Zeratool
Automatic Exploit Generation (AEG) and remote flag capture for exploitable CTF problems
This tool uses angr to concolically analyze binaries by hooking printf and looking for unconstrained paths. These program states are then weaponized for remote code execution through pwntools and a series of script tricks. Finally, the payload is tested locally then submitted to a remote CTF server to recover the flag.
Exploit Types
Zeratool is designed around weaponizing buffer overflows and format string vulnerabilities and currently supports a couple types:
- Buffer Overflow
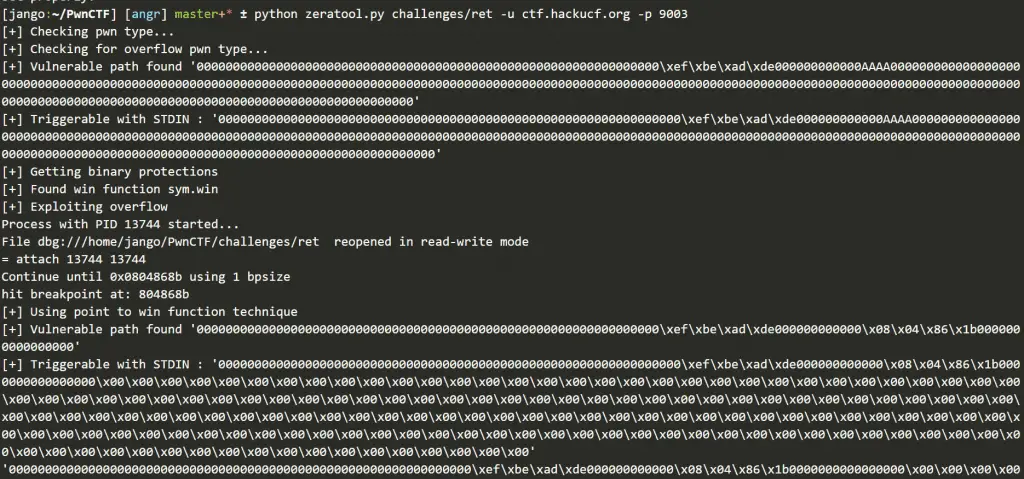
- Point program counter to win function
- Point program counter to shellcode
- Point program counter to rop chain
- Rop chains need a libc base address
- one-gadget and ropper are used rop chain building
- Format String
- Point GOT entry to win function
- Point GOT entry to shellcode
It has room to grow and future iterations of Zeratool will include information disclosure discovery and link those leaks to an offset for general ASLR bypasses.
Changelog v2.2
Zeratool now supports remote libc leaking with buffer overflows. When a puts or printf call is present, Zeratool will leak out remote GOT entries and submit them to an online libc searching database to find offsets without the need for a local copy of the library.
See remote libc leak in action!
Zeratool supports some basic ret2dlresolve chaining for 64bit binaries. See the example below on how to run it.
Installing
https://github.com/ChrisTheCoolHut/Zeratool.git ./install.sh
Usage
Zeratool is a python script which accepts a binary as an argument and optionally a linked libc library, and a CTF Server connection information
Demo
Copyright (C) 2018 Christopher Roberts
Source: https://github.com/ChrisTheCoolHut/
