
A new wave of cyberattacks linked to the Blind Eagle (APT-C-36) group has been uncovered by Check Point Research (CPR), targeting Colombian institutions and government entities. Since November 2024, this Advanced Persistent Threat (APT) group has exploited a sophisticated attack chain involving malicious .url files that mimic the behavior of CVE-2024-43451, a vulnerability exposing NTLMv2 hashes. While Blind Eagle’s malicious files do not directly exploit this vulnerability, they trigger similar WebDAV requests, enabling cybercriminals to track infected users and deliver malware payloads.
Blind Eagle has been active since 2018, focusing on espionage and cybercrime against public and private organizations in Latin America. The group’s modus operandi relies on well-crafted phishing campaigns designed to deceive victims into executing Remote Access Trojans (RATs) such as Remcos RAT, NjRAT, and AsyncRAT.
According to CPR, the latest attacks indicate Blind Eagle’s rapid adaptability: “Microsoft patched the original vulnerability on November 12, 2024. Just six days later, Blind Eagle included this .url variant in its attack arsenal and campaigns.” The group’s ability to integrate new tactics within days highlights its advanced capabilities and the ongoing challenge of defending against such adversaries.
The attack methodology observed in these campaigns includes:
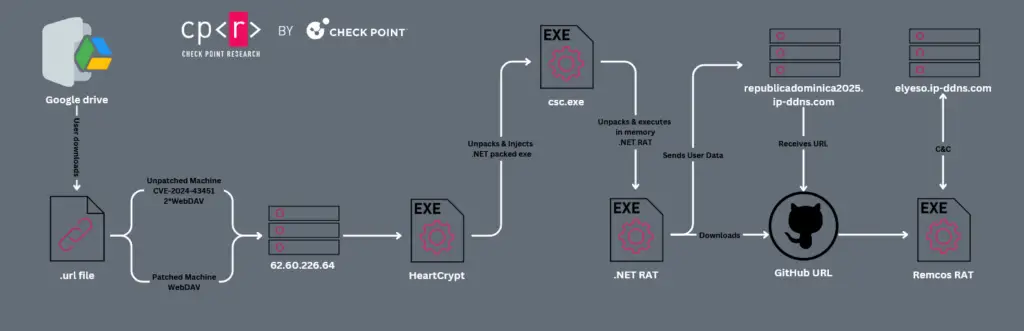
- Weaponized .url Files: Blind Eagle delivers malicious .url files via phishing emails, often disguised as legitimate communications from Colombian judicial institutions.
- Initial WebDAV Request: When a victim downloads or interacts with the file, a WebDAV request is triggered, notifying the attackers.
- Next-Stage Payload Execution: Clicking on the file downloads and executes malware via another WebDAV request, leading to full system compromise.
- Malware Deployment: The final payload is typically Remcos RAT, which enables Blind Eagle to gain persistent access, exfiltrate data, and execute further malicious activities.
“More than 1,600 victims were affected during one of these campaigns which took place around December 19, 2024,” the report states. This scale of infection, despite Blind Eagle’s targeted approach, underscores the effectiveness of its phishing techniques.
The group strategically delivers its malware using trusted cloud storage services. While previous campaigns leveraged Google Drive and Dropbox, recent attacks have also utilized Bitbucket and GitHub to distribute payloads. The use of widely trusted platforms allows the group to evade detection and bypass traditional security filters.
To further obscure its activities, Blind Eagle uses HeartCrypt, a Packer-as-a-Service (PaaS) that protects its malware binaries. According to CPR, “Blind Eagle leverages the Packer-as-a-Service HeartCrypt, which employs a .NET RAT that appears to be a variant of PureCrypter. The final stage payload is Remcos RAT.” This approach enhances stealth, making detection and mitigation significantly more challenging.
The group’s tactics extend beyond malware deployment. A March 2024 phishing campaign, labeled Operation Fail (OPFail), impersonated Colombian banks and successfully harvested over 8,000 personally identifiable information (PII) records. Among the stolen data were:
- Usernames
- Passwords
- Email credentials
- ATM PINs
Some of these records belonged to Colombian government officials and law enforcement agencies, raising concerns about potential state-level espionage.
While Blind Eagle’s exact origin remains unclear, CPR’s research provides strong evidence suggesting a South American base of operations. The report states: “We identified the group’s operating timezone as UTC-5, which aligns with several South American countries.” This finding reinforces longstanding suspicions about the group’s regional affiliations.
Related Posts:
- BlindEagle APT Targets Colombian Insurance with BlotchyQuasar RAT
- eSentire vs. Phantom: Unveiling the Cyber Spook’s Dance of Darkness
- Outdated and Unblocked: Legacy Driver Vulnerability Exploited in Widespread Attack