Image: John Ostrowski
In a revealing security analysis, Compass Security researcher John Ostrowski has disclosed two privilege escalation vulnerabilities in Microsoft Windows—CVE-2025-24076 and CVE-2025-24994—that could allow unprivileged users to gain local system-level privileges using a DLL hijacking attack.
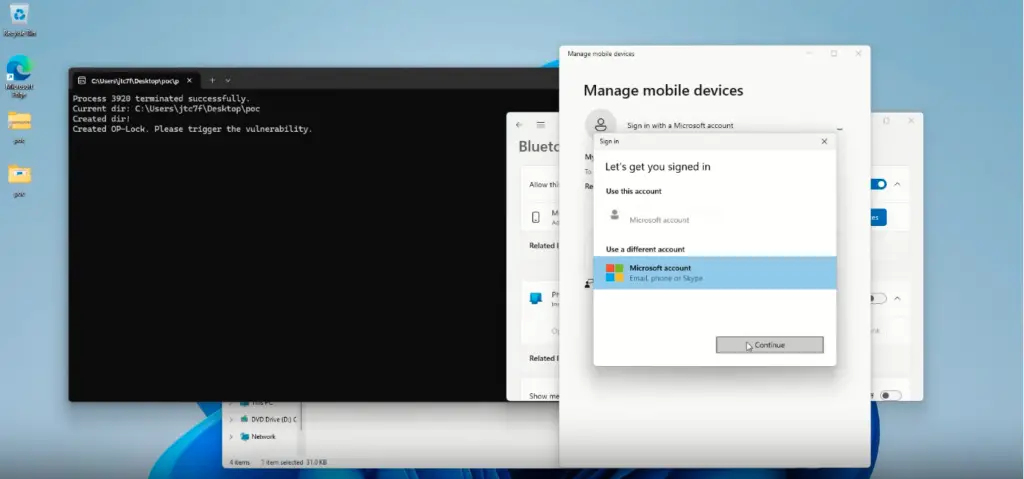
The investigation began with routine checks and automated scans, including the use of PrivescCheck. The tool highlighted a potential privilege escalation vulnerability related to COM server image file permissions. Specifically, it was found that an unprivileged user could potentially modify a DLL file loaded by a COM server running with elevated privileges.
The vulnerability lies within the “Mobile devices” feature in Windows 11, which allows users to link their mobile phones to their Windows computer. The analysis emphasizes that a user-modifiable DLL is loaded by both a regular user and a high-privileged user.
DLL hijacking is a technique that exploits how Windows applications load DLLs. By replacing a legitimate DLL with a malicious one, an attacker can execute arbitrary code with the privileges of the process that loads the DLL. In this case, since a low-privileged user could modify the DLL and it’s then loaded by a high-privileged user, this could be used to gain administrative rights.
The more dangerous of the two flaws, CVE-2025-24076, arises from a system process loading a modifiable DLL without signature validation. As Ostrowski explained:
“Since a normal user can modify the DLL file, and it is then executed by a highly privileged user, we can use this to gain administrative rights on the local machine.”
The researchers faced several challenges in exploiting this vulnerability.
- Timing: There was a very narrow window of approximately 300 milliseconds to replace the legitimate DLL with a malicious one. To address this, they used an Opportunistic Lock to halt the program’s execution while replacing the file.
- File Locking: Windows prevents files from being overwritten while in use. The solution involved intercepting the Close operation within the user application (CrossDeviceService.exe) to ensure the file was not in use before overwriting it. They used Microsoft’s Detours library to intercept the GetFileVersionInfoExW function, allowing them to reliably overwrite the DLL.
Simply replacing the DLL would cause the program to crash. To prevent this, the researchers created a proxy DLL that forwarded function calls to the original DLL while also executing malicious code.
While CVE-2025-24076 enables SYSTEM-level access, CVE-2025-24994 stems from a related user-level process failing to validate DLLs. This opens the door to user-to-user attacks, though its impact is far less severe compared to its SYSTEM-targeting sibling.
The proof of concept involved:
- Triggering the installation of the “Mobile devices” Webcam functionality.
- Waiting for the DLL to be closed.
- Replacing it with a malicious DLL.
This successfully demonstrated how a low-privileged user could gain administrative privileges on a Windows 11 machine.
Microsoft has addressed these vulnerabilities in its March Patch Tuesday.
Related Posts:
- Ubuntu Security Alert: Three Ways to Bypass User Namespace Restrictions
- PoC Released for Linux Kernel Privilege Escalation (CVE-2023-32233) Vulnerability
- Linux kernel privilege escalation vulnerability
- Warning: DLL Hijacking in Modern Malware Campaigns