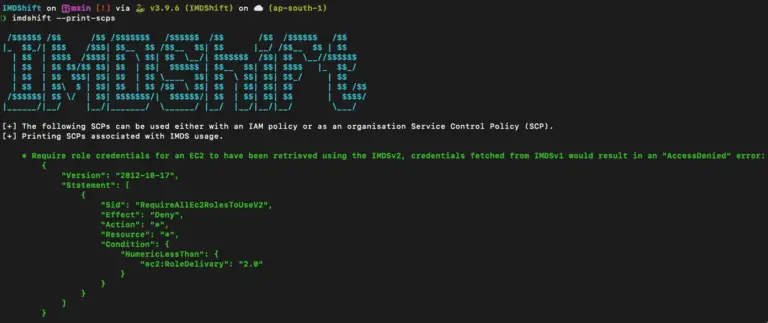
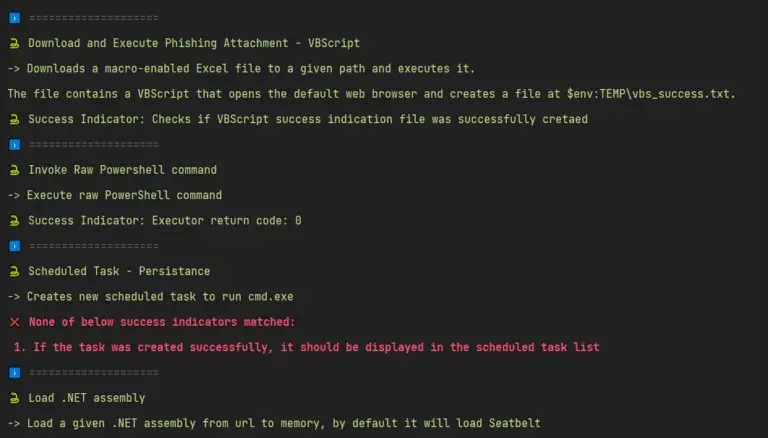
IMDShift AWS workloads that rely on the metadata endpoint are vulnerable to Server-Side Request Forgery (SSRF) attacks....
Defense
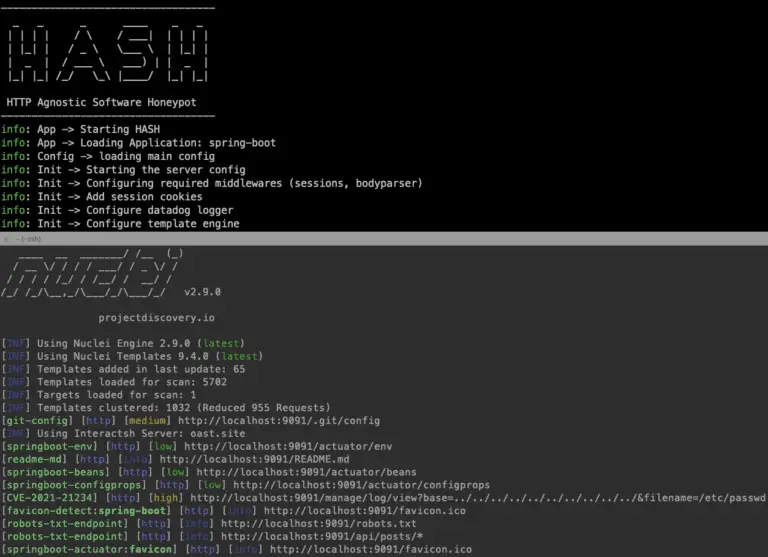
HASH (HTTP Agnostic Software Honeypot) HASH is a framework for creating and launching low interactive honeypots. Why...
