
A recent report by Trend Micro has uncovered a stealthy, state-sponsored backdoor called BPFDoor, which has been linked to cyberespionage activities across Asia and the Middle East. The investigation, which unearthed a previously unknown controller, attributes this malicious tool to Red Menshen, an advanced persistent threat (APT) group also known as Earth Bluecrow.
BPFDoor is a sophisticated malware notable for its stealth capabilities, many of which are tied to its use of Berkeley Packet Filtering (BPF), a technology that allows code execution within the operating system’s kernel virtual machine. By leveraging BPF’s packet filtering features, BPFDoor can inspect network packets at a very low level, enabling it to be activated by specific “magic sequences” within those packets. This method allows the backdoor to evade security measures, including firewalls, as the malicious packet triggers the backdoor before the firewall has a chance to block it.
Trend Micro’s most critical discovery centers on a versatile and stealthy controller—a tool used by Earth Bluecrow to interact with infected machines using TCP, UDP, and ICMP. The controller is capable of:
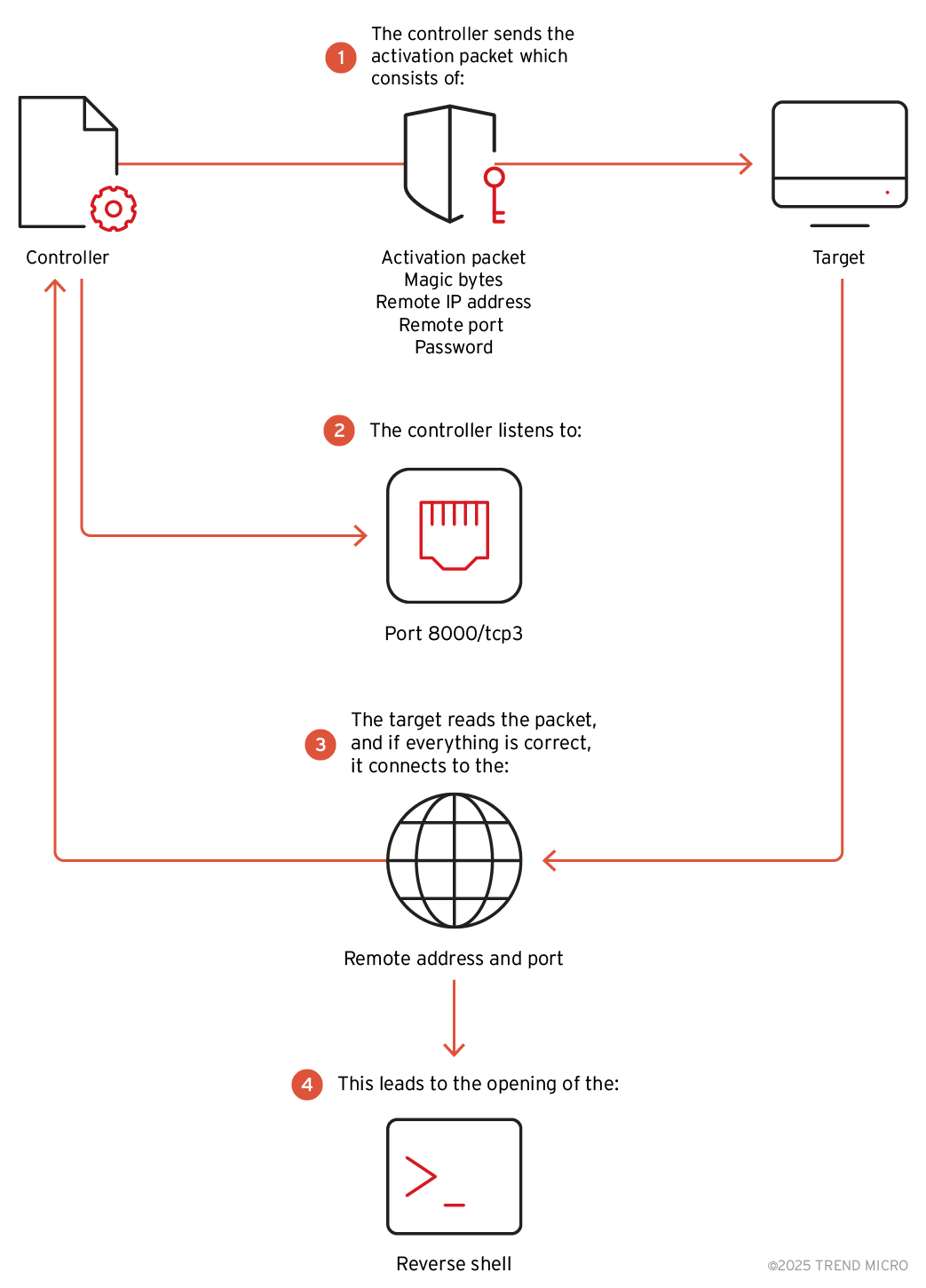
- Opening reverse shells
- Listening on arbitrary ports
- Issuing stealthy connection requests using ‘magic sequences’
- Verifying backdoor presence with or without passwords
This controller relies on password-authenticated sessions. Upon receiving a custom packet containing a password and magic bytes, the target responds by opening a reverse shell or redirecting traffic—depending on the attacker’s chosen command.
“The password sent by the controller must match one of the hard-coded values in the BPFDoor sample… the malware prefixes the clear-text password with a fixed salt, calculates its MD5 hash, and compares it with the hard-coded values,” Trend Micro explains.
Trend telemetry shows that BPFDoor has been active since at least 2021, with sustained campaigns through 2024 targeting:
- Telecommunications (South Korea, Hong Kong, Myanmar)
- Financial Services (Egypt)
- Retail (Malaysia)
The attackers typically compromise Linux servers, hiding malware in non-standard paths such as /tmp/zabbix_agent.log or /bin/vmtoolsdsrv.
Because magic packets can be customized and passwords vary per sample, defenders cannot rely on static indicators. However, network defenders can watch for:
- TCP packets starting with 0x5293 followed by IP:port and password
- UDP/ICMP packets with similar magic values
- Suspicious outbound TCP connections containing “3458” in payloads
BPFDoor exemplifies how BPF technology is being weaponized by advanced adversaries. Though long associated with packet filtering and observability, its exploitation in rootkit-like backdoors signals a new threat frontier.
“BPF opens a new window of unexplored possibilities for malware authors… this requires deeper research and constant vigilance to gain more insight into attacks launched in other environments,” Trend Micro warns.
Related Posts:
- PoC Exploit Releases for CVE-2023-52447: A Linux Kernel Flaw Enabling Container Escape
- Google’s SynthID Now in Magic Editor: AI Image Detection