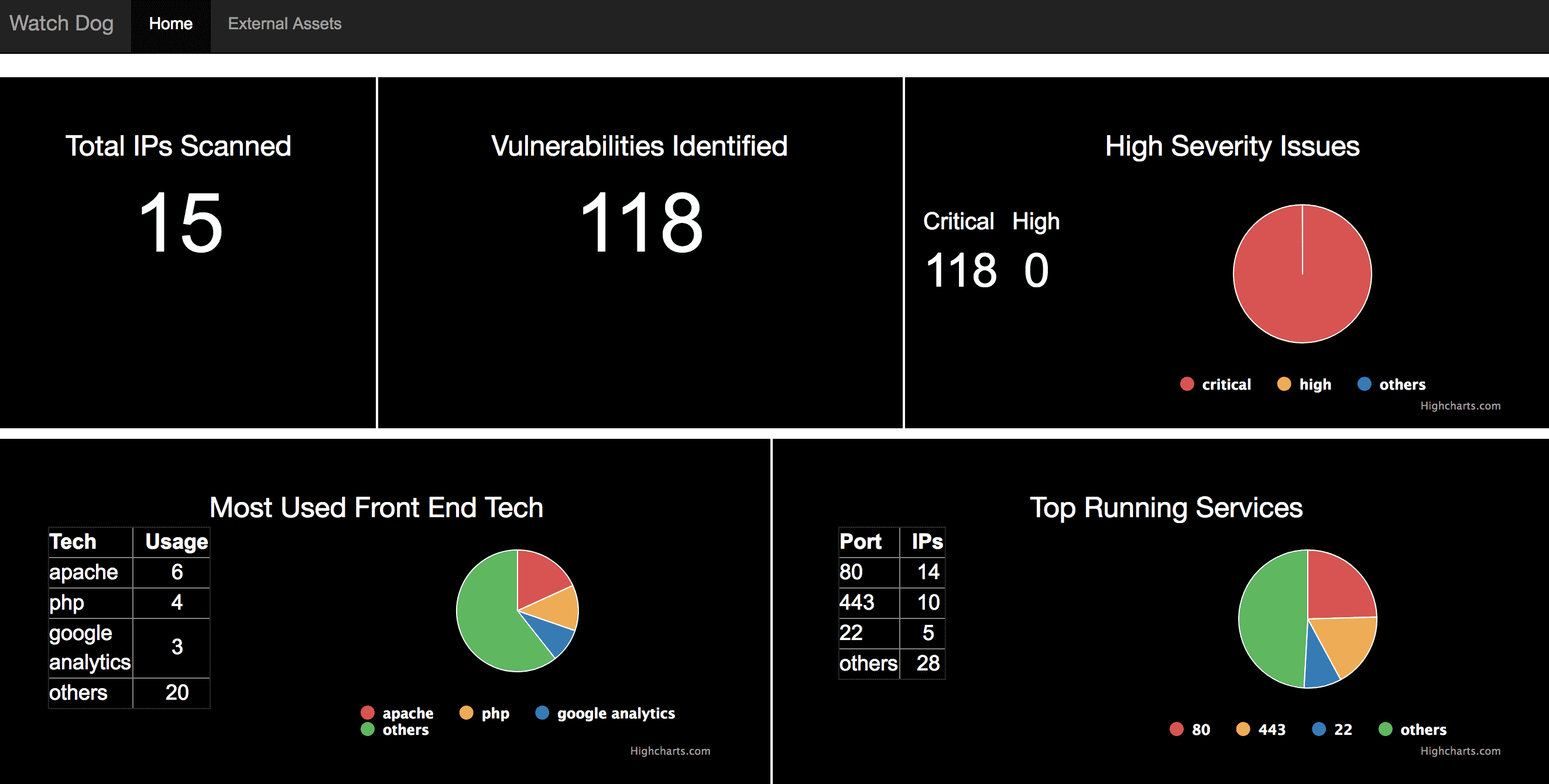
Watchdog is designed considering the use case where it is necessary to know all open services and its corresponding technologies used by the endpoints you own exposed over the Internet. As a company grows it’s foot-prints on the Internet for a product security team it becomes really difficult to maintain an inventory of all the services and technologies which it exposes over the Internet, and in an event of a zero-day outbreak on a particular protocol or a third party product it becomes immensely crucial to know which all endpoints might be affected.