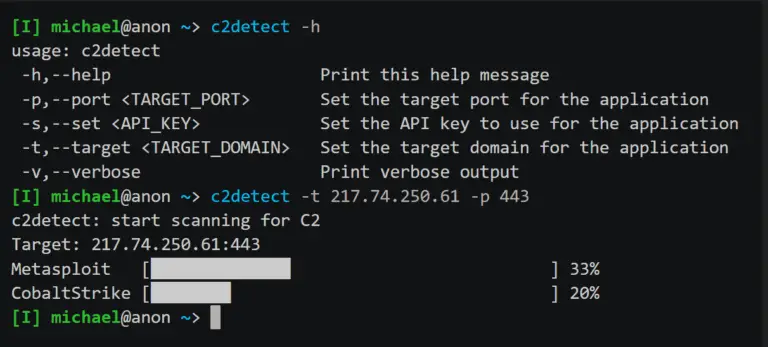
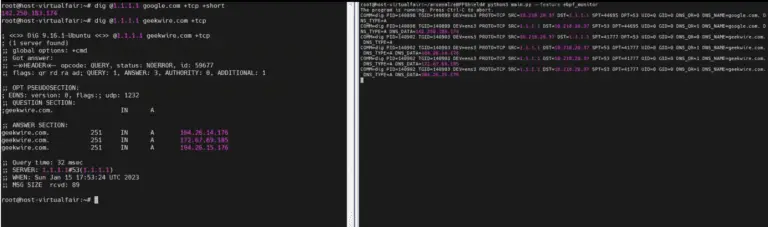
NetAtlas C2 Server Search C2 Search Netlas is a Java utility designed to detect Command and Control...
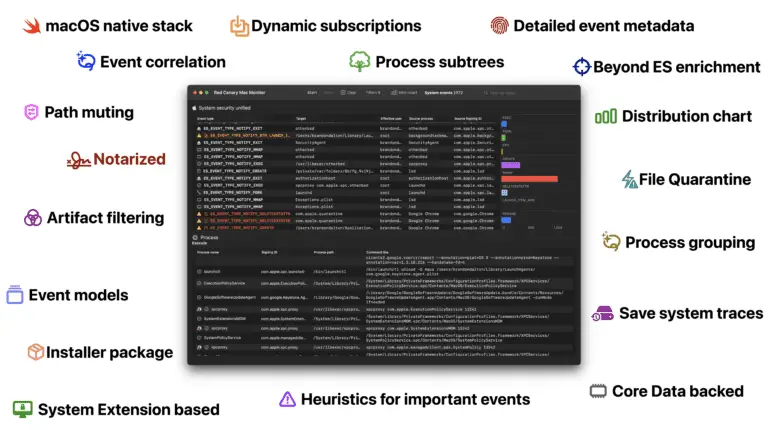
Red Canary Mac Monitor Red Canary Mac Monitor is an advanced, stand-alone system monitoring tool tailor-made for macOS...
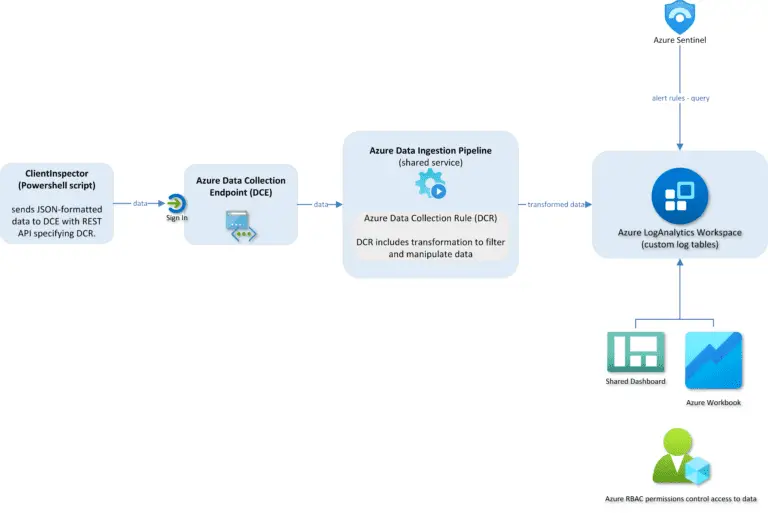
ClientInspector Are you in control? – or are some of your core infrastructure processes like patching, antivirus, and bitlocker...
eBPFShield Welcome to eBPFShield, a powerful and intuitive security tool for monitoring and protecting your servers. Featuring...
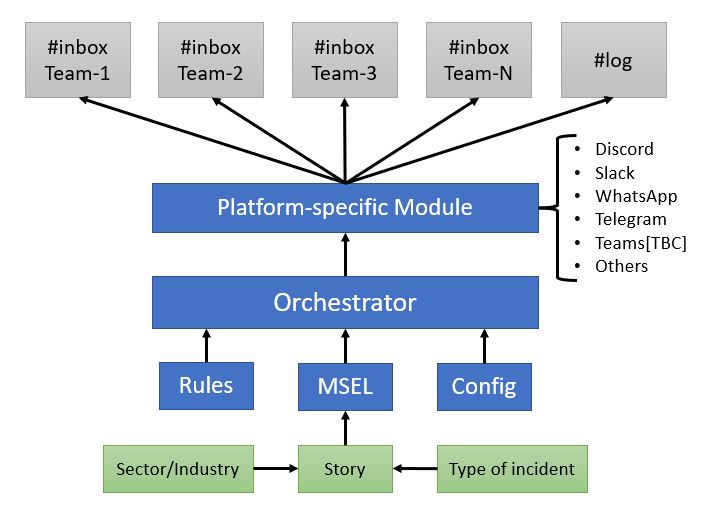
T3SF – Technical Tabletop Exercises Simulation Framework T3SF is a framework that offers a modular structure for...