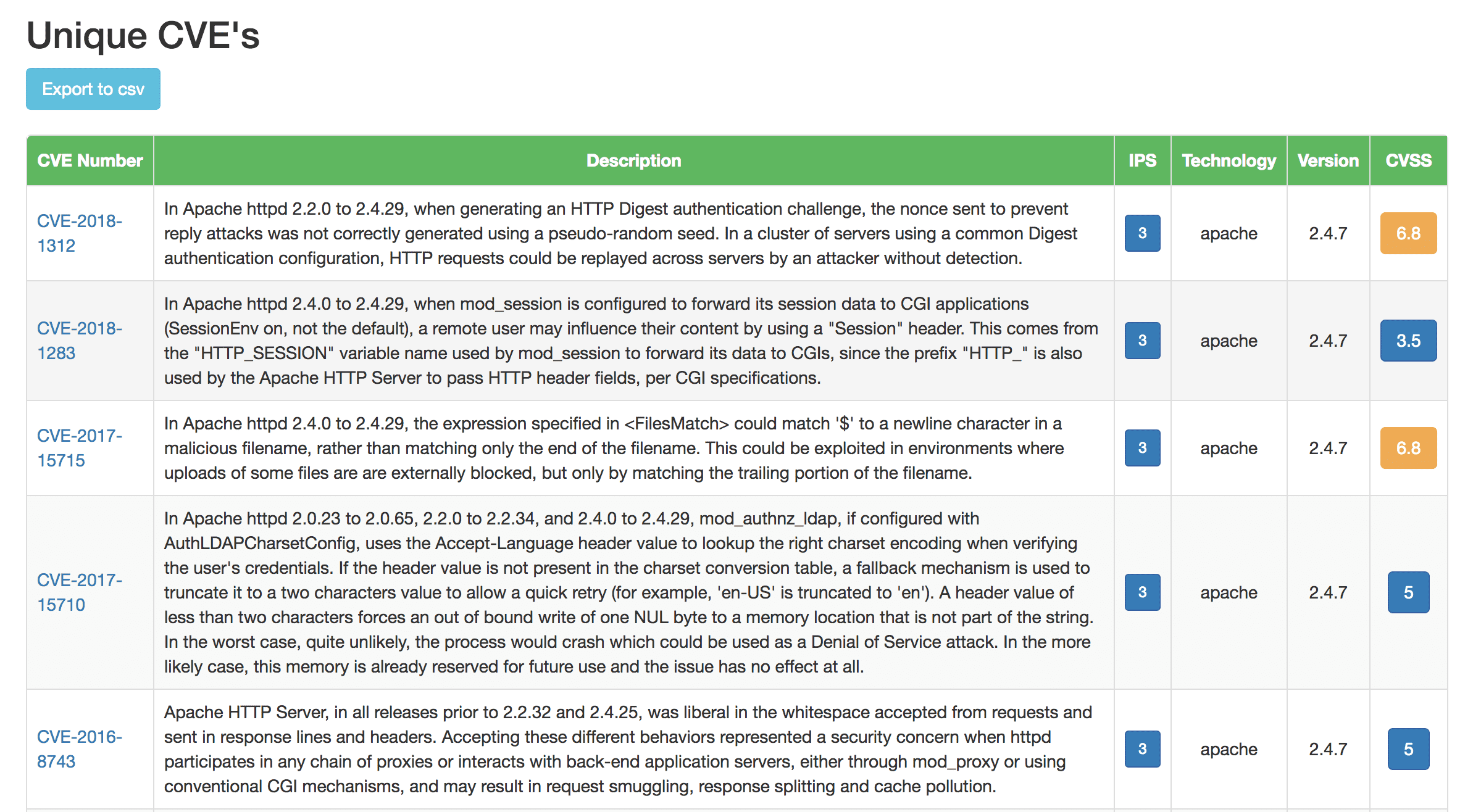
WatchDog has the ability to scan all endpoints and perform technology version analysis on the services it detects and also map this information with its rich CVE database which it maintains and updates locally.
Scan Engine:
- Nmap
- Skipfish
- Wapiti
- BuiltWith
- Phantalyzer
- Wappalyzer
Databases and collections:
Watchdog installs a local copy of CVE database which is a collection of following DB’s :
- cves (Common Vulnerabilities and Exposure items) – source NVD NIST
- cpe (Common Platform Enumeration items) – source NVD NIST
- cwe (Common Weakness Enumeration items) – source NVD NIST
- capec (Common Attack Pattern Enumeration and Classification) – source NVD NIST
- ranking (ranking rules per group) – local cve-search
- d2sec (Exploitation reference from D2 Elliot Web Exploitation Framework) – source d2sec.com
- MITRE Reference Key/Maps – source MITRE reference Key/Maps
- ms – (Microsoft Bulletin (Security Vulnerabilities and Bulletin)) – source Microsoft
- exploitdb (Offensive Security – Exploit Database) – source offensive security
- info (metadata of each collection like last-modified) – local cve-search
- via4 VIA4CVE cross-references.