SecuSphere Welcome to SecuSphere, your one-stop solution for all DevSecOps needs. Our centralized platform is expertly designed...
CureIAM Clean up of over permissioned IAM accounts on GCP infra in an automated way CureIAM is...
cymulate-framework The framework to automate Cymulate’s modules and templates for the purple team. What is Cymulate? Cymualte is...
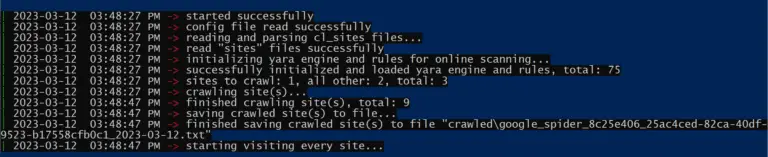
Crawlector Crawlector (the name Crawlector is a combination of Crawler & Detector) is a threat hunting framework designed for scanning...
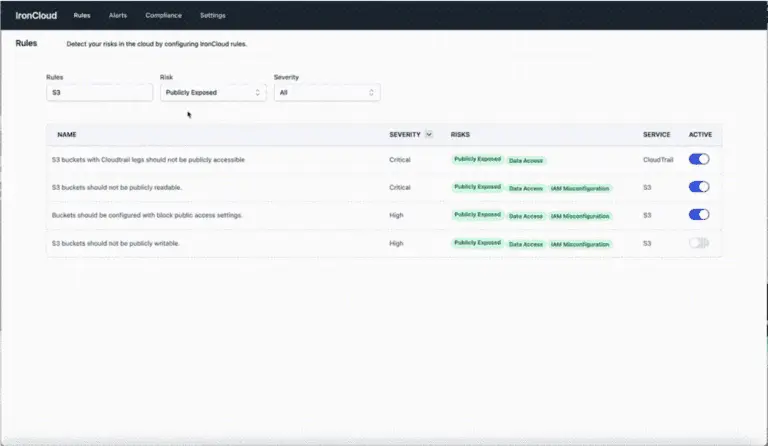
ZeusCloud is an open-source cloud security platform. Discover, prioritize, and remediate your risks in the cloud. Build...
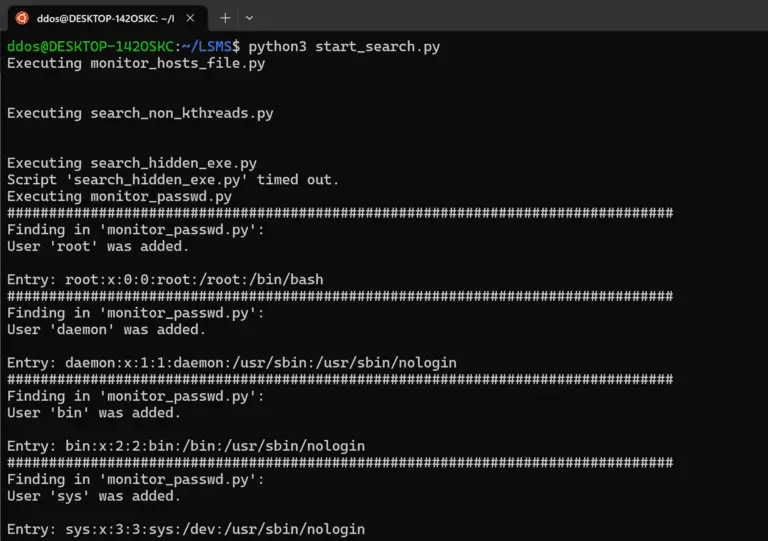
Linux Security and Monitoring Scripts These are a collection of security and monitoring scripts you can use...
Gato (Github Attack TOolkit) Gato, or GitHub Attack Toolkit, is an enumeration and attack tool that allows...
aerleon Generate firewall configs for multiple firewall platforms from a single platform-agnostic configuration language through a command...